Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.6. Phishing, Pharming, Spear Phishing, Vishing, Smishing
4.6.1. Phishing
The term phishing is most often referred to as fraudulent or deceptive conduct, the aim of which is to obtain information about a user, such as username, password, credit card number, PIN, etc.
In a narrow sense, phishing is an action that requires a user to visit a fraudulent site (displaying, for example, an internet banking website, online store, etc.) and then fill in “login information”, or this information is required directly (e.g. when filling out a form, etc.).
In a broad sense, phishing can be defined as any fraudulent conduct that is intended to inspire confidence in a user, reduce his/her vigilance or otherwise force him/her to accept a scenario prepared in advance by an attacker. In this broad sense, the user is no longer required to fill in the data, but is provided with a message (or the user is redirected to a page) typically containing malware that collects the data. Furthermore, donor scams, etc. can be included in this broader sense.
In both cases, a user who is the target of a phishing attack is deceived. The difference lies mainly in the degree of interaction required of the user.
Phishing in essence is the use of social engineering. Phishing can also be done in the real world (see scams, etc.), but the virtual world allows an attacker to send fraudulent messages to a huge number of potential victims with minimal effort. Phishing can, with a great deal of exaggeration, be compared to “carpet bombing”. As with bombing, phishing it targets a relatively unspecified number of victims so that an attacker has hope of success. For example, in 2014, Google stated that a scam with really good phishing have 45% success rate in gaining user data. [1]
Phishing is not just about e-mails. It is possible to find phishing within instant messages (Skype, ICQ, Jabber, etc.), social networks, SMS and MMS messages, chat rooms, scams (fraudulent offers of job or goods, etc.), fake browser applications [2] , etc.
Phishing in a narrow sense
The principle of a “classic” phishing attack most often consists in sending a so-called phishing e-mail to an injured party, which at first glance does not raise any suspicion that it should be a fraudulent message. Such an e-mail usually includes a link that a user is prompted to click.
After clicking on the attached link, the user gets to a fraudulent website, which is almost impossible to distinguish in terms of appearance and function from the original correct web box. If it is an imitation of a website, through which it is possible to make payments, access secure accounts, manage such accounts, etc., then the data entered by the user are automatically sent to the attacker. [3] In this way, the attacker can obtain identification data of users of Internet banking services, access to individual bank accounts of users of infected systems, identification numbers and other data on payment cards with the help of which it is then possible to make payments in the Internet environment, etc.
An actual phishing attack takes place in several steps. [4]
1. Planning of a phishing attack
In this phase of a phishing attack, a target (user group) is selected and the method to be used for the attack is selected. What type of technical security the target uses is assessed, what are the risks of the attacker revealing his identity, etc.
2. Creating conditions for a phishing attack
At this stage, a technical solution to a phishing attack is taking place. An attacker obtains lists of e-mail addresses of users to whom a phishing e-mail is to be sent, a data box is created, where the system sends the acquired user data, a trusted message is created, which is then distributed to users.
3. Phishing attack
A phishing e-mail is delivered to individual users and, depending on the quality of processing of this e-mail and other factors (user experience, user’s awareness of phishing issues, anti-phishing software of the target, etc.), the data is sent to the attacker's data box. In this phase of a phishing attack, the user encounters a phishing e-mail for the first time.
As a pretext, information about a bug in the company's security system or another warning is often used, which should make the user trust the authenticity of this message. After activating the interactive link, the person is redirected to a website created by the attacker, faithfully copying the original page of the financial institution. The user is prompted to fill in login details, usually including the card number and PIN code. The completed data is sent to the address of the phisher, who then draws some or all of the funds from the account and thus causes a loss to the client (see the following figure).
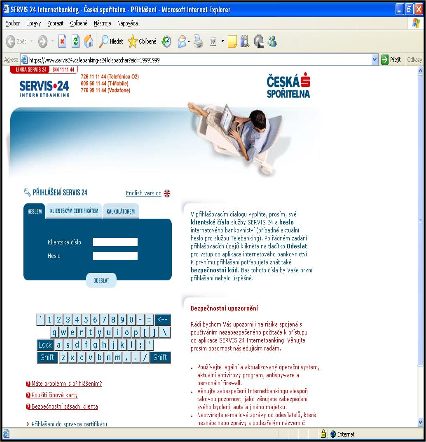
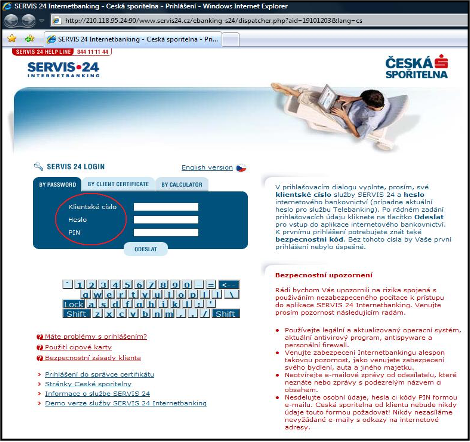
Original page (left) and fraudulent page (right)
4. Data collection
The attacker obtains data that was entered by individual users of the compromised system in a fake website environment.
5. Withdrawal of funds or other profits from a phishing attack
Using the obtained data, the attacker enters the actual bank accounts of individual users and withdraws funds. By transferring to other, especially foreign accounts, diluting these funds and using other techniques, the withdrawn funds become virtually untraceable.
