Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.5. Spam
From the point of view of information and communication technologies, the content of the term spam can in principle be understood on two levels. In a narrow sense, it is the mass dissemination of unsolicited communication, most often of an advertising nature via the Internet, and most often through electronic communication. In a broad sense, all unsolicited received messages, i.e. also messages containing viruses, Trojan horses, etc. [1] are spam.
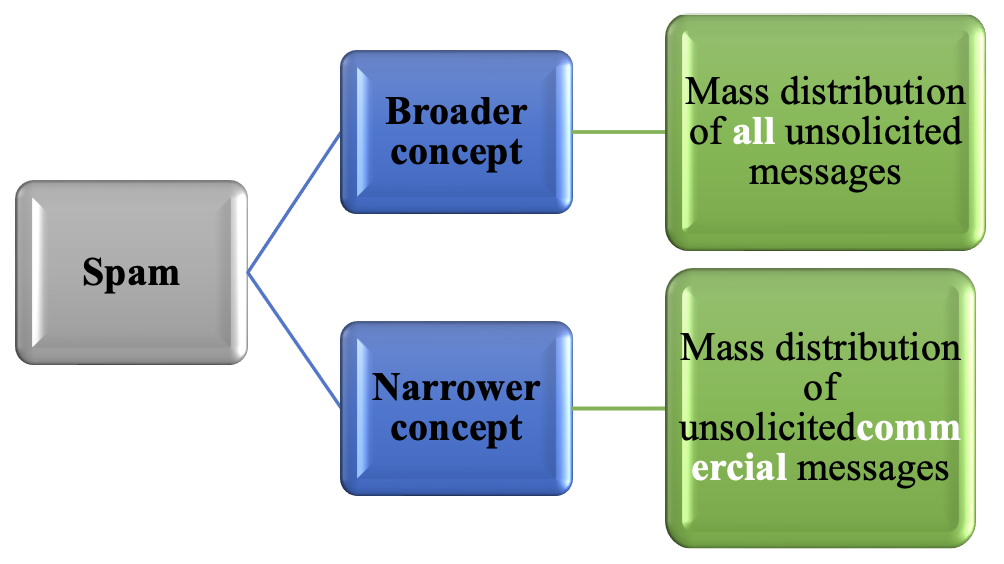
Scheme – Division of spams
It is characteristic of spam that it is a message that is sent electronically, in bulk and especially without request.
Spam uses various communication channels to send unsolicited messages:
· e-mail;
· othermessenger (ICQ, Skype, etc.);
· SMS, MMS;
· discussion forums, blogs, social networks, etc.;
· gaming platforms, etc.
Spam can contain information:
· commercial or advertising;
· on health and medicine (This category includes spam offering weight loss products, cosmetics, non-traditional medicine, medicines not available in the region, etc.);
· financial (In particular, these are offers of various loans, the possibility of extra income, etc.);
· pornographic (This spam either offers various pharmaceuticals to increase sexual potency, or links to sites with pornographic content.);
· educational (offers of various courses, trainings, etc.);
· hoax (chain letter);
· political;
· religious;
· criminal (this category includes messages containing, for example, malware, or linking to sites with malicious code, etc.)
There are currently a large number of statistics showing different numbers of spam in e-mails. For example, Jirovský states that more than 90% of spam in e-mail can be expected. In 2006, an average of 14.5 billion spam messages were sent per day. [2] Due to this, many organisations dealing with spam and providing tools to protect against it have emerged. One of these companies was TrustedSource [3] , where the following graph comes from. It shows the portion of spam in e-mails from 2005 to 2010. The blue line shows the number of e-mail messages and the red field reflects the number of e-mail spams (both are given in billions).
Regardless of the exact percentages, this type of unsolicited messages currently makes up the majority of all e-mail messages received. [4] However, because of a number of technical measures on the part of individual ISPs, the user receives a minimum of messages that represent spam.
