Fundamentals of Digital Forensics
5. Identification and analysis of information in Operating Systems
5.2. Windows Registry Analysis
Windows registry analysis can be performed using forensic software, such as AccessData Registry Viewer, Eric Zimmerman’s tools, RegRipper, or even any other software capable of extracting data from these registry files.
Due to the complexity of the Windows registry, identifying the location of each relevant piece of information can be a daunting task, however, we have enlisted the help of SANS FOR500 (https://digital-forensics.sans.org/docs/DFPS_FOR500_v4.11_0121.pdf), identifying many of the important locations where relevant information can be found.
There may be a need to extract the log from a connected computer, the log being a huge source of forensically relevant information, it will be imperative to obtain all that information. (Read: https://resources.infosecinstitute.com/windows-registry-analysis-regripper-hands-case-study-2/). There are several ways to perform the registry dump, here we will focus on some different ways.
5.2.1. The Time Zone
The first information to be analysed should include the Time Zone (Figure 57), as this may lead us to make mistakes when faced with actions that present a date/time different from the true one, simply because the system is configured with a time zone different from the one that the forensic analyst is using.
This information can be identified in hive SYSTEM, at the following location :
SYSTEM\ControlSet001\Control\TimeZoneInformation
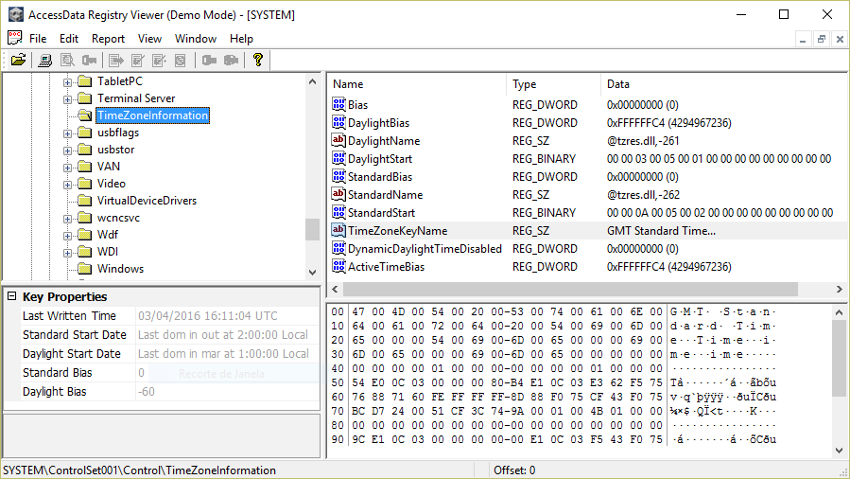
Figure 57 – TimeZone in AccessData Registry Viewerr
5.2.2. USB devices
In the registry it is also possible to obtain information from USB devices that have connected to the system in the hive SYSTEM:
To obtain: Producer / Brand / serial no. / date / time of first and last connection to the system
HKLM\SYSTEM\CurrentControlSet\Enum\USBSTOR
HKLM\SYSTEM\CurrentControlSet\Enum\USB
By viewing (Figure 58).
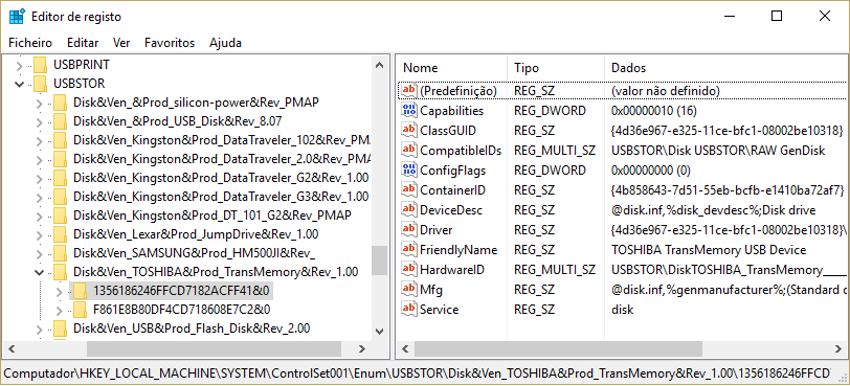
Figure 58 - Viewing USB devices in the Registry Editor
To get the letter assigned to the USB device
HKLM\SYSTEM\MountedDevices
To get the user who connected the device to the system
NTUSER.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2
The same information can be obtained by using specific tools to obtain information from USB devices, such as the 4Discovery or USBDeview tools(Figura 59).