It is very difficult to determine how many phishing attacks are carried out worldwide each day. It is also problematic to determine how many clients of compromised companies respond to a phishing e-mail. The rate of return is estimated to be between 0.01 and 0.1%.
Forecasts in 2007 estimated that “classic” phishing scams or campaigns would increase in the future. [5] These forecasts have been fulfilled in part, as the number of “classic” phishing campaigns is declining, but phishing in a broad sense is on the rise [6] , especially its new modifications or linking phishing with other types of attacks (malware, botnet, etc.).
Phishing in a broad sense
As part of demonstrating phishing in a broad sense, I will present four campaigns that took place in the Czech Republic and were more or less successful. Of course, these attacks are not the only phishing attacks in a broad sense that took place in the Czech Republic. The reason for choosing these four specific attacks is the fact that I want to point out in particular the innovative approach of the attacker and the appropriate combination of technical attack with social engineering. Specifically, the attacks are:
1. Debt/Bank/Execution
2. Czech Post (Českápošta)
3. Christmas and gifts
4. Seznam.cz – One Time Password
4.6.1.1. Debt/Bank/Execution [7]
A phishing campaign professionally called DBE hit the Czech Republic on a massive scale in 2014 (with the reverberations of this campaign lasting at least until the end of 2015). The attack itself was very precisely prepared and included both a phishing and a distribution of malware (to computers and mobile devices). The whole attack can be divided into the following phases:
1. Phishing campaign
2. Installation of malware to a computer
3. Access to online banking
4. Installation of malware to a mobile device
5. Transfer and withdrawal of funds
Ad 1) Phishing campaign
The first prerequisite for attackers to be able to successfully obtain money was a large phishing campaign to which a sufficient number of people would respond. The actual distribution of fraudulent e-mails has been broken down into three successive waves of phishing messages:
I. Debt (debt@....); March–April 2014
II. Bank (bank@....); May–June 2014
III. Execution (emissions@...); July–September 2014
Within the individual campaigns, there was an increase in the “quality” of their own e-mail messages and, in particular, a better use of social engineering in relation to the presumed victims in the target region, i.e. the Czech Republic. However, all of the above phishing campaigns had at least two features in common. First, it was the fact that the attachment in the sent e-mail always contained a file that looked like a text document but was an executable file, specifically malware: Trojan. [8] The second common feature was that social engineering took advantage of the concerns of the addressed individuals from possible litigation, in the latter case from execution.
The first wave of phishing attacks used very bad Czech.It was sent out from various, not entirely trusted domains when it comes to debt collection, registered in the Czech Republic (e.g. micik.cz or dhome.cz etc.). Various names of persons and existing telephone numbers were used, traceable on the Internet (the person owning this number ultimately had nothing to do with the attack).
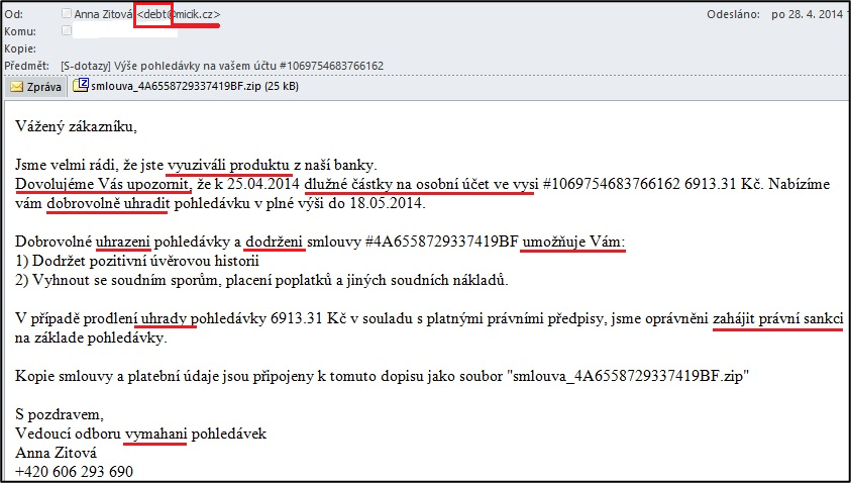
Fraudulent e-mail sent as part of the Debt wave
In the second wave, the Czech language used improved.
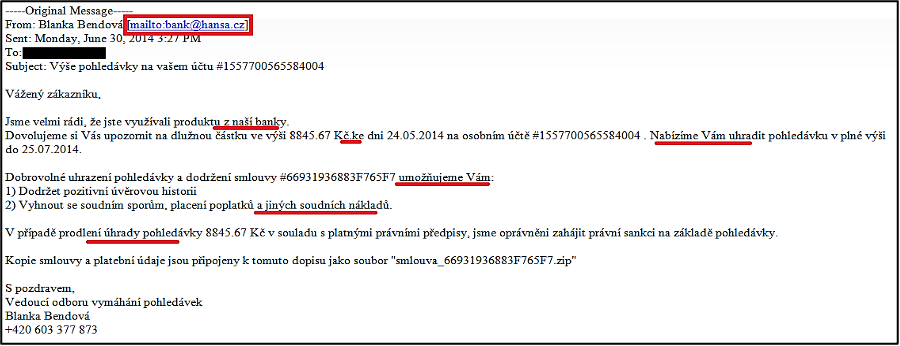
Fraudulent e-mail sent as part of the Bank wave
At the time these phishing attacks began to appear, various security organisations and CSIRT teams [9] , as well as mass media, published warnings including instructions on how to handle such reports. [10]
Both campaigns were relatively successful, but the most successful was the attack where the fraudulent e-mail was a warning (call) from an executor.
