Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.13. DoS, DDoS, DRDoS attacks
The term DoS is an abbreviation of “denial of service”. This is one of the forms of attacks on an (Internet) service, the aim of which is to deactivate or reduce the performance of the infected technical equipment. [1] This attack is carried out by flooding a compromised computer system (or network element) with repeated requests for actions to be taken by the computer system. This attack can also be implemented by flooding information channels between the server and the user's computer or by flooding free system resources. A system mainly exhibits infection from a DoS attack through unusual slowdown of service, general or momentary unavailability of service (e.g. websites), etc.
The difference between DoS, DDoS and DRDoS attacks lies mainly in the way the attack is conducted. For clarity, figures demonstrating the method of the attack are attached to the individual types of attack.
In the case of DoS (Denial of Service), the source of the attack is one. This type of attack is relatively easy to defend, as it is possible to block traffic from the source of the attack.
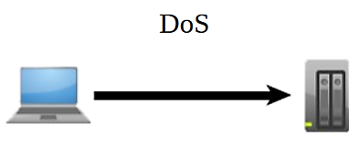
With Distributed Denial of Service (DDoS), the target computer system is congested by sending packets from multiple computer systems in various locations, making it difficult to defend against and identify the attacker.Such attacks have been used, for example, against Yahoo! Inc., e-commerce, etc. [2] Botnets or activities of users supporting a certain online campaign are very often used for this type of attacks (see below – Anonymous and LOIC).
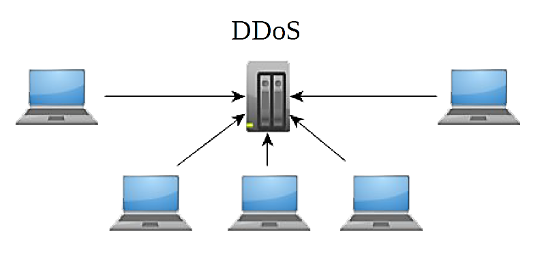
In the case of DRDoS (Distributed Reflected Denial of Service), it is a spoofed distributed DoS attack that uses a so-called reflection mechanism. The attack consists of sending fake connection requests to a large number of computer systems, which then respond to these requests, but not to the initiator of the connection but to the victim. This is because spoofed connection requests have the victim's address as the source address, which is then flooded with responses to those requests. Many computer systems thus become an involuntary participant in an attack, in fact, by responding correctly to a connection request.
DoS, DDoS, DRDoS attacks very often use bugs such as the operating
system, running programs or network protocols – UDP, TCP, IP, http, etc.
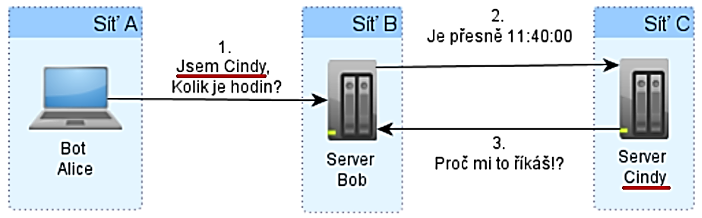
Text on the figure:
Network A, Bot Alice
1. I'm Cindy, What time is it?
Network B, Server Bob
2. It's exactly 11:40:00
Network C, Server Cindy
3. Why are you telling me this!?
There are several basic methods of DoS or DDoS attack, the most well-known ones are the following:
- Flooding with ping command (Ping-Flood)
Due to the Internet Control Message Protocol and the Ping tool (Packet Internet Groper), it is possible to use the “ping” command to determine the “life” of a computer system with a given IP address and to detect the response time of such a system. As part of the Ping-Flood attack, a victim is flooded with a large number of so-called ICMP echo request packets, to which the victim begins to respond – sending so-called ICMP Echo Reply packets. An attacker hopes that this will overwhelm the victim’s bandwidth (for receiving and sending data). The actual attack can be further intensified by setting the ping emitting ICMP packets option flood. The packets are then sent without waiting for a response. If the target computer system is underperforming, it can be made inaccessible.
