Fundamentals of Digital Forensics
5. Identification and analysis of information in Operating Systems
5.1. MS Windows Registry
“A central hierarchical database in Windows … used to store information necessary to configure the system for one or more users, applications, and hardware devices. The Registry contains information that Windows continually references during operation, such as profiles for each user, the applications installed on the computer and the types of documents each can create, property sheet settings for folders and application icons, what hardware exists on the system, and which ports are being used.”
Source: Microsoft Computer Dictionary.--5th ed., Redmond, Washington, Microsoft Press, 2002, p. 445
It is therefore possible to state that the Windows registry, despite its structuring files, contains a logical structure in constant use by the operating system, storing a set of information necessary for its operation.
The logical structure of the Windows registry contains:
- Registry keys, keys named “Software” and “System”, belonging to the hive “HKEY_CURRENT_CONFIG”.
- Registry sub-keys, where registry information is stored (e.g.: “Fonts” sub-key).
- Registry values, which contain the information by specifying their type in the respective column (e.g.: REG_DWORD - 32-bit binary value, REG_QWORD – 64-bit binary value).
The five main Hives in the logical structure of the MS Windows operating system can be seen in Figure 52.
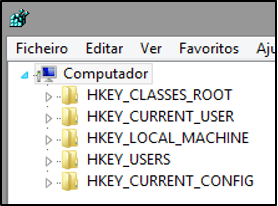
Figure 52 - Root Hive
Hive of the registry (Root Keys) are characterized by the prefix “HKEY_”, short for “Handle to a KEY”.
There are 5 main hives, stored in the various files that make up the registry, although only HKEY_USERS and HKEY_LOCAL_MACHINE are considered the true hives, the rest being shortcuts or aliases for branches within them.
|
Hive |
Abbreviation |
Description |
Link |
|
HKEY_CURRENT_USER |
HKCU |
Points to the user profile of the currently loggedon user |
Subkey under HKEY_USERS corresponding to currently loggedon user |
|
HKEY_USERS |
HKU |
Contains subkeys for all loaded user profiles |
Not a link |
|
HKEY_CLASSES_ROOT |
HKCR |
Contains file association and COM registration information |
Not a direct link; rather, a merged view of HKLM\SOFTWARE\Classes and HKEY_CURRENT_USER\SOFTWARE\Classes |
|
HKEY_LOCAL_MACHINE |
HKLM |
Global settings for the machine. |
Not a link |
|
HKEY_CURRENT_CONFIG |
HKCC |
Current hardware profile |
HKLM\SYSTEM\CurrentControlSet\Hardware Profiles\Current |
|
HKEY_PERFORMANCE_DATA |
HKPD |
Performance counters |
Not a link |
Source: Windows Internals.--6th ed., Part 1,
Redmond, Washington, Microsoft Press,
2012, p. 281
The log files are located in the following folders:
Operating system log files
C:\Windows\System32\Config\
Registry files for each user
C:\Users\<username>\ntuser.dat
5.1.1. Registry editor (RegEdit)
The registry editor, in its graphical version, allows the export of one or more registry keys (Figure 53).
RegEdit, File > Export
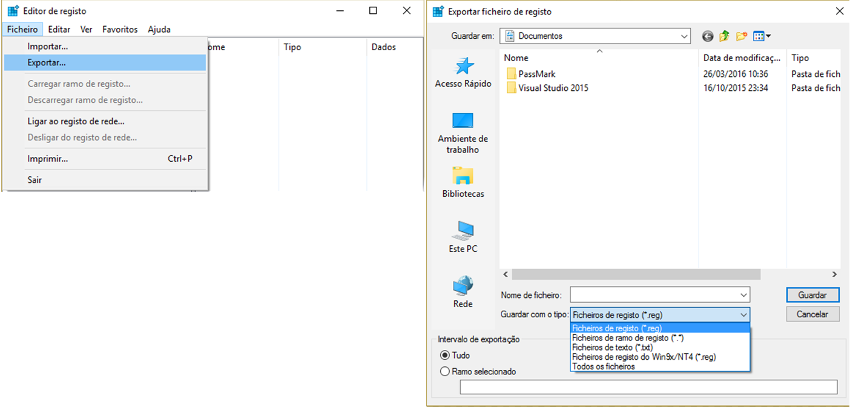
Figure 53 – Registry Export through RegEdit
Via the command line:
regedit /e c:\output.reg "HKEY_LOCAL_MACHINE\System\..."
5.1.2. ERUNTgui
The application ERUNTgui (Figure 54), allows the backup, restoration and optimization of the registry, being of forensic interest the possibility of performing the backup of the registry, thus enabling its subsequent analysis.
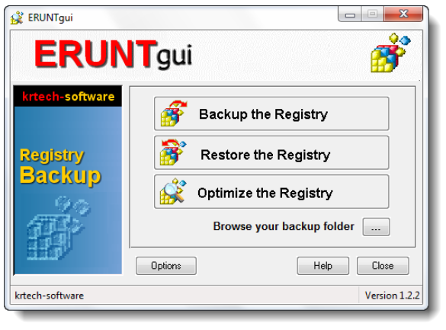
Figure 54 – Registry Export through ERUNTgui
5.1.3. RAWCopy
The RAWCopy application (Figure 55), allows copying the sectors of the disk where the files in use are, thus overcoming the limitation of copying files opened by the system.
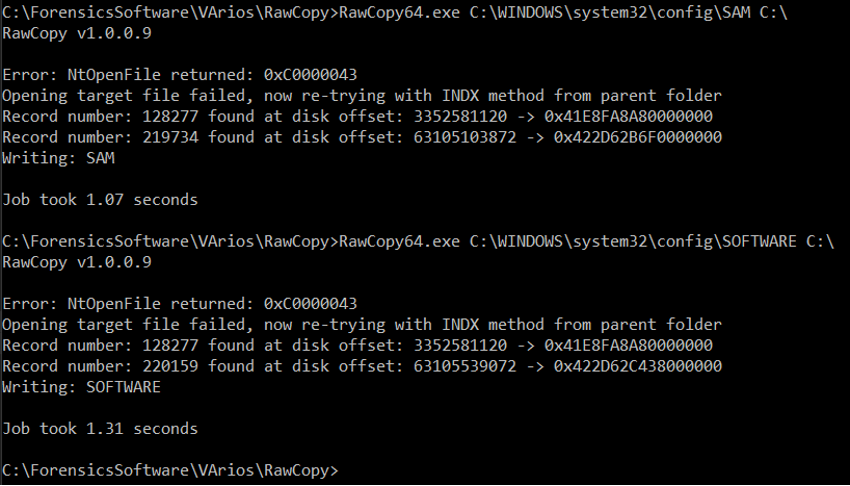
Figure 55 – Registry Export through RAWCopy
Through RAWCopy it was possible to obtain a copy of the SAM and SOFTWARE file with the system running (Figure 56).
Figure 56 – Files exported by RAWCopy
Source: https://github.com/jschicht/RawCopy
