Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.17. APT (Advanced Persistent Threat)
APT means an advanced and persistent threat. It is a long-term systematic cyberattack, focused on a target computer system, or on the ICT of a target organisation. Various techniques and relatively large resources are used for such an attack, and typically secondary targets (e.g. computer systems such as repeated DoS or other attacks) can be attacked in order to divert attention from the primary target (malware infiltration of a company), which is then attacked.
"APT is usually focused on extracting strategically valuable classified or non-public data, limiting a target's ability to act, or taking a position that enables the future implementation of the above-mentioned. The implementation of actions that meet the definition of APT is associated with a high level of expertise, considerable financial resources and the ability to adapt to the actions of the victim of the attack in the long term. The character of APT thus acquires primarily state actors, i.e. their controlled and sponsored groups, or specialised groups of organised crime.“ [1]
An APT attack typically consists of:
· an acquisition of information about a target of an attack (collection of information from open sources; use of social engineering, etc.)
· an actual attack:
o Selection of suitable means (malware, creation of cover identities, etc.)
o If a system is vulnerable from the outside, it is attacked
o If a system is inaccessible from the outside, other techniques combined with social engineering are used (e.g. Spear phishing, Identity Theft, etc.)
· taking control of some computer systems, consolidating positions within the compromised computer network
· collecting data and information and sending them to the attacker
· data extraction
During an APT attack, attackers can use other different types of attacks on the selected target, depending on the data and information they have acquired.
APT can be displayed using its life cycle:

Life cycle of APT attack [2]
An APT attack can last from several months to many years, and an attack can include relatively long periods when the activity of attackers is minimal. It is no exception to conduct a large number of similar operations against different objectives at the same time. [3]
The Kasperky Lab website (https://apt.securelist.com/#firstPage) visually depicts known APT attacks, including information on when a sample of attack malware first appeared, when an APT attack was discovered, where it primarily operates (geolocation information, primarily attacked operating systems, number of targets, etc.), etc. The following two print screens show the primary binding of Stuxnet malware (including, among others, to Duqu 2.0) and then the binding of Duqu 2.0 to other malware.

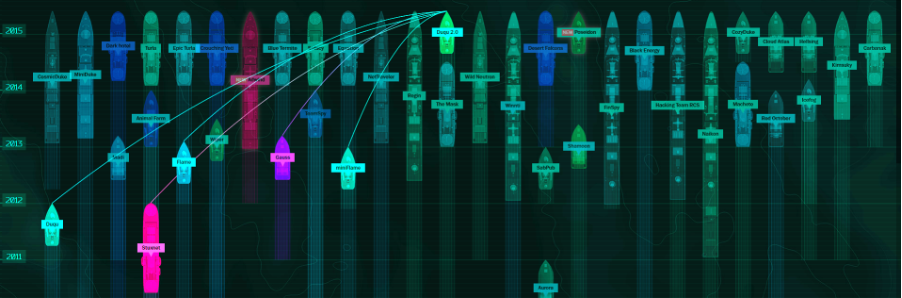
Display of APT attacks including their interconnection [4]
Possibilities of criminal sanctions in the Czech Republic
Any criminal sanction of an attacker or attackers performing an APT attack then depends entirely on their actions, which may take the form of, for example, distribution of malware, one of the phishing attacks, Identity Theft, etc.
Possibilities of criminal sanctions in Poland
When analysing an APT attack in terms of violations of the law in force in Poland, it should be considered that if an attack was carried out at all its stages, at least a few offences would be committed. Pursuant to the applicable legal regulations, an APT attack may be considered:
- hacking under Art. 267 § 1 of the Penal Code
- crime of producing or making available computer devices or programs, passwords and codes under Art. 269 b of the Penal Code
- computer fraud under Art. 287 of the Penal Code
Other crimes that may occur during the implementation phase are:
- computer sabotage under Art. 269 of the Penal Code,
- bringing danger to life, health or property under Art. 165 of the Penal Code,
- destruction, damage, deletion of IT data from art. 268 a of the Criminal Code,
- disruptions in the operation of the computer system or ICT network pursuant to Art. 269a.
An APT attack can also be tantamount to espionage under Art. 130 § 3 of the Penal Code.
Possibilities of criminal sanctions in Portugal
APT attack aren’t specifically criminalised, not even as aggravated offences.
[1] Advanced Persistant Threat. [online]. [cit.20.8.2016]. Available from: https://www.isouvislosti.cz/advanced-persistent-threat
[2] Advanced Persistant Threat – life cycle. [online]. [cit. 20. 8. 2016]. Available from: https://upload.wikimedia.org/wikipedia/commons/7/73/Advanced_persistent_threat_lifecycle.jpg
[3] For more details see: Advanced Persistent Threat. [online]. [cit. 20. 8. 2016]. Available from: https://www.isouvislosti.cz/advanced-persistent-threat
Advanced Persistent Threat (APT). [online]. [cit. 20. 8. 2016]. Available from: http://searchsecurity.techtarget.com/definition/advanced-persistent-threat-APT
Advanced Persistent Threats: How They Work. [online]. [cit.10.7.2016]. Available from: https://www.symantec.com/theme.jsp?themeid=apt-infographic-1
How do APTs work? The Lifecycle of Advanced Persistent Threats (Infographic). [online]. [cit. 10. 7. 2016]. Available from: https://blogs.sophos.com/2014/04/11/how-do-apts-work-the-lifecycle-of-advanced-persistent-threats-infographic/
[4] Targeted cyberattacks logbook. [online]. [cit.10.7. 2016]. Available from: https://apt.securelist.com/#secondPage