- Flooding of free system resources (SYN-Flood)
SYN-Flood is a type of attack in which an attacker tries to overwhelm his victim with a large number of connection requests. An attacker sends a sequence of packets with a SYN command (SYN packets) to the target computer system (victim), with the target system responding to each SYN packet by sending a SYN-ACK packet, but the attacker no longer responds. The target computer system waits for the final acknowledgment, the so-called ACK packet from the connection initiator (attacker) and holds the allocated resources for this connection, but it has a limited number. This can deplete the system resources of the target of the attack. [3]
- Source address spoofing (IP spoofing)
IP Spoofing is an activity consisting in forgery of a source address of sent packets, when an attacker initiating a connection from machine A with the IP addressa.b.c.d inserts e.g. IP address d.c.b.a as a source address and sends them to a target B. Target B then responds to this source address, i.e. the response is not addressed to the IP address a.b.c.d, but to the IP address d.c.b.a. Using this method, it is possible to make attacks worse (intensify attacks) such as DoS, DDoS. An attacker uses this technique when he does not need a response from his target to his connection request, he just wants to employ him. When an attacker specifies the IP address of the target of his attack (e.g.a.a.a.a) as the source IP address in the sent packets and sends the packets to many other computer systems (IP addresses), these then respond to the computer system a.a.a.a. In this way, a DRDoS attack is carried out.
- Smurf attack
This attack is executed through a misconfiguration of the system, which allows the transmission of packets to all computers connected to the computer network through the broadcast address.
The goal of DoS/DDoS attacks is usually not to infect a computer or computer system, or to overcome security protection with a password that protects it, but to either overwhelm or temporarily disable it using a series of repeated requests. Typically, this will restrict or block access to services.
In order to be able to legally prosecute an “attacker” who has used DoS or DDoS attacks, it is necessary to determine whether his conduct was illegal and, if so, how serious the conduct was. The point is that a DDoS attack in its nature can be, for example, the completely above board activity of Internet users trying to connect at one time (in a short period of time) to a web server of a company that provides discounts on tickets and, for example, announced that from 12.00 there will be a comprehensive reduction of tickets by 75%. Or it may be access by a large number of users to a web service of one of the popular media that report on important or newsworthy events – the inauguration of a new president, the death of a prominent person, etc. If the target computer system (webserver) is insufficiently dimensioned or is incorrectly configured (it is not able to handle the required amount of access), it will “collapse” similarly to a targeted DDoS attack. The question then is whether users who tried to log in to said website at the given time and thus practically caused the shutdown of the service in question should be punished.
I believe that in the cases outlined above, although users have caused a massive DDoS attack on a provider's service, it is not realistic or even conceivable to punish these “pseudo-attackers” by any legal instrument, as their conduct was not illegal from the outset.
However, a different case would be a situation where attackers are called, for example, via the Internet and at a specific time, due to their re-login to the provided service, suppress this service. [4] Such cases occurred, for example, in the context of protests against the ACTA (Anti-Counterfeiting Trade Agreement) in 2012, when one of the options for committing these attacks was to use a tool distributed to Anonymous supporters, the LOIC (Low Orbit Ion Cannon).
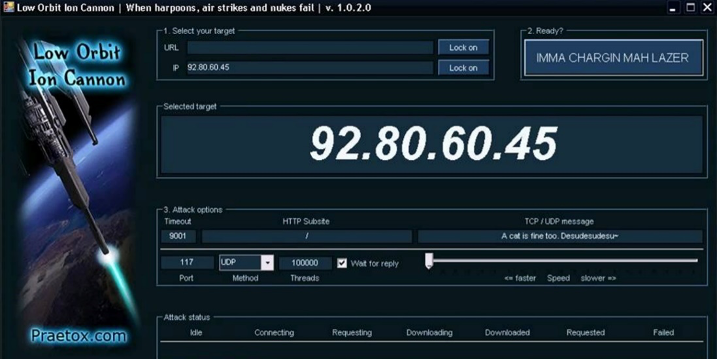
LOIC (Low Orbit Ion Cannon) [5]
The imaginary successor of LOIC was the HOIC (High Orbit Ion Canon) software, which was developed as a replacement for LOIC.
