Fundamentals of Digital Forensics
4. Acquisition and analysis of volatile information
4.1. Process of capturing volatile information
First of all it is necessary to ensure the stability of our working machine. One of the problems that can be experienced is the automatic restart of the machine, caused by automatic updates of the operating system. It is therefore advisable to deactivate, not the operating system updates, but their ability to force a restart of the machine. This restart could, for example, interrupt a disk acquisition or an image analysis.
Another good practice is to deny write access to removable disks, thus preventing the source disks from being altered.
A volatile data is any data that can be lost when the system is shut down, such as a record of a connection to a website that is still present in RAM or the system clipboard. The collection of this data must occur while the system is running.
Live-Data Forensics, is the technique used to collect data that is volatile and can be lost if the device loses power.
Memory DUMP is the procedure of storing in a file, all data present at a given moment in the physical memory of the computer.
When collecting this type of data, it is necessary to take into account the order of volatility of the data, adapting the collection to the category of data that is of most interest. If our goal is to identify the sending of an email to a certain address, it would not make much sense to give priority to the identification of processes instead of collecting passwords, or access credentials, that allow access to the email address.
It is very important that live data collection is properly documented, preferable by creating a collection team of at least two people, to ensure that the collection procedures are carried out by one person while the other documents the collection process used.
It is also important to guarantee the minimum alteration to the system to be analysed and if any alteration needs to be made, it should be registered in a report for future memory.
Recommendations on the use of scripts:
· Use of environment variables
(ex.: cmd: %COMPUTERNAME% / PS: $env:Computername)
· Running in Administrator mode
4.1.1. Native System Tools
Considering the minimal digital footprint on the device, we should whenever possible use forensic tools to collect useful information that allows a more efficient analysis. An example of this is information related to full-disk encryption. However, the MS Windows operating system allows the execution of commands and scripts with native tools, being an excellent possibility to obtain the necessary information with a minimal digital footprint.
As recourse is made to external tools, care must be taken to thoroughly test each of these tools in order to know exactly what they do in the system. Any external tools used, the date/time of use should be noted, as well as describing the intention of use.
4.1.3. Date, Time and other System informations
This element should be the first to be collected when performing an investigation. The system date makes it possible to contextualise the information collected later and allows the researcher to build a timeline of events that have occurred, not only in the system under analysis, but through correlation between information from other systems. Another important piece of data is the time elapsed since the last boot (uptime).
Some tools can help researchers in these tasks, such as MiTeC - System Information X[1] and WinAudit[2].
Collection of the date/time of the system being serviced (Figure 32).
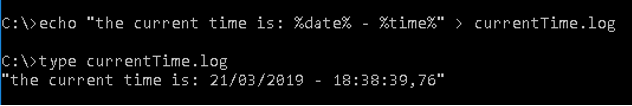
Figure 32 – Obtaining the system’s date and time.
Collecting the date/time of the last system start-up (Figure 33).
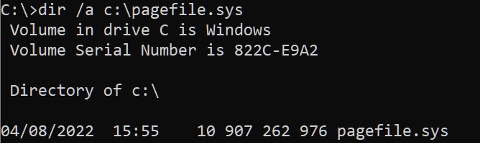
Figure 33 – Obtaining the date and time of the last system boot
Commands useful for obtaining data from the system:
· Windows version: ver
· Environment variables: set
· System informations: systeminfo /fo list >> C:\tmp\info.txt
· Consult the registry: reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName
· Consult from WMI: wmic os get name, version
· Start and shutdown of the system: TurnedOnTimesView.exe (Fonte: Nirsoft.net)
Commands useful for obtaining data about System Users
· Users:
o Net User [username]
o Userprofilesview.exe /shtml "f:\temp\profiles.html" /sort "User Name" (Source: Nirsoft.net)
· Logged Users:
o PSLoggedOn.exe (Source: SysInternals)
o LogonSessions.exe (Source: SysInternals)
4.1.4. Processes and Applications
It is central to enumerate the processes running on a potentially compromised System. A process is a section or instance of an application that is running. Looking at the running processes in Task Manager gives some information, however much more information can be obtained than can be seen there.