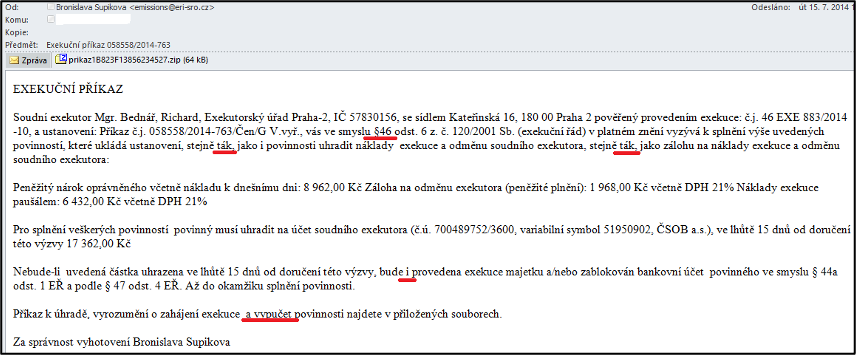
Fraudulent e-mail sent as part of the Execution wave
The Czech language used in the “execution order” especially contained errors in use of diacritics, or some sentences were formulated in a less than natural style. (The most obvious errors are underlined.) However, the names of real executors were used, traceable on the Internet (said executor had nothing to do with the attack), as well as the real-looking numbers of executions.
Ad2) Installation of malware to a computer
As mentioned earlier, all phishing campaigns included malware in the attachment of the sent e-mail: TrojanDownloader (i.e. malware designed to download other malware). This malware was primarily created and targeted at the Windows XP operating system, which was discontinued in March 2014.
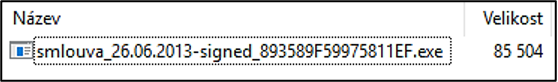
Executable file (malware) contained in the attachment to the fraudulent e-mails
After running the attachment, “Tinba” malware (bank Trojan horse) was installed, which was downloaded from the Internet in the background, while a contract or an execution order in a text editor was shown to a user. [11]
The malware was written to the directory: Users/specific user/AppData/Roaming/brothel. In this directory, it was possible to find ate.exe, which is a file that was created after opening the executable file in the phishing e-mail. At the same time, an appropriate key was created in the registry in the HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun branch. In this way, it was possible to verify whether this was malware resulting from this attack.
Ad3) Access to online banking
The next step of the attacker was to wait for the moment when the victim logs in to online banking. The malware on the computer is able to record communication between the user and online banking, and an attacker has the ability to monitor this communication. The user barely had a chance to detect the attack because the URL in the browser belonged to the bank and the communication was secure (HTTPS).
"The actual theft of sensitive data takes place by inserting malicious code into the official websites of banks. Configuration scripts are downloaded from C&C servers (machines belonging to attackers, used to control the botnet) and decrypted as described above. What is interesting is the reuse of the same format of configuration files of the well-known bank Trojans Carberp and Spyeye. For each botuid (a unique value that identifies the user's environment), a list of usernames and passwords is stored on the C&C server. Additional scripts are downloaded depending on the bank used, either hXXps://andry-shop.com/gate/get_html.js;hXXps://andry-shop.com/csob/gate/get_html.js; or hXXps://yourfashionstore.net/panel/a5kGcvBqtV, which will be downloaded if the victim visits the websites of Českáspořitelna, ČSOB, or Fia.“ [12]
Ad 4) Installation of malware to a mobile device
The next step of the attacker was to convince users of the need to increase security when accessing online banking. The reason for the warning issued by the alleged bank (actually an attacker-controlled website) was to “increase” the security of the connection. The victim was offered a page with a choice of mobile device operating systems (Android, Windows Phone, Blackberry and iPhone OS), but only the Android version allowed the download of malware to the phone. The attackers chose various ways of distributing malware to a phone, from simply sending an SMS message with a link from which a user was meant to download the program, to sending an SMS message and a QR code. [13]
|
The text of the message: CS-S24 Download a security from Bit.ly/Tp9JjU |
The malware downloaded and installed on the mobile device was detected by Avast! as Android: Perkele-T.

Downloading malware to the phone
The purpose of this malware was to gain access and full control over the secondary authentication means (two-factor authentication), which in most cases is the mobile phone. If a user was using an operating system other than Android, they received a message: “Please try again later.”
Ad5) Transfer and withdrawal of funds
The next step of the attacker was to draw funds from the attacked account and sent them to the account of white horses, who were then to withdraw cash or transfer it to other accounts. Due to full control (using malware) of both Internet banking access data (see infected computer) and control of the secondary authentication device (see infected mobile phone – when authentication messages were forwarded to the attacker without being seen by the victim), the attacker could enter a “legitimate” money transfer order.
According to a report from Avast!, Russian-speaking attackers were behind this attack. SMS messages from the infected phone were forwarded to the number 79023501934, which was registered in the Astrakhan region, Russia. [14]
4.6.1.2. Czech Post (Česká pošta)
The second major phishing attack began in November 2014 and continued until December 2014. At the beginning of the attack, there was a phishing e-mail with a “Czech Post” (Českápošta) notification that you were not found as the addressee of a shipment and that you should download the shipment information. The Czech language used in this phishing e-mail is one of the worst you can come across in phishing. Apparently one of the automatic translators from the Internet was used to generate this e-mail.
