Fundamentals of Digital Forensics
2. Preservation and collection of digital evidence at the crime/incident scene
2.2. Incident management and mitigation
ISO/IEC 27035 defines 5 steps in incident management and mitigation, namely:
- Preparation and Planning
- Detection and recording
- Assessment and decision
- Response
- Lessons learned
1.Preparation and Planning is the phase of identifying all the critical assets of the institution, internal processes for access to information, creation of monitoring systems that allow the identification of incidents, as well as all the responsibilities and procedures in case of anincident.
Preparation
· Preparation of the digital lab
· Defining the team leader
· Defining the team members and responsibilities
· Preparing the briefing / intervention strategy
Briefing
· Intervention strategy?
· Equipment needed to take to the incident site?
· What type of collection/acquisition methods (tools)?
· What is the network activity?
· Volatility of the data collected?
· Could the equipment have been configured to destroy evidence?
· How will we store/transport the digital evidence?
· Related equipment, manuals, etc ?
· Identify possible conflicts of interest?
· Risk assessment
2. Detection and recording is necessarily the phase of identifying events and distinguishing between the event or consecutive events and the possible incident .
Similar to any other crime scene, since the incident may have been intentionally provoked by an internal employee of the organisation. In this way we should take into consideration the previous preparation to act according to the following points:
· Securing the crime scene
· Collecting preliminar information
· Documenting the crime scene
· Collecting and preserving evidence
· Packaging and transporting
· Chain of custody
The maximum possible collection of information, appropriate to the type of possible incident, should be carried out in order to enable efficient decision-making. In this way we should take into consideration all types of information that can be acquired, such as:
· Connection type (Wi-Fi/Ethernet)
· Which computers are used to connect to the internet?
· Location of systems and identify whohas access
· Details of removable devices and user properties
· Obtain details of network topology
· Obtain details of other peripherals connected to the computer
· Are there any other questions on this subject that were not answered?
Of this information, we should take into consideration the surrounding information, such as:
· What services are offered by the organisation?
· Who are those affected by the incidents? Have they been informed?
· Are there logical protection measures (antivirus, firewall, IDS, IPS)? Alarms?
· What physical security measures are in place?
· Are there CCTV records
· Identify the number of computers and computers connected to the internet
· Check the latest hardware replacements
· Level of employee access? Recent redundacies?
· Administrative/Administrator access levels?
· Organisation’s Security Policies?
· Procedures given to contain the incident?
· List of suspects? Why are they suspects?
· System Logs? Network logs? Anything suspicious?
· System usage after the incident? CMD/Shell commands? Scripts? Tasks? Processes?
· Post-incident analysis procedures?
The incident response team should take into consideration the collection of volatile data, which is possibly critical for quick decision-making regarding all past events. Thus, it is important to act in different ways according to whether the computer is on or off (Figure 7).
How to find the computer?
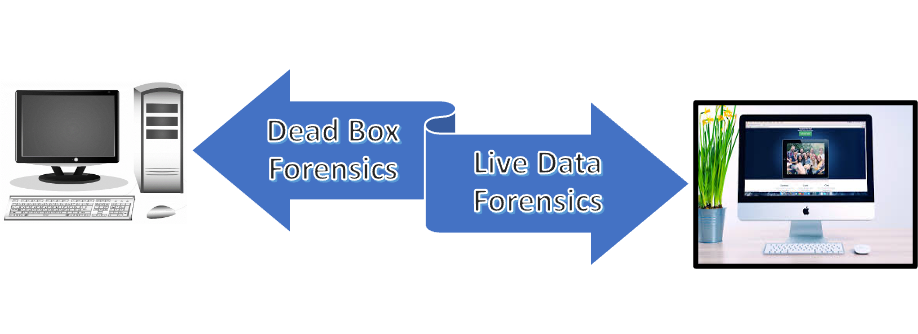
Figure 7 – first action
The first responder must have proper authority and expertise to act
The U.S. Department of Homeland Security has published a short guide for First Responders, entitled “Best Practices for seizing Electronic Evidence”, which has what they call golden rules, which is presented in Figure 8.

Figure 8 - Best Practices for seizing Electronic Evidence
Source: https://www.crime-scene-investigator.net/SeizingElectronicEvidence.pdf
These rules are currently in force and should be followed when responding to security incidents.
The U.S. Department of Justice – National Institute of Justice, on the other hand, has published a flow chart summarizing the process of approaching devices, called “Collecting Digital Evidence Flow Chart” (Figure 9).
