Comprehensive network security
2. INTRUSION DETECTION SYSTEMS (IDSs)
2.2. Intrusion Detection Systems’ Types and Characteristics
Historically speaking, there are different types of intrusion detection systems, classified according to their nature and way of working. According to different scholars, they can be classified into two main categories: Signature-Based and Anomaly-Based:
·
Signature-Based approaches are
designed based on known attack patterns and are used as rule sets, such as the
ones used by Snort IDS. Incoming traffic is then compared to these rules, in
order to identify abnormal traffic among the normal one (Figure 9).
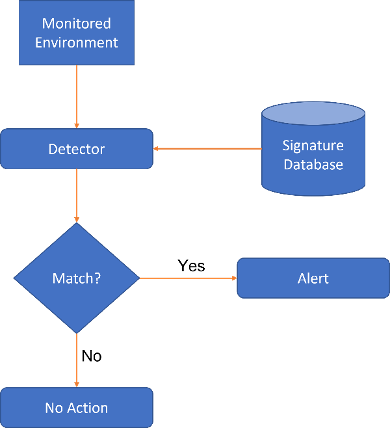
Figure 9 - Signature-based IDS scheme
· Contrasting with the previous category, Anomaly-Based methods are based on the idea of normal behavioural profiles, flagging divergent profiles during intrusion detection. This type of approach often returns a high false alarm rate, when detecting new attacks (Figure 10).
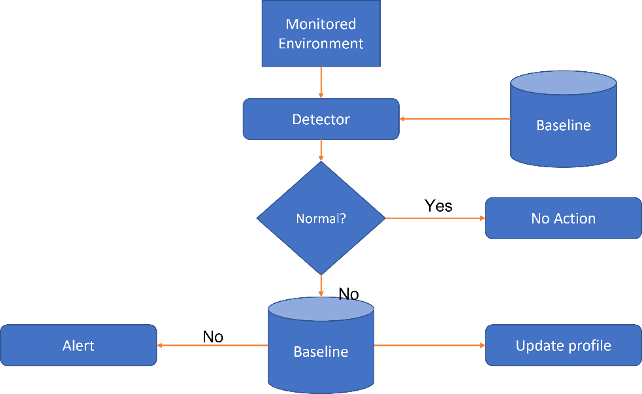
Figure 10 - Anomaly-based IDS scheme
It is also common to find IDS systems categorised as Host-Based (HIDS) (Figure 11) and Network-Based (NIDS) (Figure 12). When compared, a Host-Based IDS system assumes the responsibility of monitoring the behaviour of a single host, while a Network-Based IDS system collects evidence through network traffic data. Some developers consider the combination of these two IDS categories as the best way to protect computer networks against cyber-attacks, though, they are still too immature to be widely deployed. Also, it is possible to identify a weak point in HIDS that must be improved, when it may fail to correctly detect an intrusion in case the host is compromised.
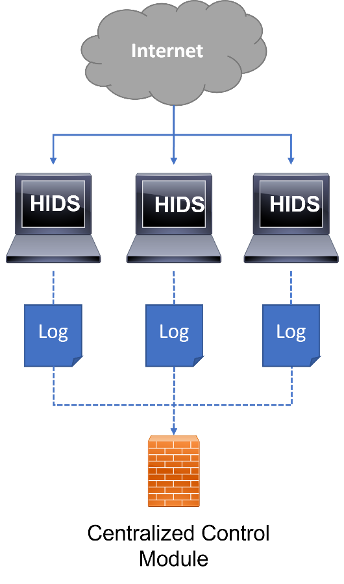
Figure 11 - Host-based IDS scheme
In conventional IDS systems, the paradigm of denying access to malicious packets by dropping them or their root is entirely accepted.
Like in any other computer security mechanism, also in intrusion detection systems there are some advantages and disadvantages that need to be taken into consideration, prior its installation and configuration. It is important to highlight that traditional IDS may not be suitable for all computer systems and networks. A good example of this is regarding critical infrastructures, such as a water distribution system. Working 24 hours a day, and providing drinking water to large cities and country, an IDS must be carefully chosen and implemented, because it may cause a disruption on the communications and, consequently, put in danger human lives. Here, it is important to highlight the existing weaknesses and singular characteristics of such critical systems that must be taken into consideration. The example of SCADA main components, such as PLCs and RTUs have usually low computational and memory capabilities, making them not suitable to allocate a HIDS that must be installed on the host itself for it to be analysed. On the other hand, NIDS sensors can be installed in a separated machine connected to the network to be monitored. Such approach can be easily integrated with the SCADA system, where it is necessary to understand and analyse communication protocols. However, in their current implementations, SCADA communication protocols, which were initially designed to work in serial communications, are embedded into TCP packets’ payloads.
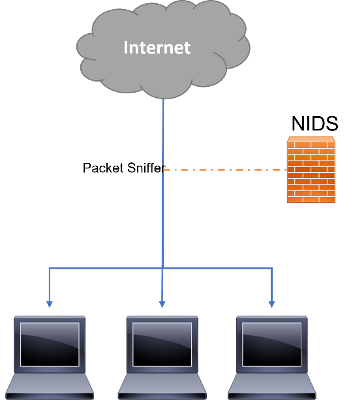
Figure 12 - Network-based IDS scheme
In a deeper view, Signature-Based approaches are designed based on known attack patterns that are used as rule sets. Incoming traffic is then compared to these rules, in order to identify abnormal traffic among the normal one. Contrasting with the previous category, Anomaly-Based often returns a high false alarm rate, when the system behaviour is not properly configured into the IDS system. In the specific case of a critical system, due to its sensitive nature, the normal behaviour and configuration of the system is always deeply documented and kept updated.
Apart from the previous classifications, it is also common to find IDS systems categorized as Host-Based (HIDS) and Network-Based (NIDS). When compared, a Host-Based IDS system assumes the responsibility of monitoring the behaviour of a single host, while a Network-Based IDS system collects evidence through network traffic data analysis. Many scholars consider the combination of these two IDS categories as the best way to protect water distribution systems against cyber-attacks, though, they are still too immature to be widely deployed.
Also in these classifications, it is possible, also, to identify a weak point in HIDS that must be improved, when it may fail to correctly detect an intrusion in case the host is compromised. Moreover, a HIDS should be installed on the host itself, or use an agent, which by itself is not totally practical in a critical network environment, since many of its devices have a low computational and energy power. Furthermore, HIDS also increase the amount of traffic within the network, loading it with IDS information packets, which, once again, may cause more problems to the system then helping it.
In conventional IDS systems, the paradigm of denying access to malicious packets, by dropping them or their root, is entirely accepted. However, due to their critical nature, such paradigm is not acceptable in water distribution systems’ networks. Critical systems require regular and constant communications among devices and controllers, where an unavailable root or packet may compromise the entire system, resulting in catastrophic consequences.