The fraudulent e-mails were sent from addresses that do not belong to Czech Post. These were, for example, addresses: upport@cs-post.net, tracktrace@cs-post.net, cpost@cs-post.net, post@cs-post.net, zasilka@cs-post.net, which due to the domain cs-post could arouse a user's belief that this is a Czech Post site. However, it should be noted that cs-post was registered in the .net domain, while the actual pages of the Czech Post (Českápošta) are registered in the .cz domain (see https://www.ceskaposta.cz).
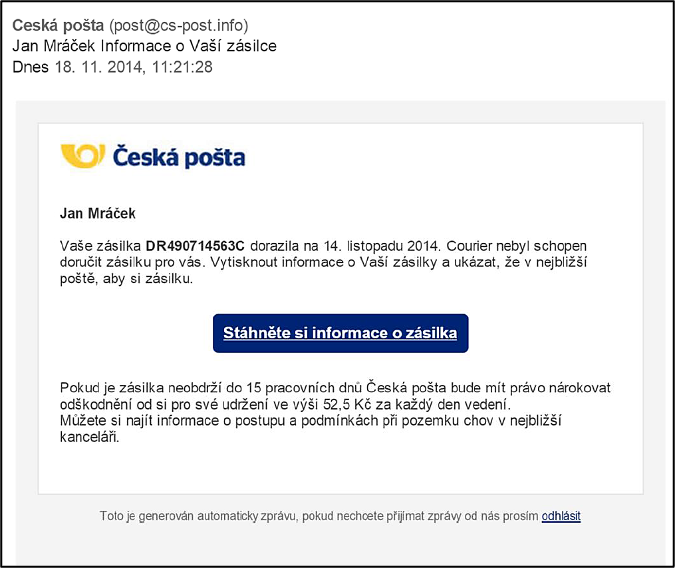
Fraudulent e-mail from “Česká pošta”
If a user clicked on the box: Download information about the shipment, he/she was redirected to pages that resembled the actual pages of the Czech Post (Českápošta). Here, a user was asked to enter a security code (Captcha) and was then allowed to download a .zip file that contained “tracked shipment information”. As in the previous phishing campaign, an executable file (ransomware) was stored in the attachment, but the purpose was to encrypt a user's data.
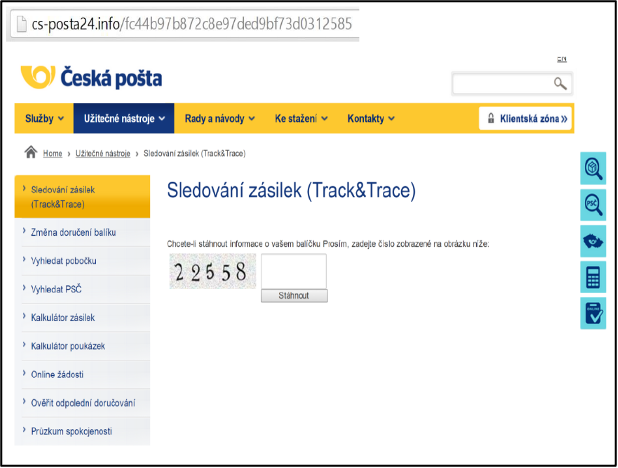
Fraudulent site of the “Czech Post” (Českápošta)“
After encrypting the data, a user was prompted to pay for a key that was able to decrypt the encrypted files. The prompt has already been written in a much better version of Czech. The user could also learn some answers to some questions that may have bothered him/her.
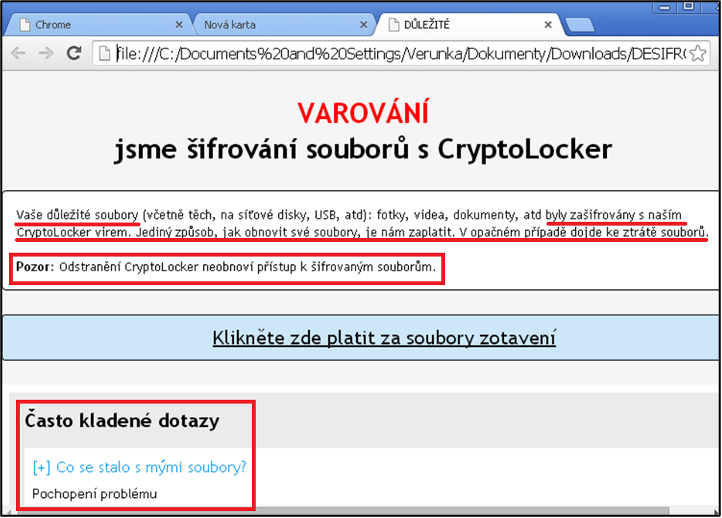
Information that was displayed to the user after encrypting his/her data
Data recovery at that time cost 1.09 BTC, and in addition to the conversion to Czech crowns, the user was shown detailed instructions on how to set up a bitcoin wallet, where and how to buy bitcoins and where to send them.