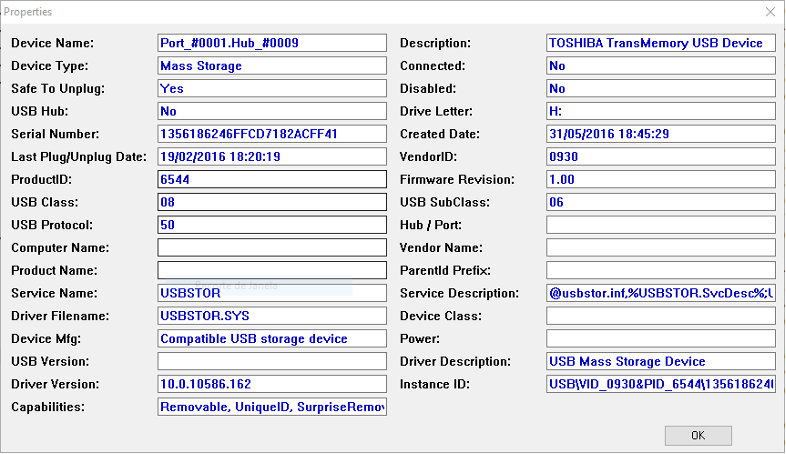
Figure 59 – Viewing USB devices in USBDeview
Read:https://www.researchgate.net/publication/318514858_USB_Storage_Device_Forensics_for_Windows_10
5.2.3. Users
The information about the system users is stored in the Windows registry in the SAM hive, but there is also the NTUSER.DAT registry file for each user, which stores data specific to that user:
List of local user profiles
In the registry: HKLM\Software\Microsoft\Windows NT\CurrentVersion\ProfileList
System users
In the file: SAM\SAM\Domains\Account\Users\
Viewing this registry key through the Registry Editor, you can see how this information is displayed (Figure 60).
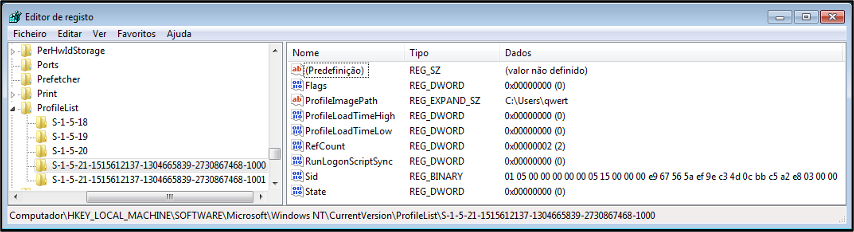
Figure 60 – Viewing users in the registry editor
The same information can be obtained with specific tools to obtain users’ information, such as the AccessData Registry Viewer (Figure 61).