Some of the types of information about the running processes that can be obtained:
· The absolute path of the executable file
· The command used to launch the process
· The amount of time the process is running
· Which user started the process and its level of permissions in the system
· Modules that the process has loaded
· Content of the memory allocated to the process
Examples of programs and commands for acquiring infomation about the processes running on the system:
· Psinfo.exe -h -s -d /accepteula (Source: SysInternals)
· PsList.exe (Source: sysinternals)
· CurrProcess.exe (Source: Nirsoft.net)
· tasklist /v
· Wmic process get name, processid, priority, threadcount, privatepagecount
Examples of programs and commands for acquiring information about services, scheduled tasks and system events:
· [Services] PsService.exe (SysInternals)
· [Services] net start
· [scheduled tasks] schtasks
· [events] PsLogList.exe (SysInternals)
· [events] EventLogSourcesView.exe (Nirsoft)
· [events] wevtutil
4.1.5. Memory
Clipboard is an area in memory where data can be stored for future use. Most Windows applications provide this functionality through the Edit menu and the Copy, Paste or Cut choices. This feature is useful for moving data between applications or documents. Often data stays on the Clipboard for days without the user realizing it.
To collect the data stored in this area of the memory the following application can be used InsideClipboard.exe (Nirsoft.net).
Malware analysts search in memory when dealing with obfuscated malware, because when it is executed it is deciphered into the same memory. In addition Rootkits hide processes, files, registry keys and even network connections. It is possible to check what is hidden from the user’s view by analysing RAM memory. This data is very useful for contextualising identified data in future analysis.
4.1.6. Memory Acquisition
The Memory Dump process (Figure 34) is also widely used to diagnose bugs in programs, as these dumps are normally created when there is an error and programs unexpectedly stop working.
These memory dumps are done in binary, octal or hexadecimal format. An investigation can be made using programs, such as:
· DumpIT (moonsols)
· AccessData FTK Imager
· Belkasoft Live RAM Capturer
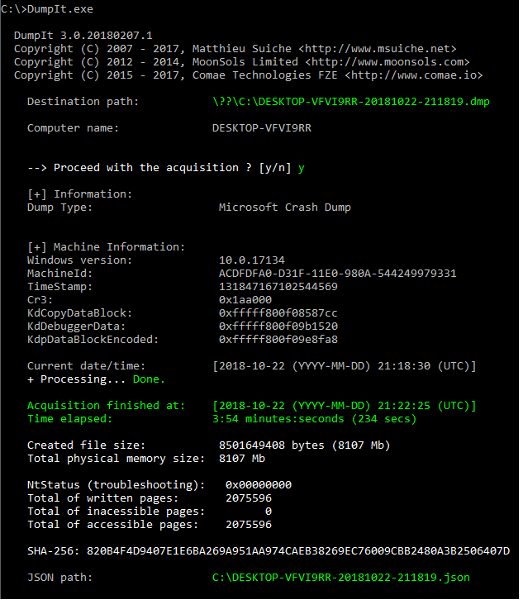
Figure 34 – Example of how DumpIT works
There are other files[3], to support the main memory, which must be collected, such as pagefile.sys, used by Windows as “virtual memory”. Whenever the system needs to use more memory than is available in RAM. Or hiberfil.sys is used to store data from memory when the computer goes into hibernation.
For memory collection in a Linux environment, the dcfldd or insmod programs can be used.
· dcfldd if=/dev/fmem of=memory.dump
· insmod lime-XX.ko "path="memory.dump" format=raw"
4.1.7. Network information
Collecting volatile information about the computer’s network status: active connections, open ports, routing information and configuration, cache, ARP….
As soon as an incident is reported, the investigator must collect information about the status of network connections to the affected system.
These connections can expire and the information can disappear over time. Looking at this data can help determine if an attacker is still logged into the system, if there are malware-related connections, if there is a process trying to find other machines on the network to propagate that malware, or to send log information to a malicious server.
Collecting this information can provide important clues and add context to other informations collected.
Examples of commands for gathering network information:
· Network card information: ipconfig /all
· DNS cache: ipconfig /displaydns
· Active network connections: Netstat -a
· ARP cache: Arp -a
· Netsh int ipv6 show neigh
· Wifi events: Netsh wlan show all
· Wireless Networks: WifiInfoView.exe (Source: Nirsoft.net)
· Routing Table: Route print
· Cache connections: Netstat -c
· List Cache sessions: Netstat -s
· Net accounts
· Resource sharing: Net share
· Query the Server about DNS: Nslookup -d
· List current connections: Rasdial
· List Profiles: Netsh wlan show profiles