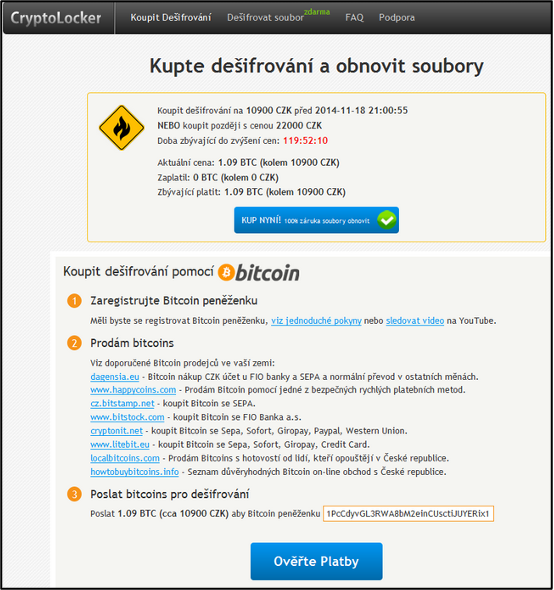
Instructions on how to decrypt your files [15]
The attack is specific in that it added ransomware to a phishing campaign, which immediately began encrypting a user's data, and in that a pre-Christmas period was used to carry out the attack, in which many people wait for shipments to be delivered. Due to these two factors, the attack was very successful.
4.6.1.3. Christmas and gifts
Another major phishing attack began during December 2014 (specifically during the Christmas period) and continued in January 2015. This attack was divided into two phases. In the first phase, users were sent e-mail wishes with a Merry Christmas via an electronic postcard. In the second phase, messages confirming an order for electronics were sent during January. The message informed a user that he/she had purchased goods (e.g. printer, hard drive, camera, etc.) for which he/she had paid in advance with a payment card, referring to the invoice in the attachment.
Both attacks have a common element, which is the malware contained in an e-mail attachment. Specifically, it was a Trojan horse (Kryptik), which was presented as a screen saver. This malware was, as in the case of the attack mentioned in chap. 4.6.1.1Debt/Bank/Execution compressed in a .zip file. After unpacking the .zip file, many users did not consider the .scr [16] file to be executable and thus infected their own computer.
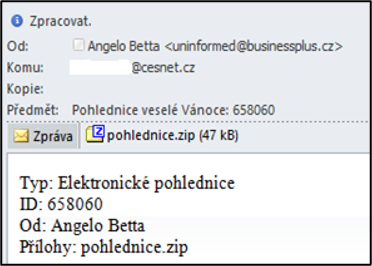
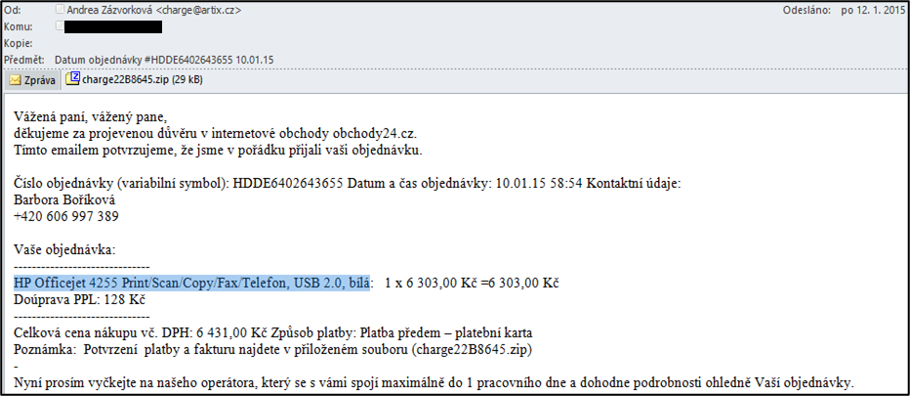
Samples of postcard and shop phishing messages
The attack is specific in that it used a type of file that many users do not consider dangerous, and the timing of the attack. Thanks to various chain e-mails, users have become accustomed to opening electronic postcards or attachments that look like this, without more thorough checking of the content. The second attack was planned so that a user check if he/she had not actually ordered any goods that were not delivered to him/her due to the Christmas holidays.
4.6.1.4. Seznam.cz – One Time Password
The latest phishing attack demonstrates a significant change in attackers' tactics. An attacker still takes advantage of the fact that malware has infected a computer. An attacker can control this computer himself or rent it out, for example, as part of a botnet. The actual infection could have occurred, for example, through another incoming e-mail, when visiting infected sites, or otherwise. The attacker's goal in the case of Seznam – One Time Password [17] was to gain control of the user's mobile phone.
The malware that was installed on a computer prompted a user to log in to the Seznam.cz e-mail box to install a tool for easier and safer work with their mailbox on their mobile phone. A user is then guided step by step through installing the SeznamOTP application from an untrusted source. At the end of the installation, a user is provided with his/her “unique licence key”. In reality, however, a user has installed malware on his/her mobile phone.
