Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.18. Cyberterrorism
In connection with cyberattacks, we cannot neglect to mention terrorism, which is one of the current global threats, or its noticeable dynamic growth and spread worldwide.
Terrorism can be divided according to form into lethal and non-lethal forms, where the first group is characterised by the use of common means of violence (conventional – attacks committed using commonly available weapons, such as firearms and unconventional – misuse of weapons of mass destruction). However, non-lethal forms of terrorism [1] or attacks using more modern tools in combination with lethal means are more common in the Internet.
The conventional form of non-lethal terrorism includes the following subgroups:
- Unarmed terrorism.
- Cyberterrorism, one of the greatest dangers of the 21st century. The principle is primarily the misuse of ICT (including the Internet) as a means and environment for carrying out an attack. Similarly to the classic conventional terrorist attack, this is a planned activity usually politically or religiously motivated and carried out by small rather than militarily organised structures. The aim of these groups is primarily to influence public opinion. Due to the rapid spread of information and communication technologies around the world, cyberterrorism poses a significant threat and is increasingly used by terrorist groups. [2]
- Media terrorism, in which there is a planned abuse of the media and other psychological weapons in order to influence the opinions of the entire population or target groups of the population.
This relationship is most aptly characterised by the diagram shown in the following figure.
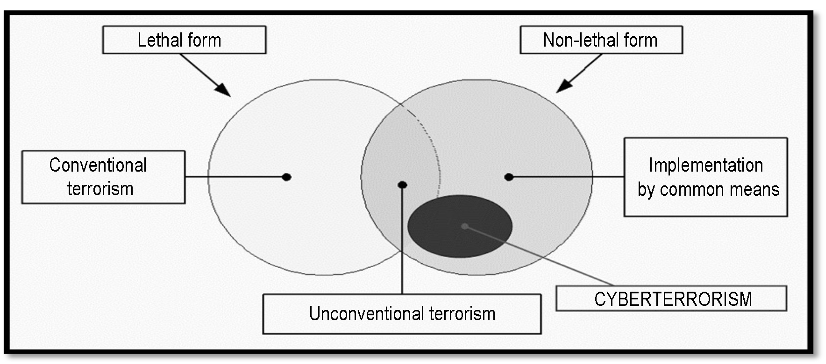
Forms of terrorism, including cyberterrorism
The global nature of
the IT and telecommunications environment enables the transfer of information
and the coordination of terrorist activities throughout the world. It is stated
that, for example, the attack on the WTC in New York was organised using the
Internet.
There may be other cases of misuse of the Internet for the dissemination of malicious information or for psychological operations related to media terrorism. The Internet plays a significant role in spreading propaganda, ideology or intimidation, for example by publishing executions of prisoners online [3] , attracting and mobilising new activists, sympathisers or sponsors, defending terrorist acts and inciting individuals to commit them. Terrorist groups' Internet sites often contain instructions for making makeshift weapons, or propaganda targeted at the younger generation.
The Internet provides exceptional opportunities for extremist and terrorist groups as well as individuals, especially in the area of fast and relatively secret communication, where it serves to exchange information and instructions for planning and coordinating events or transferring funds.
Almost all terrorist groups and organisations run their websites. They are usually published in several language versions, and there are also special pages aimed at children and women containing fairy tales or comics, which incorporate, for example, the stories of suicide bombers. [4]
TravelWest.info website after being attacked by attackers
Possibilities of criminal sanctions in the Czech Republic
From the point of view of criminal law, the aforementioned acts may fulfil the objective elements of criminal offences under Section 311(2) (Terrorist Attack), Section 355 (Defamation of Nation, Race, Ethnic or other Group of People), Section 356 (Instigation of Hatred towards a Group of People or of the Suppression of their Rights and Freedoms), Section 364 (Incitement to Criminal Offence), Section 403 (Establishment, Support and Promotion of Movements Aimed at Suppression of Human Rights and Freedoms) and Section 404 (Expressing Sympathies for Movements Seeking to Suppress Human Rights and Freedoms) of the Criminal Code.
Possibilities of criminal sanctions in Poland
In Poland, Articles 265 through 269 and Article 287 of the Penal Code apply to the implementation of a cyberterrorist attack and, depending on the effect of the cyberterrorist attack, some other Articles of the Penal Code may also be applicable, such as:
Art. 163 Causing a catastrophe
Art. 164. Causing the danger of a catastrophe
Art. 165. Causing public danger
Art. 173 Causing a traffic accident
Art. 174. Causing an imminent danger of a traffic disaster
Possibilities of criminal sanctions in Portugal
According to Law No. 52/2003, on the fight against terrorism, if connected with terrorism intents, the penalties for offences such as Computer-related fraud or Computer related forgery will be aggravated by a third (Art. 4(2). Besides, the public provocation to offences related to electronic communications (Art. 4(3)(4), recruiting (Art. 4(5)(6) or the promotion of terrorist groups or actions are aggravated if practiced by the Internet (Art. 4(8)(9).
[1] However, it is possible to imagine a combination of these attacks. For more details, see e.g.:
Exclusive: Computer Virus Hits U.S. Drone Fleet. [online]. [cit.10.7.2016]. Available from: https://www.wired.com/2011/10/virus-hits-drone-fleet/
[2] JIROVSKÝ, Václav. Kybernetická kriminalita nejen o hackingu, crackingu, virech a trojských koních bez tajemství. Prague: Grada, 2007, p. 129
[3] The presented URL is not censored and contains drastic footage! See e.g.:
WATCH: ISIS Downs Prisoners Alive & Blows Hostages Up With RPG & Kills Others With Explosives – Graphic video. [online]. [cit.20.8.2016]. Available from: https://www.zerocensorship.com/uncensored/isis/drowns-prisoners-alive-blows-hostages-up-with-rpg-kills-others-with-explosives-graphic-video-132382
Disturbing ISIS video shows militants beheading four prisoners and gunman executing shoppers at market. [online]. [cit.20.8.2016]. Available from: http://www.mirror.co.uk/news/world-news/disturbing-isis-video-shows-militants-7306017
[4] JIROVSKÝ, Václav. Kybernetická kriminalita nejen o hackingu, crackingu, virech a trojských koních bez tajemství. Prague: Grada, 2007, p. 138
See also e.g.:
Cyber Terrorism: How Dangerous is the ISIS Cyber Caliphate Threat? [online]. [cit.20.8.2016]. Available from: http://www.govtech.com/blogs/lohrmann-on-cybersecurity/Cyber-Terrorism-How-Dangerous-is-the-ISIS-Cyber-Caliphate-Threat.html
Islamic State Hacking Division. [online]. [cit.20.8.2016]. Available from: https://ent.siteintelgroup.com/index.php?option=com_customproperties&view=search&task=tag&bind_to_category=content:37&tagId=698&Itemid=1355
