Fundamentals of Digital Forensics
2. Preservation and collection of digital evidence at the crime/incident scene
For the analysis to be performed in the best condition, it will be necessary that the preservation and collection is also performed correctly. In this section we will approach actions at the incident scene in the same way as action at the crime scene, since there are obvious similarities in both, but each of them will necessarily have their specificities and specific characteristics that we will not portray here.
INCIDENT
“Computer incident is an interruption or quality breakdown in an Information Technology Service” Source: Manual “ITIL V3 – Service Operation” (OGC, 2007)
For there to be an incident, there must necessarily be a compromise of the availability, authenticity, integrity and/or confidentiality of the data.
It is the Computer Security Incident Response Team (CSIRT) networks that make it possible to collect data regarding computer incidents, for this they have developed a common taxonomy (Source: https://www.redecsirt.pt/files/RNCSIRT_Taxonomia_v3.0.pdf) of incident classification, classifying them through 2 vectors, by type of incident and by type of event.
ENISA has als developed and promoted knowledge on good practices in incident identification and management, publishing regularly on the subject (Read: https://www.enisa.europa.eu/publications/using-taxonomies-in-incident-prevention-detection).
ENISA in 2010 published the document “Incident Management Guide“ (https://www.enisa.europa.eu/publications/good-practice-guide-for-incident-management) where it classifies incidents into categories according to their degree of severity, as presented in Figure 6.
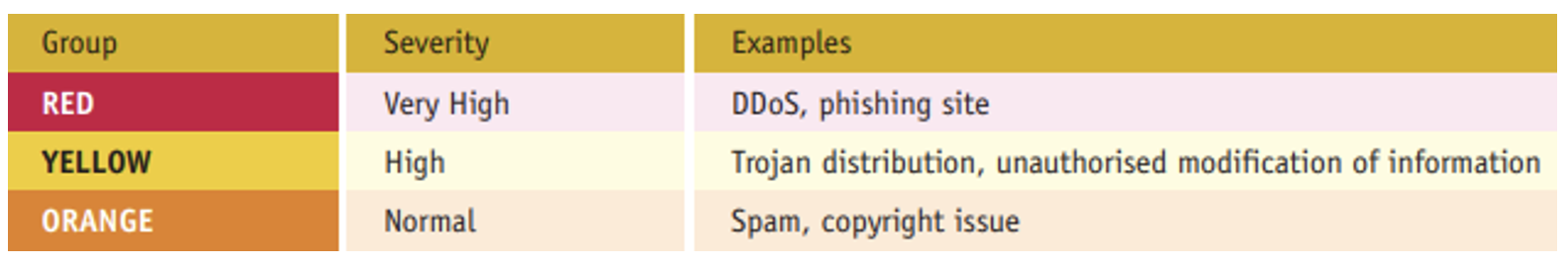
Figure 6 – Incident classification
Source: Incident Management Guide (ENISA 2010)