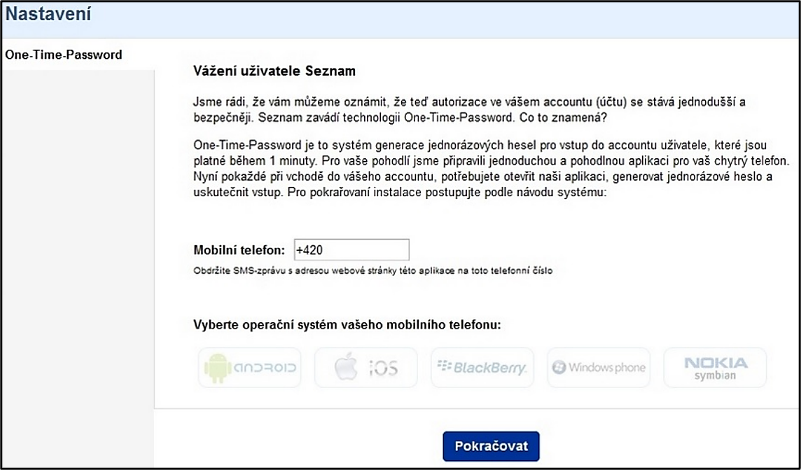
Welcome screen of SeznamOTP installation [18]
The risk of this last phishing attack is that the “phishing message” was not delivered via e-mail or other means of communication, but was displayed to a user only in a specific situation (in this case after logging in to the seznam.cz mailbox) and the initiator of this message was malware found on an already infected computer. The second risk factor is the fact that the security request is not linked to a bank account. Therefore, a user may not be aware of the dangers of installing this application.
In the Czech Republic, it is possible to punish conduct that has the nature of “classical phishing” according to Section 209 (Fraud) of the Criminal Code. The fraud is completed by enrichment. A creation of a replica of a website and the acquisition of login names and passwords could then be qualified as a preparation or attempt of a criminal offence according to Section 209 of the Criminal Code. Obtaining access data, including account numbers, payment card numbers and PIN codes without their further use, will not be a criminal offence.
Possibilities of criminal sanctions in the Czech Republic
In the case of combined forms of phishing attacks, where malware is used to infect a computer, such conduct of an offender must also be punished in accordance with Section 230 (Unauthorised access to the computer system and information carrier) of the Criminal Code.If the aim of the phishing attack is to gain an unjustified benefit for oneself or another, it is also possible to apply the provisions of Section 230 (3) of the Criminal Code.
In specific cases, it would be possible to use the provisions of Section 234 (Unauthorised measures, counterfeiting and alteration of the means of payment) of the Criminal Code.
Possibilities of criminal sanctions in Poland
Breach of the secret of communication (sniffing) - art. 267 § 3 of the Penal Code. This type of crime consists in obtaining proprietary information, e.g. through sniffers, i.e. programs that intercept data (passwords and user IDs). Such an act is punishable by up to 2 years imprisonment.
Article 267 Unlawful obtaining of information
§ 1.Whoever, without authorisation, gains access to information not intended for him, by opening a closed letter, connecting to a telecommunications network or breaking or bypassing an electronic, magnetic, IT or other specific protection thereof, shall be subject to a fine, the penalty of limitation of liberty or deprivation of liberty for up to 2 years.
§ 2.The same punishment shall be imposed on anyone, who without authorisation, gains access to the whole or any part of an information system.
§ 3. The same punishment shall be imposed on anyone, who in order to obtain information to which he is not entitled, establishes or uses an eavesdropping or visual device, or other device or software.
§ 4. The same punishment shall be imposed on anyone, who discloses information obtained in the manner specified in § 1-3 to another person.
§ 5.The prosecution of the offence specified in § 1-4 shall occur on the motion of the injured person.
Possibilities of criminal sanctions in Portugal
Being the dissemination of malware criminalised (Art. 6(2) of the Cybercrime Law), as mentioned, in itself, the creation of inauthentic data would be considered an offense as Computer-related forgery (Art. 3 of the Cybercrime). Besides, if the purpose of such creation has a fraudulent or dishonest intent of procuring, without right, an economic benefit for oneself or for another person, on the expenses of the victim, it would also be considered a Computer-related fraud (Art. 221(1) of the CriminalCode).
In addition, the counterfeiting of cards and other non-cash means of payment, including the misuse of devices, is punished as aggravated offences (Art. 3-A to 3-F of the Cybercrime Law).
On the other hand, being within the scope of Law No. 52/2003, on the fight against terrorism, computer-related forgery and computer-related fraud would be considered as aggravated offences.
4.6.2. Pharming
Pharming [19] is a more sophisticated and dangerous form of phishing. This is an attack on a DNS (Domain Name System) server, which translates a domain name into an IP address. The attack occurs when a user enters an address of a web server he/she wants to access in an Internet browser. However, it will not link to the appropriate IP address of the original web server, but to a different, spoofed IP address. Websites at a fake address usually very faithfully imitate the original pages. They are practically indistinguishable from them. A user then enters his/her credentials that an attacker obtains. This attack is usually carried out when a user accesses Internet banking sites.
“Fake websites can be used to install viruses or Trojan horses on a user's computer, or they can be used by attackers to try to obtain personal or financial information, which can then be misused to steal identity. Pharming is a particularly dangerous form of cybercrime, because in the case of an infected DNS server, a user can become a victim even if no malware is installed on their computer at all. Even if you use precautionary measures, such as entering Internet addresses manually or using only trusted bookmarks, you are not protected against this type of attack, because unwanted redirection only occurs after the computer sends a connection request.” [20]
The other typical way of pharming is to attack an end user's computer with malware, where a lower level of security can be expected. This malware changes the hosts file to divert traffic from the intended destination and redirect users to a fake website.
Criminal sanctions are similar to those in the case of phishing.The same according to Portuguese and Polish law.
4.6.3. Spear Phishing
Spear phishing is one of the forms of phishing attack, but with the difference that spear phishing is a precisely targeted attack, unlike phishing, which is a rather widespread (random) attack. The target of an attack is usually a specific group, organisation or individual, specifically information and data contained in this organisation (e.g. intellectual property, personal and financial data, business strategies, classified information, etc.).