HOIC (High Orbit Ion Canon) [6]
The conduct of the attackers in this case is certainly illegal, because these attackers were aware or at least understood that their actions interfere with the rights of others. In this case, it would be possible to use the instruments of criminal, administrative and civil law.
Due to the adoption of the Convention on Cybercrime, criminal law should be harmonised and such legal norms should be adopted, in the EU member states and beyond, which should be able to punish DoS or DDoS attacks by the criminal law of that country. The following calls for protection against these attacks and the implementation of legislative measures: Chapter II – Measures to be taken at national level, Section 1 – Offences against confidentiality, integrity and usability of computer data and systems, Article 4 – Interference with data, of the Convention:
1. Each Party shall take such legislative and other measures as may be necessary to establish as a criminal offence, in accordance with its domestic law, an intentional unlawful damage, erasure, deterioration, alteration or suppression of computer data.
2. A party may reserve the right to stipulate that it will consider the conduct described in paragraph 1 to be criminal only if it causes serious harm.
Possibilities of criminal sanctions in the Czech Republic
It follows from the wording of the provisions of Section 230 (2) (Unauthorised access to the computer system and information carrier) of the Criminal Code:
Whoever gains access to a computer system or information medium and
a) uses data stored in a computer
system or information media without an authorisation,
(b) erases or otherwise destroys, damages, modifies, suppresses, or
corrupts the quality of data stored in a computer system or information
media, or renders them unusable without authorisation…
It follows from this provision that an attacker committing a DoS or DDoS attack must, in order to be criminally liable, gain unauthorised access to a computer system and subsequently suppress the data in it. [7]
In this case, two separate articles (Chapter II, Section 1, Article 2 – Illegal Access and Article 4 – Interference with data) of the Convention on Cybercrime were merged into one provision.
The legislator thus made it practically impossible to punish the perpetrators of DoS or DDoS attacks by means of criminal law, as an offender is required to gain unauthorised access to the computer system. This legal interpretation, which requires gaining unauthorised access to a computer system, thus allows an offender to be punished only for the conduct specified in the Convention on Cybercrime in Article 2 – Illegal Access: “Each Party shall take such legislative and other measures as may be necessary to ensure that, under its domestic law, unauthorised access to all or any part of a computer system is a criminal offence when committed intentionally.”
From a technical point of view, DoS or DDoS attacks do not gain access to a computer system or part of it, or at least it is not the primary goal. [8]
For the above reasons, I am convinced of the need to incorporate into the Czech legislation a separate objective element of the crime, which would protect the computer system from DoS, DDoS, DRDoS, etc. attacks and which would respect the provisions of the Convention on Cybercrime. It would be possible to use, for example, the following wording:
“Whoever prevents the use of a computer system without authorisation…"
At present, it would be theoretically possible to charge perpetrators with DoS and DDoS attacks for a criminal offence under Section 228 (damage to property) of the Criminal Code. [9] However, a condition for the use of the institution of damage to property would have to be the fact that such a thing (including a computer system) would be destroyed, damaged or made unusable. However, this condition usually only applies to this type of attack with regard to a certain temporary unusability.
In this context, however, the question also arises as to how and which way the actual damage will be quantified in the event of damage to a thing and who will be liable. [10]
Other objective elements that an attacker committing a DoS and DDoS attack could commit in certain circumstances include Section 272 (General threat), Section 273 (General threat due to negligence) of the Criminal Code.
Regarding the possible criminal sanction of a perpetrator of DoS or DDoS attacks, it is also important to determine (identify) the offender of this particular crime. The question remains as to who should be criminally prosecutedas the offender who, for example, caused the unavailability of a certain service (e.g. web application).
Possibilities of criminal sanctions in Poland
In this case, Article 268 of the Criminal Code is applicable, stating that:
§ 1. Whoever, without being authorised to do so, destroys, damages, deletes or alters a record of essential information or otherwise prevents or considerably hinders an authorised person from becoming acquainted with it, shall be subject to a fine, the penalty of restriction of liberty or deprivation of liberty for up to 2 years.
