Comprehensive network security
1. FIREWALLS
1.4. Firewall Topologies and Architectures
Generally located by the border, between the public and the private networks, firewalls can still be used to increase the security of specific network segments within a network. It is common to find them not just to separate private LANs, but also to separate, for instance, critical systems from the internet and corporative networks. Based on this idea, and by the many different firewall types, there are also different implementation topologies and architectures:
· Dual-Homed Host
In this architecture, there is used a computer, named “dual-homed host” placed in between the internal and external networks, usually the Internet. The name given to this computer is because it possesses two different network interfaces, one per each connected network. Like the first proxy implementation way, also here there is no other communication path, forcing all traffic to go through the host and avoiding the direct connection between the internal and external networks. The main advantage on this approach is that it gives a larger control of the network traffic and easier management. On the other hand, this approach is vulnerable in a way that if the host is attacked, it may cause a critical security issue. This type of architecture is usually used on proxy firewalls.
· Screened Host
In a screened host architecture, instead of a single host placed between the internal and external networks, there are used two different hosts, where one plays the role of a router to the Internet (screened router) and the other one as an internal router (bastion host) (Figure 6).
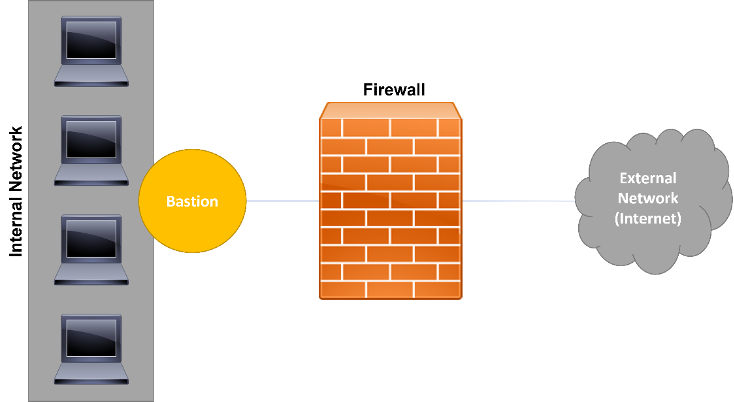
Figure 6 - Screened Host architecture representation
Focusing on the bastion host, it doesn’t allow direct communication at both sides, forcing the communication to flow like: internal network – bastion host – screening router – external network and vice-versa. In this case, the router works by filtering packets, where those filters are designed and configured to redirect the traffic to the bastion host. Consequently, the bastion host will decide, according to its rules, if the traffic is or not allowed, even after the first filtration. The bastion host is a critical point on the network and must be protected to not break the security of the entire network and systems.
· Screened Subnet
The last of the three architectures is the screened subnet that also included a bastion host, like the previous one, however, in this architecture, the bastion host is placed inside an isolated area named DMZ (Demilitarized Zone). The DMZ, is placed between the internal and external networks and surrounded by packet filtering routers (Figure 7).
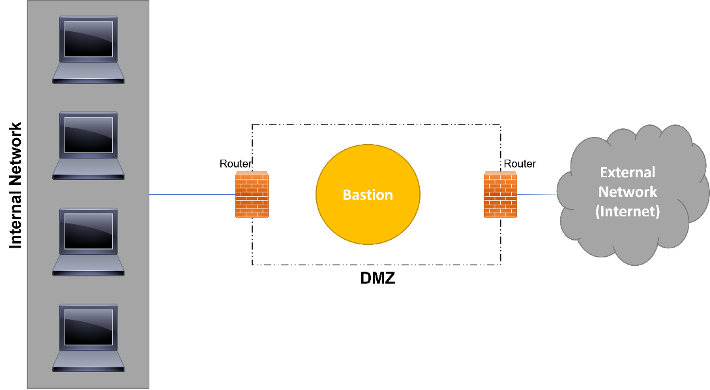
Figure 7 – Screened subnet architecture representation
The use of a DMZ increases the security level, since if the attacker is able to go through the first router firewall, he still needs to deal with the DMZ to gain access to the internal network. The DMZ may also be configured in different ways, including firewalls, proxies, more bastion hosts, and other security systems to improve all security. The high security level and configuration flexibility makes the screened subnet architecture a more complex and expensive one.