The difference between spear phishing and classic phishing is in who is the sender of the messages in question. At the beginning of an attack, it is the attacker who uses open sources to find out as much information as possible about the attacked organisation, its structure, etc. He also creates a high-quality e-mail or other message and begins to communicate with a person from within the organisation as a colleague. The attacker will then use this person as a means of spreading other messages (e.g. infected malware) within the organisation. As the person who is “known” to the victims, he has no problem communicating with the victims, who verifies the attacker’s messages less, if at all. [21]
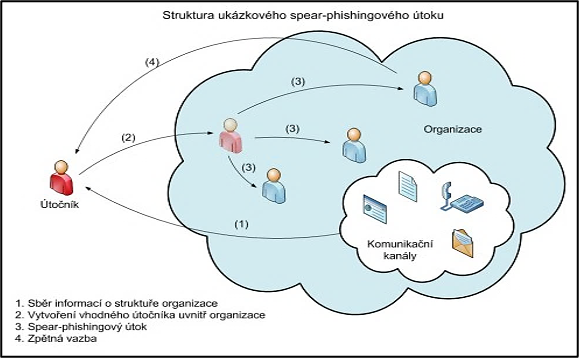
Structure of a spear-phishing attack [22]
Text on the figure:
The structure of a sample spear-phishing attack
Attacker – Organisation – Communication channels
1. Collection of information about the structure of an organisation
2. Creating a suitable attacker within the organisation
3. Spear-phishing attack
4. Feedback
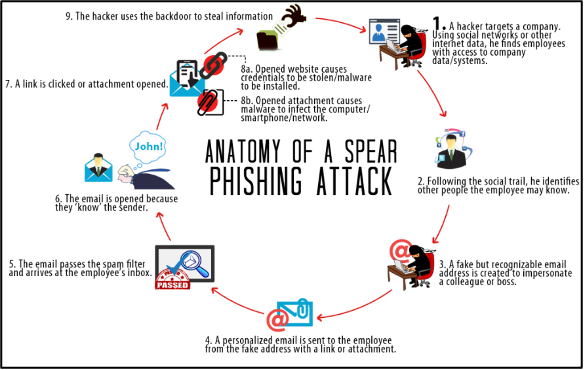
The course of a spear phishing attack [23]
Possibilities of criminal sanctions in the Czech Republic
A spear phisher's punishment is similar to that of phishing. For example, a terrorist organisation may be behind a spear phishing attack. In this case, liability for a criminal offence under Section 311 (Terrorist attack) of the Criminal Code is not ruled out.
Possibilities of criminal sanctions in Poland
The same laws apply as those for phishing.
Possibilities of criminal sanctions in Portugal
The conclusion being the same as for phishing in general, including those related to terrorism.
4.6.4. Vishing
The term vishing [24] refers to telephone phishing, in which an attacker uses a social engineering technique and tries to lure sensitive information from a user (e.g. account numbers, login details – name and password, payment card numbers, etc.). The attacker is deliberately trying to falsify his/her identity. Attackers often present themselves as representatives of real banks or other institutions in order to arouse as little suspicion as possible in a user. Vishing is used in VoIP (Voice over Internet Protocol) telephony.
4.6.5. Smishing
Smishing [25] works on a similar principle as vishing or phishing, but uses SMS messages to distribute messages. As part of smishing, it is primarily an attempt to force a user to pay an amount (for example, call a toll-free line, send a donor SMS, etc.) or click on suspicious URL links. If a user visits the URL, he/she is redirected to a page that exploits certain vulnerabilities in the computer system, or the user is prompted for sensitive information or malware. [26]
Example of smishing:
“Warning – this is automatically generated message from (local bank name), your credit card has been blocked. To reactivate, call 866 ### ###“
Possibilities of criminal sanctions in the Czech Republic
Criminal sanctions of vishing and smishing are similar to those in the case of phishing.
Possibilities of criminal sanctions in Poland
The same laws apply as those for phishing.
Possibilities of criminal sanctions in Portugal
Also in this case, the conclusions regarding criminalisation is the same as for phishing in general, including those related to terrorism.
[1] See e.g. Google says the best phishing scams have a 45-percent success rate. [online]. [cit. 14.8.2016]. Available from: https://www.engadget.com/2014/11/08/google-says-the-best-phishing-scams-have-a-45-percent-success-r/
Phishing by the Numbers: Must-Know Phishing Statistics 2016.[online]. [cit. 14.8.2016]. Available from: https://blog.barkly.com/phishing-statistics-2016
[2] See e.g. Beware of Fake Android Prisma Apps Running Phishing, Malware Scam [online]. [cit.14.8.2016]. Available from: https://www.hackread.com/fake-android-prisma-app-phishing-malware/
[3] LANCE, James. Phishing bez záhad. Prague: Grada Publishing, 2007. p. 45.
[4] WILSON Tracy, V.How Phishing Works.[online]. [cit.14.8.2016]. Availablefrom: http://computer.howstuffworks.com/phishing.htm
[5] The development trends of phishing – see also e.g.DODGE, Ronald. C., Curtis CARVE and Aaron J. FERGUSON. Phishing for User Security Awareness. Computers & Security, 2007, vol. 26, No. 1, pp. 73–80.