Possibilities of criminal sanctions in Portugal
Such acts are clearly under the scope of Computer sabotage [Illegal interference] (Art. 5(1) of Cybercrime Law), possibly as aggravated offence in the case of high damage or interfering with critical infrastructures or other essential services (Art. 5(5).
[1] For more details, e.g. MARCIÁ-FERNANDÉZ, Gabriel, Jesús E. DÍAZ-VERDEJO and Pedro GARCÍA-TEODORO. Evaluation of a Low-rate DoS Attack Against Application Servers. Computers & Security, 2008, vol. 27, No. 7–8, pp. 335–354.
CARL, Glenn,Richard BROOKS andRai SURESH. Wavelet Based Denial-of-Service Detection. Computers & Security, 2006, vol. 25, No. 8, pp. 600–615
RAK, Roman and Radek KUMMER. Informační hrozby v letech 2007–2017. Security magazín, 2007, vol. 14, No. 1, pp. 3.
[2] For example, DoS attacks on the websites of the presidency, parliament, ministries, media outlets and two Estonian banks – Estonia (2007). Estonia recovers from massive DDoS attack. [online]. [cit. 4. 3.2010] Available from: http://www.usatoday.com/tech/news/techpolicy/2007-09-12-spammer-va_N.htmhttp://www.computerworld.com/s/article/9019725/Estonia_recovers_from_massive_DDoS_attack
[3] At this point it is necessary to mention Handshake – a process whose task is to set the parameters of a communication channel between two subjects before starting the actual communication. For example, a handshake is used on the Internet to open a TCP connection (the so-called “three-way handshake”, i.e. an exchange of three datagrams), and only then does the actual data transfer follow. Three separate steps are required to establish a TCP connection:
1. A party initiating the connection (client) sends a TCP segment with the SYN flag set.
2. A receiving party (server) responds with a TCP segment with the SYN + ACK flags set.
3. The client responds with a TCP segment with the ACK flag set.
Other TCP segments already have only the ACK flag set.
For more details, see e.g. TCP handshake krok za krokem. [online]. [cit.18.8.2016]. Available from: http://www.svetsiti.cz/clanek.asp?cid=TCP-handshake-krok-za-krokem-3122000
There are other ways of DoS attack, e.g. “TearDrop”, “Nuke”, “Peer-to-Peer attack”, etc. For more details cf. [online]. [cit.25.9.2010]. Available from: http://cs.wikipedia.org/wiki/Denial_of_Service
[4] It can also be a case where an attacker sends a hoax of type “on 6 June 2016 from 12 to 13, tickets will be free at Lufthansa! Click here for more information.”
[5] LOIC. [online]. [cit.18.8.2016]. Available from: https://i.ytimg.com/vi/QAbXGy0HbrY/maxresdefault.jpg
[6] HOIC. [online]. [cit.18.8.2016]. Available from: https://npercoco.typepad.com/.a/6a0133f264aa62970b0167612ea130970b-pi
[7] Suppression means the activity listed in Article 4 of the Convention on Cybercrime.
[8] If, for example, a PING flood is used for a DoS or DDoS attack, then it is possible to imagine the whole situation as the constant calling (and subsequent hanging up) to a specific telephone number. This will lead to a situation where the attacked phone number does not have the ability to make its own call (the call function is blocked), but none of the callers (attackers) will receive any data stored in the attacked phone.
[9] See Section 228 (1) of the Criminal Code:
“Whoever destroys, damages or renders useless another’s possesion and thus causes damage not insignificant to another’s property, shall be sentenced to imprisonment for up to one year, to prohibition of the activity or to forfeiture of a possession or other asset of value.”
Damage not insignificant means damage amounting to at least CZK 5,000 (see Section 138 (1) of the Criminal Code)
[10] Will every attacker be held accountable for this damage? Will responsibility for this damage be “divided” among the attackers?