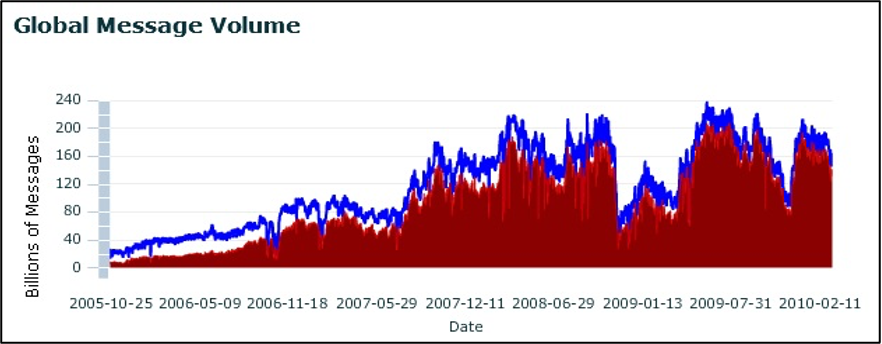
Spam development from 2005 to 2010
The significant drop in spam at the end of 2009 is due to the closure of McColo's Internet spam business. [5]
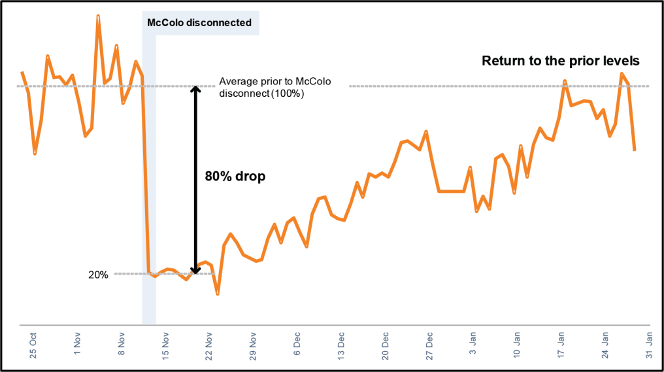
Development of spam after McColo ceased operations in November 2008
Spam interferes with electronic communication, often makes it completely impossible (the information structure is overwhelmed) and thus reduces society's confidence in information technology. However, if spam is restricted, the right to freedom of expression is practically restricted in favour of the right to the protection of personal integrity.
Even for the reason described above, the legal sanction of a spammer is quite complicated and at present the institutes of civil and administrative law are used, as criminal law does not allow to punish a spammer.
Spam containing criminal or other fraudulent content is referred to as scam. Scams currently form a significant part of spam and their purpose is, typically using social engineering, to gain a user's trust and force him/her to perform some required actions (e.g. opening an e-mail attachment, visiting the displayed URL, etc.). Scams include phishing, malware, 419, hoax, fraudulent lotteries and offers, donor scam, cold-call scamming, Facebook like scam, etc.
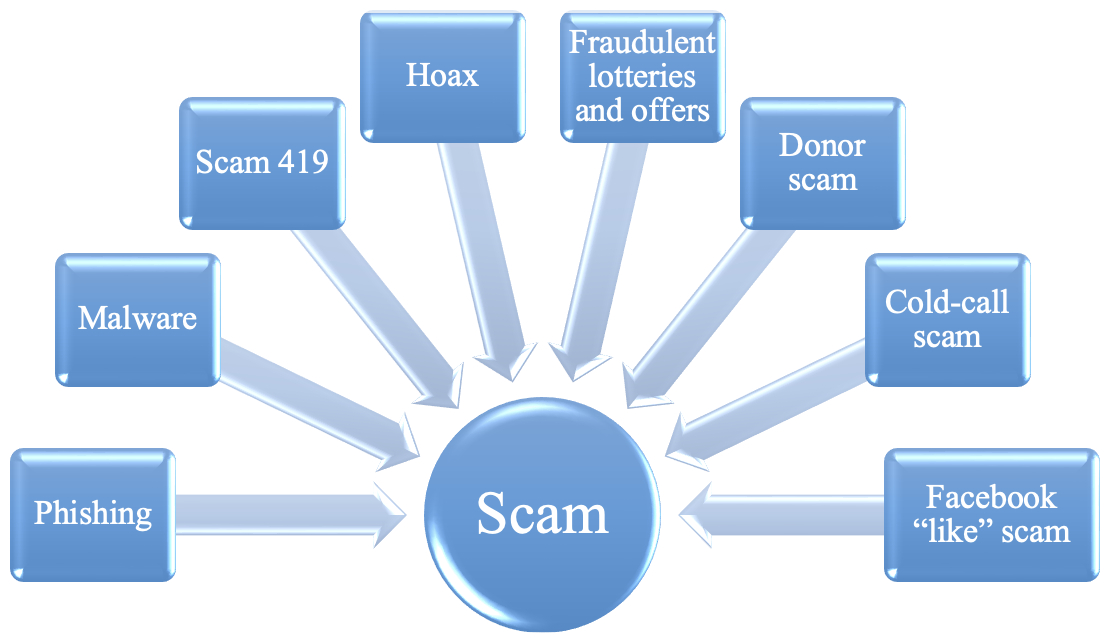
Types of scam scheme
At this point, I will focus primarily on three types of scam, namely Scam 419, Hoax and Fraudulent Offers.
4.5.1. Scam 419
Scam 419 is a designation for e-mails, better known as Nigerian Letters. These scams are an example of the transmission of normal crime (fraud) from the real world to the virtual world.
For the sake of interest, we enclose three very different reports having the nature of Scam 419.
Report No. 1 – “You have inherited a huge amount of money”
