Comprehensive network security
1. FIREWALLS
1.3. Firewall Types and Characteristics
A firewall may work in different ways, based on methodology of the developer, specific needs of the system to be protected, operating system’s characteristics network structure and so on. It is then possible to find different types of firewalls implemented on our networks, including:
· Packet Filtering
Packet filtering was the first developed firewall type, where it was used a simple but limited methodology, focusing the analysis on the packet’s IP addresses (Figure 4).
Data transmission was performed based on the TCP/IP (Transmission Control Protocol/Internet Protocol), which is organized into different layers. Usually, the packet filtering is limited to the network and transport layers: the first one included the IP address from all devices within the network and all routing processes; the second one included the transport protocols that allow data traffic and transmission, such as the TCP. Based on these prime concepts, firewalls using packet filtering were able to firstly filter packets based on their addresses, both source and destination, as well as filter packets according to their TCP and UDP (User Datagram Protocol) ports. As an example, it would be able to block traffic from the IP address 192.168.1.1 on TCP port 80. All services working on this port would be accessible form the device with the mentioned IP address.
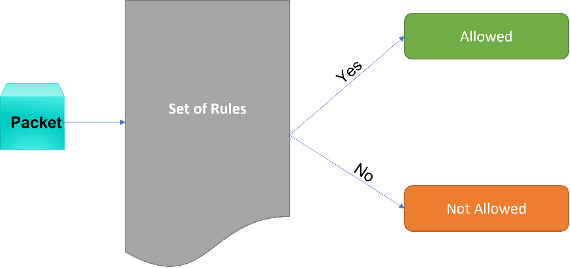
Figure 4 - Simple representation of a packet filtering approach
· Static and Dynamic Filtering
Including all functions from the previous type, it is also possible to find firewalls performing packet filtration in two different ways, where the first one focuses on static filtration, and the second one, which is a bit more developed, focuses on the dynamic filtration. The first model (static), data are blocked or allowed simply based on rules, not taking into consideration any relation among the packets or their connection. At the beginning, this approach didn’t have any issues, however, some new network services or applications may lay their correct communication and data transmission on requests and answers, creating a specific packet flow, related among them. By this, using the first model, it is possible to cause disruption on the communication, resulting in a malfunction of the app or service. Moreover, this may be also seen as a security concern, where the network administrator would be forced to create singular and specific rules to avoid these services from crash, increasing the possibility of no blocking packets that should indeed be blocked.
On the other hand, dynamic filtration came to address such limitations. This packet filtering model, filters consider the packets context to create rules capable of adapting to the scene and, consequently, allowing specific packet traffic to work, while it is necessary and only during a specific period. By this, the chances of blocking trustful packets drastically decreases.
· Personal Firewalls
There are also simple firewalls designed to protect personal computers and mobile devices and able to be used by the normal user. Today’s operating systems already include a firewall software, including Microsoft Windows, Linux and Mac OS X. Also, there are some antivirus software that include different levels of protection and a firewall. These firewalls, have limited performance and protection, allowing users to apply simple rules and configure the access from apps and services to the Internet. Though they increase the level of security of the device, there are still possible to bypass and make the device a target of attack. Hackers can easily bypass such firewall types and exploit systems vulnerabilities. In a corporative network is it advised to also use boundary frameworks, such as explained before.
· Software and Hardware Firewall
Also previously mentioned, firewalls may be implemented at both hardware and software ways. By itself, this information is not incorrect, however, it is necessary to add that the hardware itself is nothing more than a device, where the firewall software is installed. Usually known as firewall appliances, these devices are dedicated to performing the firewall role only and may include different configurations and ports, to connect to different networks. Moreover, such appliances are usually used on larger networks, where there is a considerable amount of network traffic, or where data is sensitive. The main advantage of these firewalls is that because the hardware was specifically developed for this purpose, it can deal with larger volumes of data and are not vulnerable to attacks that are usually found in a conventional server.
· State-Based Firewall
After the simple packet filtration, came the state-base technology applied to firewalls. This cause almost a revolution on the way firewalls used to work, because instead of a simple packet analysis, as they were passing through the firewall, and blocking or allowing them according to simple rules, state-based firewalls manipulate dynamic information and keep their monitoring actions analysis packets even while they are transiting within the network. While the packet filtering type of firewall was only able to block or allow packets based on their IP addresses and ports, a state-based firewall can detect and block illegitimate network traffic, based on patterns and other advanced state concepts. However, it is important to highlight that this type of firewall brings a disadvantage related to the necessity of storing traffic data in memory and to a deeper and stronger analysis that demands a higher processing power and storage capabilities.
· Application Firewall
Though this technology is still used nowadays, by itself, it is not enough to properly protect the network against attacks and intrusions. Application and Web application firewalls were born as the next great step on security. Traditional firewalls were limited to the general network traffic analysis and monitoring, failing to properly detect traffic originated from applications, services, or other software. These new application firewalls were designed to deal with this gap, being able to block intrusion attempts that take advantage from vulnerabilities possible to be exploited. In addition, many of them come with a parental control, being also able to detect the type of content and identify if it is suitable for youngers to see.
· Proxy
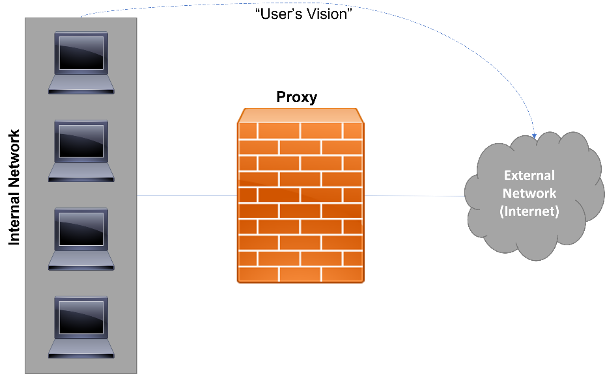
Figure 5 - Example of the implementation of a proxy server in between of the external and internal networks
Working as proxy server, filtering essentially the http content and browser accesses, the firewall may be implemented in between the private and public networks (Figure 5). This way forces all traffic to be analysed and monitored, allowing a better control of the access and data transmissions. Though, it is also possible to implement it as a normal server, forcing all http traffic to be forwarded through it. This is commonly used by many organizations, where it is demanded that all web browsers are configurated to send the traffic to the proxy server to be analysed. Consequently, the main firewall must block all http traffic that doesn’t come from the proxy server. Only this way it is possible to properly control the http requests and responses.
· Next-Generation Firewall
The next-generation firewall was the last concept to be developed and focus essentially the corporative world. This new firewall type includes all the previous ones into a centralised filter, being able to analyse and monitor packets, intrusion and prevention of applications and services, among others. These firewalls are also possible to be found as an online service, however, their majority are still applied as an appliance. Being more robust and with a deeper analysis, their implementation is more complex and must be carefully performed, where a proper security plan should be developed and regularly updated. Used as the main security mechanism, these firewalls are often installed on the border between the private and the public networks, controlling the inbound and outbound traffic.