[6] According to the following study, phishing has increased by 250% in the last 6 months. See Phishing Activity Trends Report. [online]. [cit.14.8.2016]. Available from: https://docs.apwg.org/reports/apwg_trends_report_q1_2016.pdf
[7] Hereinafter referred to as DBE.
[8] For more details see results from Virustotal. [online]. [cit. 15.8.2016]. Availablefrom:
[9] Computer Security Incident Response Team. For more details, see e.g.: https://www.csirt.cz/
[10]
See e.g. Pozor na zprávu o údajné
neuhrazené pohledávce - jedná se o podvod. [online]. [cit.15.8.2016].
Available from: https://www.csirt.cz/page/2073/pozor-na-zpravu-o-udajne-neuhrazene-pohledavce---jedna-se-o-podvod/
Znovu se
objevily podvodné zprávy. [online].
[cit.15.8.2016]. Availablefrom: https://www.csirt.cz/news/security/?page=97
PODVODNÉ EMAILY hrozí exekucí, nic neplaťte a neotvírejte![online]. [cit.15.8.2016]. Availablefrom:
Pozor na zprávu o výzvě k úhradě před exekucí - jedná se o podvod. [online]. [cit.15.8.2016]. Available from: https://www.csirt.cz/news/security/?page=87
Čo sa skrýva v prílohe podvodných e-mailov?[online]. [cit.15.8.2016]. Available from: https://blog.nic.cz/2014/07/23/co-sa-skryva-v-prilohe-podvodnych-e-mailov-2/
[11] For more details see the analysis of Tinba malware functionality: W32. Tinba (Tinybanker). [online]. [cit.15.8.2016]. Available from: https://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp_w32-tinba-tinybanker.pdf
[12] HOŘEJŠÍ, Jaromír. Falešný exekuční příkaz ohrožuje uživatele českých bank.[online]. [cit.15.8.2016]. Available from: https://blog.avast.com/cs/2014/07/17/falesny-exekucni-prikaz-ohrozuje-uzivatele-ceskych-bank-2/
[13] Ibid. – image with captcha code.
[14] HOŘEJŠÍ, Jaromír. Falešný exekuční příkaz ohrožuje uživatele českých bank.[online]. [cit.15.8.2016]. Available from: https://blog.avast.com/cs/2014/07/17/falesny-exekucni-prikaz-ohrozuje-uzivatele-ceskych-bank-2/
[15] Sledování zásilky České pošty aneb nová havěť.[online]. [cit.14.8.2016]. Available from: http://www.viry.cz/sledovani-zasilky-ceske-posty-aneb-nova-havet/
[16] SCR files are executable files.
They are primarily assigned with the Unknown Apple II File program (found on Golden Orchard Apple II CD Rom). The following are also assigned: Windows Screen Saver, Image Pro Plus Ver. 1.x - 4.5.1.x Macro (Media Cybernetics Inc.), TrialDirector Script File (inData Corporation), Screen Dump, Screen Font, StatisticaScrollsheet, Procomm Plus Screen Snapshot File, Movie Master Screenplay, Mastercam Dialog Script File (CNC Software Inc.), Sun Raster Graphic, LocoScript Screen Font File (LocoScript Software), Faxview Fax, DOS DEBUG Input File, Script a FileViewPro.
Co znamenápříponasouboru SCR.[online]. [cit.14.8.2016]. Available from: http://www.solvusoft.com/cs/file-extensions/file-extension-scr/
[17] Hereinafter referred to as the SeznamOTP
[18] More information about this malware and the course of the entire attack can be found, for example, at: Podvodníciměnítaktiku. Našlinovoucestu, jak vybílitlidemúčty. [online]. [cit.14.8.2016]. Available from: https://www.novinky.cz/internet-a-pc/bezpecnost/364094-podvodnici-meni-taktiku-nasli-novou-cestu-jak-vybilit-lidem-ucty.html
[19] It is a combination of words farming and phreaking.
[20] For more details see Co je pharming? [online]. [cit.14.8.2016]. Available from: http://www.kaspersky.com/cz/internet-security-center/definitions/pharming
[21] “An attacker chooses an organisation working with valuable information, analyses the website to obtain information about the personnel structure, employees and procedures (for more detailed information about employees, such an attacker can use their private pages and discussion forums) and in the next step, the attacker creates a report whose content, form and appearance mimics internal communication in the organisation. Then the attacker asks an employee to provide sensitive information for access to the computer network."
Evoluční teorie v podání spearphishingu. [online]. [cit.15.2.2010]. Availablefrom: http://connect.zive.cz/content/evolucni-teorie-v-podani-spear-phishingu
[22] Ibidem
[23] Tip of the month July 2016 – Avoid getting hooked by Phishing. [online]. [cit.14.8.2016]. Available from: http://www.intermanager.org/cybersail/tip-of-the-month-july-2016-avoid-getting-hooked-by-phishing/
[24] It is a combination of words “voice” and “phishing”.
[25] It is a combination of words “SMS” and “phishing”.
[26] E.g. Xshqi – Android Worm on Chinese Valentine’s day. [online]. [cit.14.8.2016]. Available from: https://securelist.com/blog/virus-watch/65459/android-worm-on-chinese-valentines-day/
Selfmite – Android SMS worm Selfmite returns, more aggressive than ever. [online]. [cit.14.8.2016]. Available from: http://www.pcworld.com/article/2824672/android-sms-worm-selfmite-returns-more-aggressive-than-ever.html