Hi dear,
I am a lawyer Victoria Josef, I have a message for you concerning my deceased client who bears the same surname as you, I am aware, may not be related to him blood, but is a national in your country who lost his life alongside his immediate family duringaccident here in Togo engine.
He left for an amount of $ 2,700,000, meanwhile, his bank wants to transfer the benefits to one of his extended family members as the presentation can be made through my office. To be honest, this money belongs to my deceased client, who has the same surname and nationality lived with you and worked here in Togo for more than 20 years as a contractor, but died in a fatal car accident along with all members of his family in 2009 and recently, the bank where this money is stored gave me a mandate to provide some member of his family to demand this money or else it will be passed to the government treasury account as abandoned money.
I don't want that to happen, but the problem is that his supposed closest relatives died in this same car accident and all his efforts to trace his family members since his death have been unsuccessful in disputing when he never introduced some of them to me while he was alive.
Friend,
that's why I embarked on this mission to find someone to work from hand to hand
with me claiming this fund to help our families and the needy, instead of
allowing these corrupt government officials to take over this hard-earned
money, just like that and scatter it, leaving the poor masses to suffer. For me
to pick up on you among the millions of people on Facebook; Just mean it's God
who made our way upset, so let's work together with one mind as we share the
money the way he claimed it.
Please indicate your interest in this statement so that I can provide you with
regard to work and guidelines.
Attorney Victoria Joseph Esq.
