Fundamentals of Digital Forensics
1. Introduction to Digital forensics
1.6. Process models in forensic analysis
Each forensic investigator has their own working method and methodology during the course of a forensic analysis, and there is no standard model for each type of investigation, which is usually guided by the past experience of each investigator.
Over the time, various methodologies that define the need for a sequence of generic steps in a forensic investigation have emerged, usually defined as “evidence collection, preservation or examination, analysis”.
Several investigation models have been proposed, also called “Digital Forensics Investigation Frameworks”(Figure 4), these being some of the most popular:
· DFRWS model - Digital Forensic Research Workshop (Palmer et al. 2001)
· ADFM - Abstract digital forensics model (Reith et al. 2002)
· IDIP - Integrated Digital Investigation Process (Carrier et al. 2003)
· EIDIP - Enhanced Integrated Digital Investigation Process (Baryamureeba & Tushabe 2004)
· CFFTPM - Computer Forensics Field Triage Process Model (Rogers et al. 2006)
· SRDFIM - Systematic Digital Forensic Investigation Model (Agarwal et al. 2011)
· IDFPM - Integrated Digital Forensic Process Model (Kohn et al. 2013)
· EDRM - Electronic Discovery Reference Model (https://edrm.net, 2014)
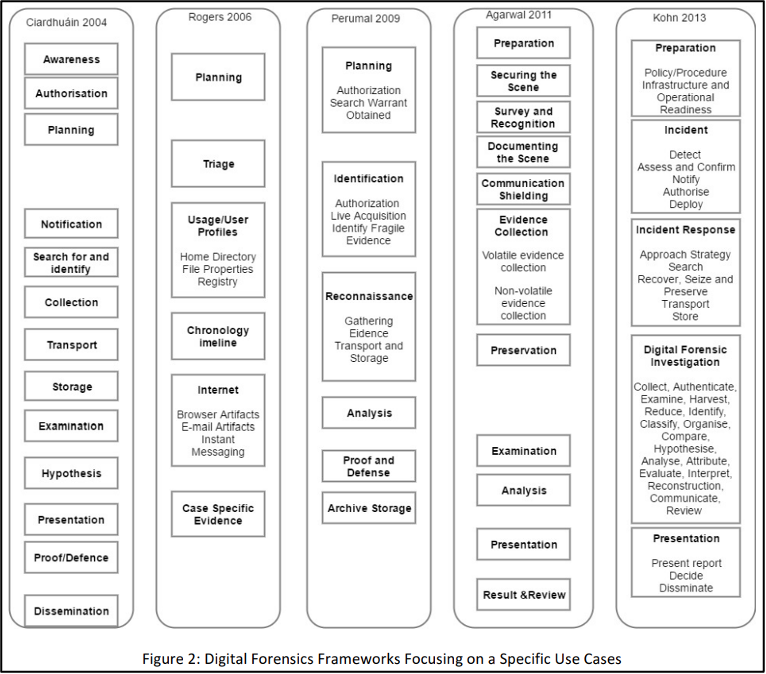
Figure 4 - Digital Forensics Investigation Frameworks
Source: Figure 2 of the article https://arxiv.org/ftp/arxiv/papers/1708/1708.01730.pdf
In 2001, a research arising from the Digital Research Workshops proposed a 6-step framework, as presented in Figure 5.
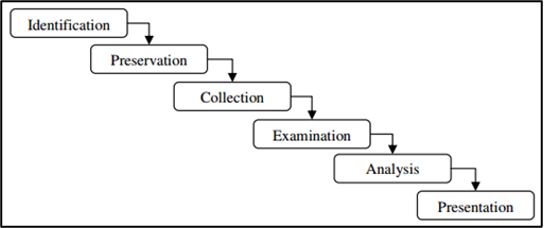
Figure 5 - DFRWS Framework
This is still today one of the main digital forensic investigation methodologies, and the one we will follow. Each of the stages is described below:
Identification – When the researcher needs to identify all relevant information and define the strategy for acquiring that information. The researcher may be dealing with a typical storage device, such as a hard drive, a memory card, or else digital data may need to be collected from network traffic data, volatile data such as memory data, mobile or IoT devices, or any other digital data storage device. At this stage, preparation prior to the use of techniques and tools, is extremely important to ensure the authenticity, integrity and non-repudiation of all evidence in court.
Preservation – This is the stage that seeks to involve tasks such as setting up proper case management and ensuring anacceptable chain of custody in court. This stage is crucial to ensure that data is collected without any external contamination and analysed correctly.
Collection – This step refers to the acquisition of digital evidence, and traditionally this can be done through cloning or forensic imaging of the storage device. The acquisition of volatile data, or other relevant and volatile data, could be decisive for the investigation phase, especially when the data relating to the acquired storage is encrypted. The data collected at this stage is the input data or the source of data for analysis stage.
Examination – This is the phase of searching for the desired data, involving search techniques, recovery of deleted data, data decryption, password cracking, malware analysis, pattern analysis, among others. This phase is interconnected with the analysis phase, since, for example, after the identification of documents it will be necessary to analyse them, taking into account the answer to the requested questions.
Analysis – Analysis of all the data collected. This is the most time-consuming phase, due to the need to do a thorough search and identify all relevant artefacts. It is common in most cases that the data collected comes in the form of unstructured data, requiring specific tools and more time-consuming analysis to idenfitfy potential digital evidence data, where structured data is included, such as records, databases, data files, system files, web pages and others.
Presentation – This is the last phase of the digital forensic analysis process, where a final report with all relevant data to be submitted to the judge. This report should be submitted in hard copy, with all the artefacts considered important. In case of doubts about the information presented in the submitted report, the expert’s testimony in court is required to provide the respective clarifications .
