Fundamentals of Digital Forensics
1. Introduction to Digital forensics
1.2. Digital Forensics Application
The areas of activity of digital forensics are increasingly comprehensive, where before it would only be analysed the hard disks and other media for storing information, now it may be necessary to collect and analyse data in volatile memories (performance in live-data forensics) or even network traffic data (network forensics), data stored on mobile devices (mobile forensics), data stored in distributed systems in Clouds on the Internet, among many others.
Edmond Locard (Figure 1), stated that:
“it is impossible for a criminal to act, especially considering the intensity of a crime, without leaving traces of this presence”
In crimes that somehow involve a digital component, cyberinstrumental and cyberdependent crime (R.Bravo) and according to Edmong Locard’s statement, there is a greater possibility of digital evidence being left, relating the crime to the use of digital means.
Figure 1 - Edmond Locard’s scheme
Source: https://www.crimemuseum.org/crime-library/forensic-investigation/edmond-locard
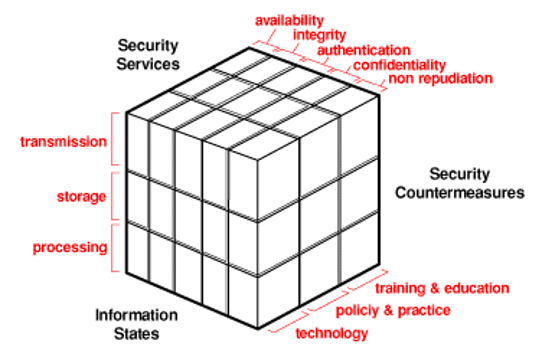
Digital forensics is not considered an exact science, and it is possible that the same digital forensics report analysed by diferent people may have diferent understandings, hence the concern to ensure the basic principles of information security (Figure 2), confidentiality, integrity and non-repudiation, are essential. In this way digital forensics will necessarily be:
LEGALLY ADMISSIBLE AND TECHNICALLY IRREFUTIBLE
The use of universally accepted techniques, complying with the provisions of national laws in an attempt to give each question under investigation as complete an answer as possible, the 7 whys being the most complete form of response:
“What? Where?, When?, How?, Who?, Why? and How Many?”
Inspector-coordinator Rogério Bravo – Judicial Police
Figure 2 – Information Security
Source: John McCumber
Confidentiality
Until the court decides, the people involved are and must remain innocent, and access to their data is totally restricted to the expert himself, who cannot make it available to third parties.
Authenticity
The evidence must be authentic. Produced by people who can answer about it. Otherwise the evidence is considered irrelevant in court.
Integrity
The information contained in the devices must be maintained in its original state at all costs. The expert is responsible for the use of techniques that alter the integrity of the information.
No Repudiation
As far as the exercise of expert functions is concerned, “non-repudiation” suits the use of universally accepted techniques, making it possible to use counter-expertise to obtain the same results.