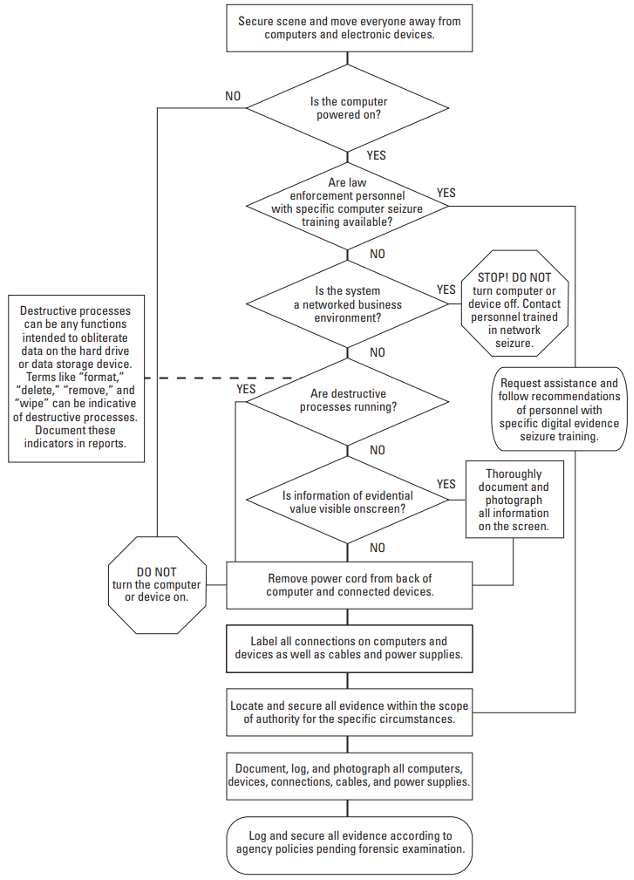
Figure 9 - Collecting Digital Evidence Flow Chart
Source: Collecting Digital Evidence Flow Chart. US Department of Justice - National Institute of Justice (2010).
In this regard, we can determine the following procedures:
1. Ensure physical and electronic security.
2. If the computer is turned off:
· Ensure that it does not turn on (Disconnect power cord/ Remove battery, if any)
· Label/photograph all components and peripherals
· Identify storage devices
· Check BIOS data/time (Without hard disk)
3. If the computer is turned on:
· Disconnect communications (disconnect Network cable/ remove SIM Card)
· Photograph the screen and all its contentes (describe the visible content)
· If there is a need to collect volatile and non-volatile data:
· Perform Live acquisition of the data (according to the order of volatility)
· Check that storage devices are encrypted
· Disconnect the computer from the power supply
· Labelling/photographing all components and peripherals
· Identify the storage devices
· Check BIOS date/time (Without hard disk)
4. If a mobile device (smartphone/Tablet) is envolved:
· If the device is switched off, do not switch on
· If the device is on :
· Photograph the display (if available)
· Pu tinto flight mode
· Always ensure that the device connected to the battery has sufficient power supply to keep it active until analysis
· Use a Faraday bag/sack (Figure 10)

|
Figure 10 – Faraday bag |
· Collect all additional storage devices (memory cards, SIM cards, etc.)
· Document all steps involved in the mobile device seizure
· Question for access codes (PIN/Pattern), SIM card PIN and PUK codes (check device carrying pouches – Figure 11)
How to store and transport?
· Wear gloves
· 
|
Figure 11 – Standard Code |
· Digital evidence with openings and moving components should be sealed with tamper-evident seals or tamper-evident tape
· Devices should be stored in static dissipation and faraday bag
· Document
· Document in a proper report and signed by all involved
· Fill out the equipment’s Chain of Custody (Figure 12)
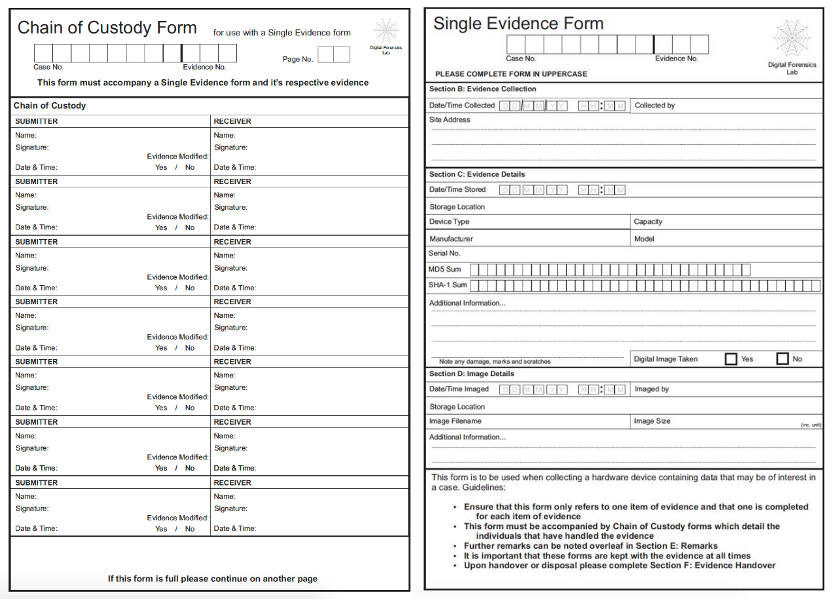
Figure 12 – Chain of custody
3.Assessment and decision is the phase after the knowledge of the existence of a possible incident, gathering all useful information about what happened, leading to a decision on the confirmaton of a IT security incident. With this confirmation, a quick response must be made in order to mitigate and solve it .
4.Response is the phase where the incident is classified, in accordance with that defined in phase 1, categorising the incident and classifying its severity, carrying out the necessary procedures for its mitigation and resolution, using crisis management mechanisms and incident reporting to the competent authorities, in the Portuguese case are the Judicial Police (PJ), the National Cyber Security Centre (CNCS) and the National Data Protection Commission (CNPD).
5.Lessons Learned is one of the most necessary phases, as it enables measures to be implemented so that a similar incident does not happen again, as well as using the knowledge generated to improve the organisation's security system.
See: https://www.cncs.gov.pt/certpt/coordenacao-da-resposta-a-incidents/
