Comprehensive network security
1. FIREWALLS
1.1. Introduction to Firewalls
Widely used nowadays, the term firewall is cited by all kinds of information technology users, referring not just to computers but also to mobile devices, and by its literal meaning, wall of fire, it is well known as one of the main security mechanisms implemented worldwide.
Though it is directly related to information technologies, the word firewall wasn’t born with the internet. It was already used in houses, cars, between others. One of the main examples is related to the doors that prevent the fire from spreading around the buildings, while firemen try to control it. The first firewalls were developed by the end of 1980, right after the first computer virus, named “Morris Worm”, was discovered, which infected many large organizations, such as NASA, Berkeley and Stanford Universities, showing that the Internet was no longer a closed community and just used by trustful people.
In their very beginning, firewalls were no more than simple routers, configured to separate the private network into smaller ones (Local Area Networks or LANs), preventing network errors to be spread around the LAN, and, consequently, improving its global performance. This type of firewall was mainly used during the 90s and were based on filtering rules, where the focus was given to the IP address, allowing all devices within the private network to access the Internet or public network (outbound traffic) and blocking public IP addresses from entering the private LAN. These firewalls were not that efficient and were very limited, since they didn’t provide a proper way to build strong security and access rules, making it impossible to restrict the access of a specific part of an application or software.
The second generation of firewalls came to provide the possibility of also examining the transport layer (OSI’s layer four), instead of being limited to the IP address (OSI’s layer three). Having the knowledge about active sessions, firewalls were then able to take advantage of that information to improve the bandwidth of the network and packet processing velocity and efficiency. By this, the filtration was performed not only by the IP address, but also by the communication attributes.
On their third and more recent generation, known also by application filtering, firewalls take advantage of the previous two technologies, associated with a proxy server, working as a mid-agent, to evaluate the requirements of each communication that arrives or departs from our connected networks. This proxy may be seen as a door man, where it is only allowed to pass the people who are granted permissions for a specific destination (Figure 1).
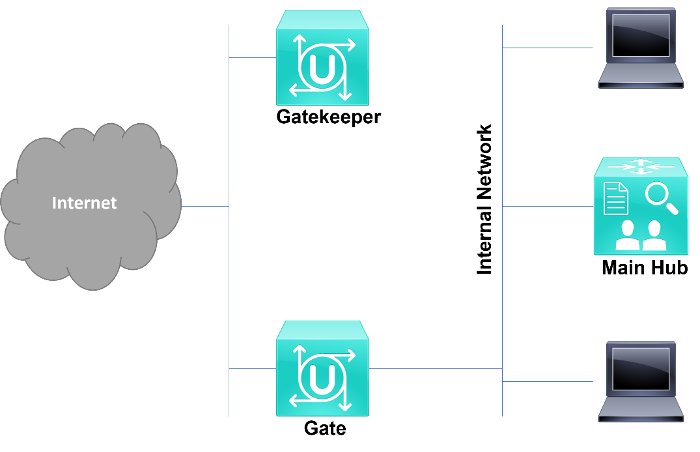
Figure 1 – Third Firewall Generation
A firewall may be seen as one or more devices, including both software and hardware, strategically placed in the border of two different networks, usually called private and public networks (Figure 2).
Based on its implementation, in between those two networks, it is capable to inspect and analyse all network packets that comes to it, through its different interfaces, and it acts as it was the border controller at the airport, checking all passports and visa permissions from that specific packet, allowing it to follow through or vetting its access. Using this main principle, this technology avoids the entrance of undesired communications from the public to the private networks, or vice-versa, and consequently protects the information and resources within our private systems.
Moreover, this type of filtering is also capable of avoiding internal devices from accessing domains and information that do not go in line with the network security policies. Focusing on simple networks, such a domestic one, the firewall is usually implemented on the router software. The case of larger networks, including the corporative ones, it is highly recommended to use a robust hardware firewall, dedicated to protecting the border of the network, making sure that just essential communications and functions are allowed, and granting the security of the network.
It is also important to highlight that to prevent the network from attacks, the firewall must be able to prevent attacks against itself, at both levels, internal and external (private and public networks).
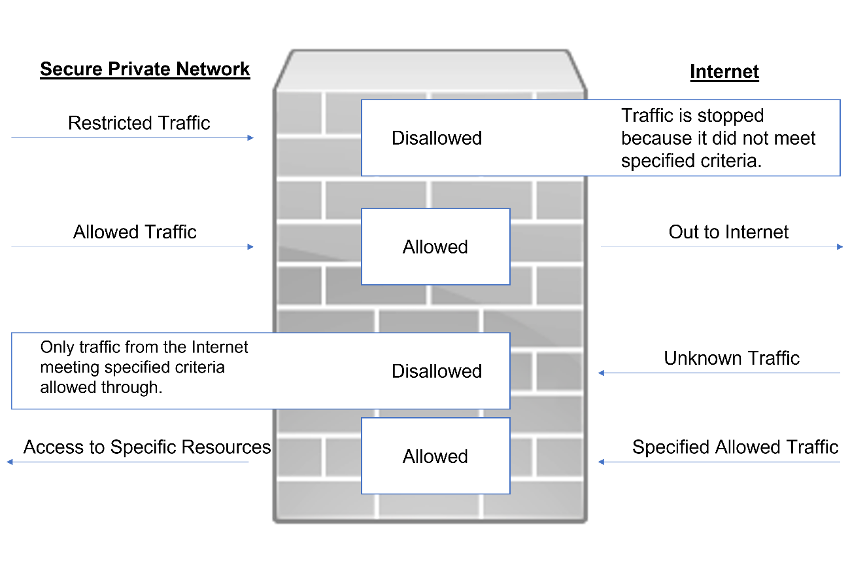 Figure 2 - Security solution, placed
in between the private and public networks
Figure 2 - Security solution, placed
in between the private and public networks
As it was said before, a firewall may be based on both hardware and software solutions, where the most common one is the second option, not only by its cost and its implementation, but also because it is present in almost every network system and personal computers. Working under a set of rules or instructions, the firewall analyses the network traffic to identify the allowed data transmission or reception actions. Also, by its literal name, it makes clear that the system is basically an undesired traffic blocker, allowing only the specific network traffic that follow the configured accessing rules (Figure 3).
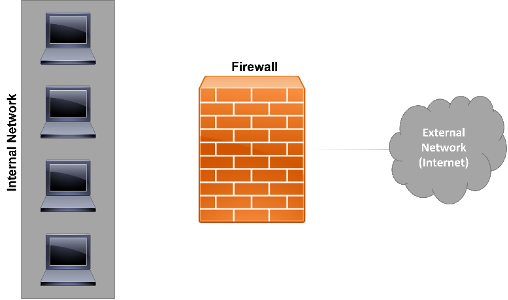
Figure 3 - Basic representation of a firewall implementation
In sum, and the most important concept is that a firewall is a security system able to protect a private network from external attacks, being also able to control the communications, based on rules that are built towards the organization security policies. It is present not only in high level networks, such as the corporative ones, but also as a software in home internet connection routers, desktops, laptops, and even mobile devices.