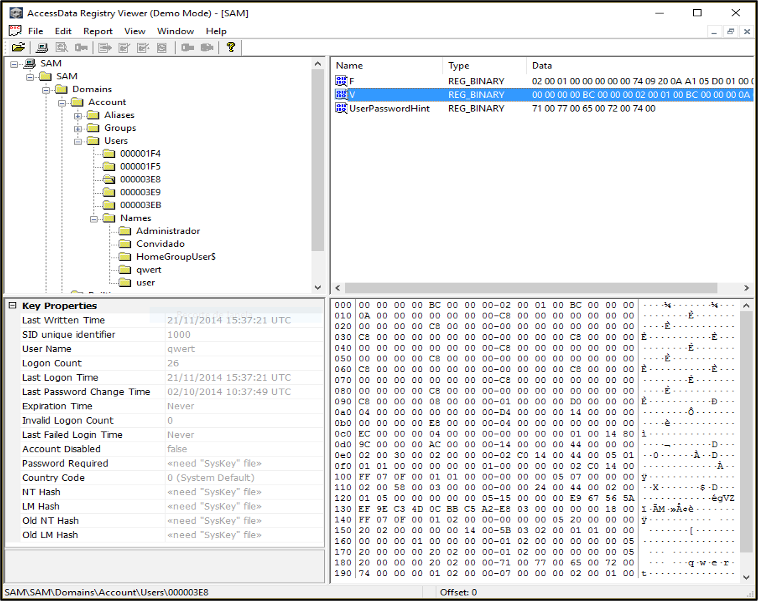
Figure 61 – Viewing users in AccessData Registry Viewer
5.2.4. Network
The log also contains various network information, such as the wireless networks the system has connected to:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\NetworkList\
In this location it is possible to identify:
• Network name (SSID)
• Name of the domain / intranet
• Date/time of last connection (through the date/time that the respective key was written)
• Gateway MAC address
5.2.5. Windows Registry Analysis - RegRipper
Regarding Windows registry analysis, there are many forensic tools that we can use to facilitate the analysis of information contained in the Windows registry. We focus here on some free tools such as RegRipper, RegistryReport and Windows Registry Recovery.
RegRipper (http://github.com/keydet89) is an Open Source Forensic application, developed by Harlan Carvey and written in PERL, with the objective of extracting information from Windows Registry files in a readable way.
RegRipper (Figure 62) can be used through the command line and a graphic interface to extract specific information from each registry file. When using the command line it is possible to select the plugin to be applied to each registry hive, whereas in the case of the command line all the plugins available for the selected hive are applied. The result of the extracted information may be displayed on screen or saved in a text file, in the case of using the command line. Through its graphical interface it will be necessary to indicate the output location, called Report File, to create the text file with the result of all plugins applied to the respective registry hive..
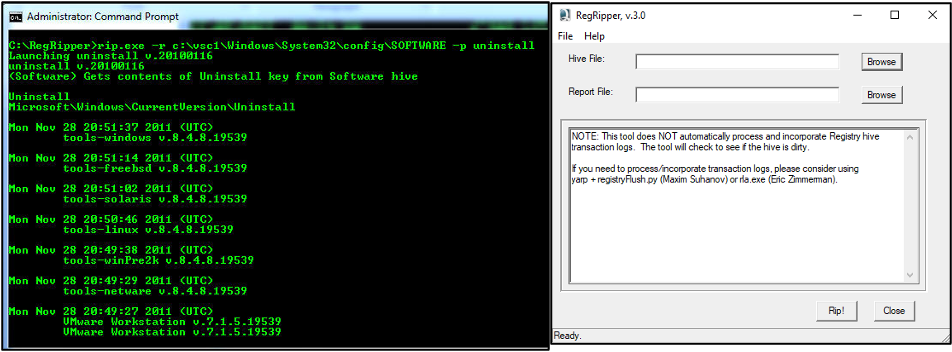
Figure 62 – Usage of RegRipper
Through the command line it is possible to check the available plugins to apply through the argument “-l -c”.
C:\RegRipper3.0-master>rip -l -c > c:\list.csv
In GUI mode (Figure 63), it is not possible for us to choose a single plugin, but the Hive that we want to analyse.
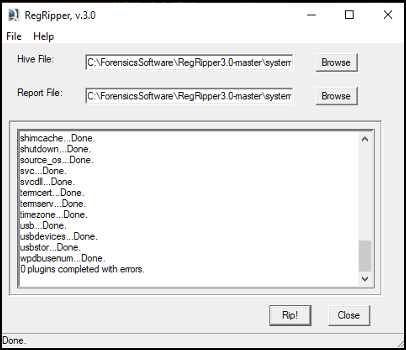
Figure 63 - Using the RegRipper GUI
Output file (Figure 64)
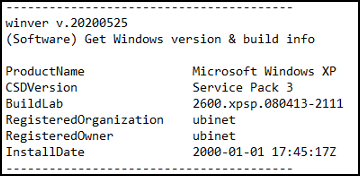
Figure 64 – RegRipper output file
There are other forensic applications with the same objective of interpreting the contents of registry files, such as Registry Report and Windows Registry Recovery.
RegistryReport
Like RegRipper, Gaijin Registry Repport also presents the registry information in an easily readable and searchable way. It works simply, allowing you to select the information you want to retrieve from the registry via checkboxes, as shown in Figure 65.
Source: https://gaijin.at/en/files?dir=old-software registryreport
https://github.com/jschicht?tab=repositories
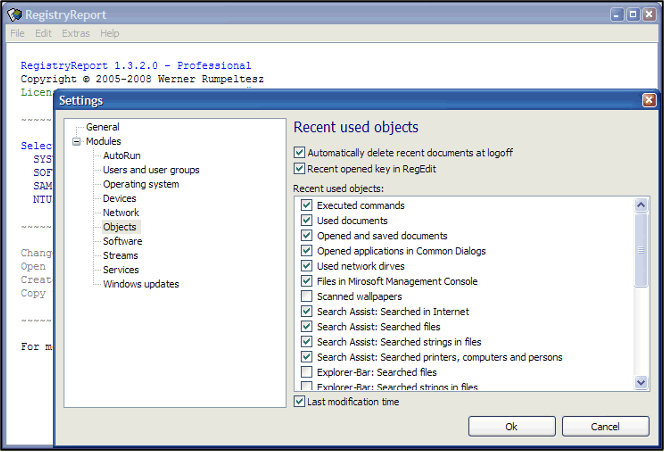
Figure 65 – Usage of RegistryReport
Source: https://www.gaijin.at/en/files?dir=old-software&sort=N&order=A registryreport
Windows Registry Recovery
WRR (Figure 66) is one of the applications we can use for Windows registry analysis

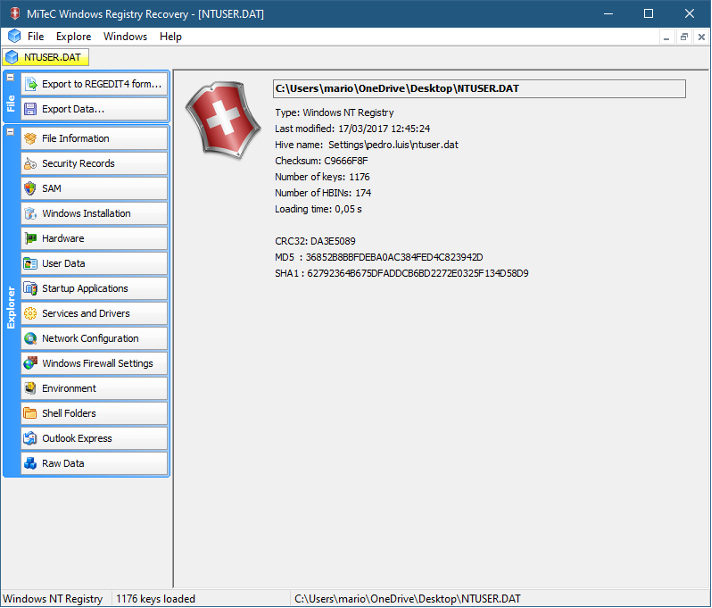
Figure 66 – Using MiTeC Windows Registry Recovery
Source: http://www.mitec.cz/wrr.html