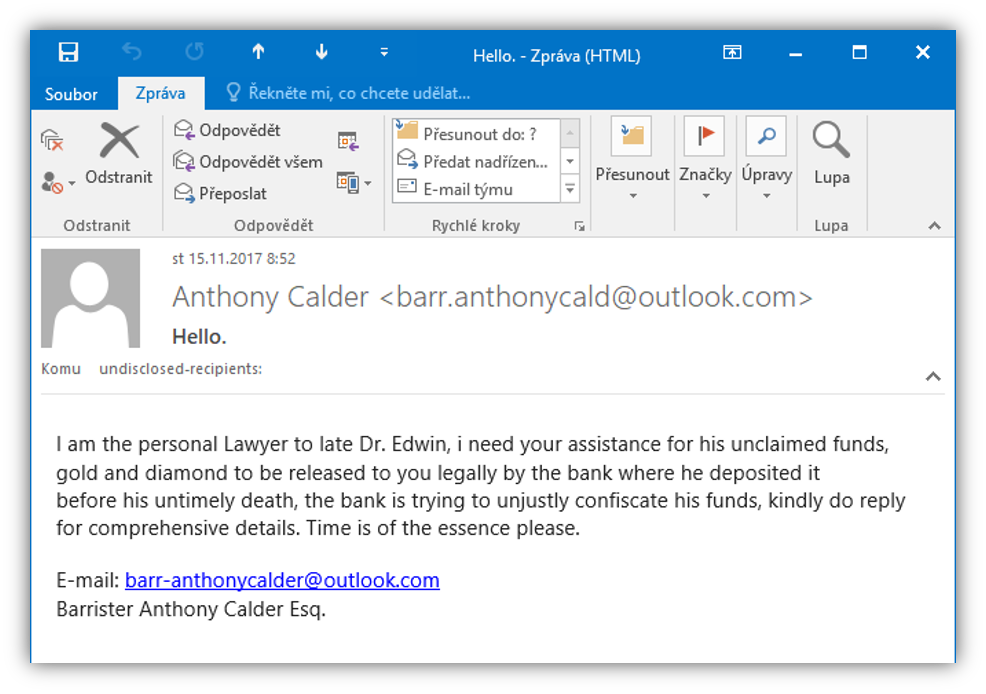
Message No. 2 – “I fell in love”
Hello Darling,
My name is Joe Anita I'm a woman, I found out his identity on the side, and I want to learn that we know more about each other and share social life with culture, and I have nothing to say, so please reply me, so I send my data to you and I will say more about myself in my paintings. Thank you very much.
Your joy Anita
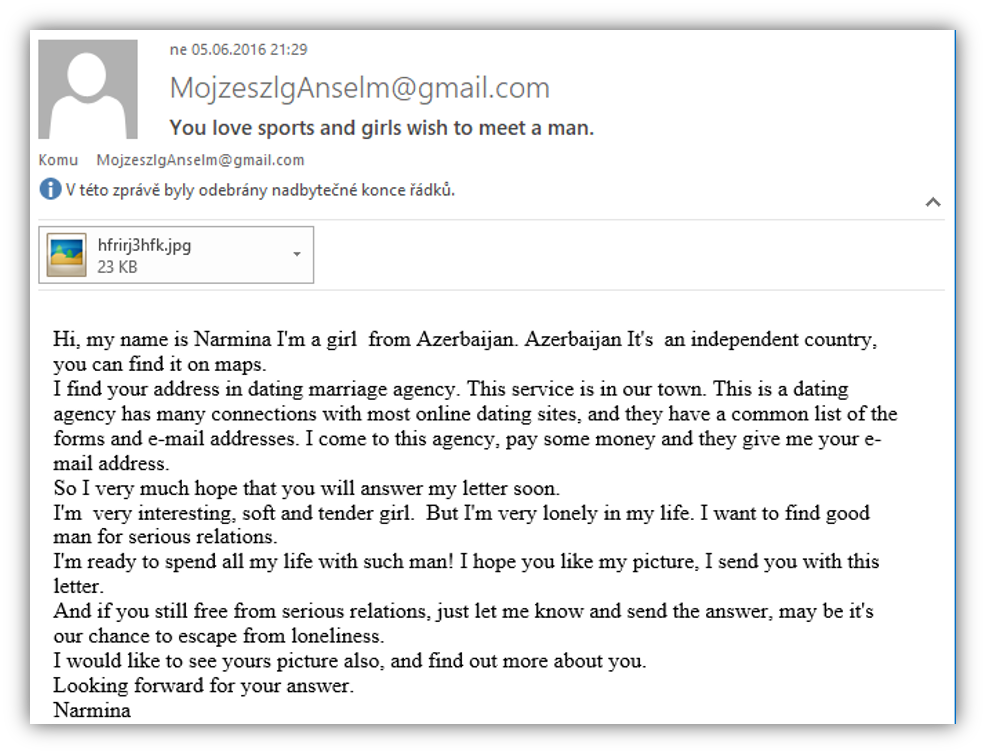
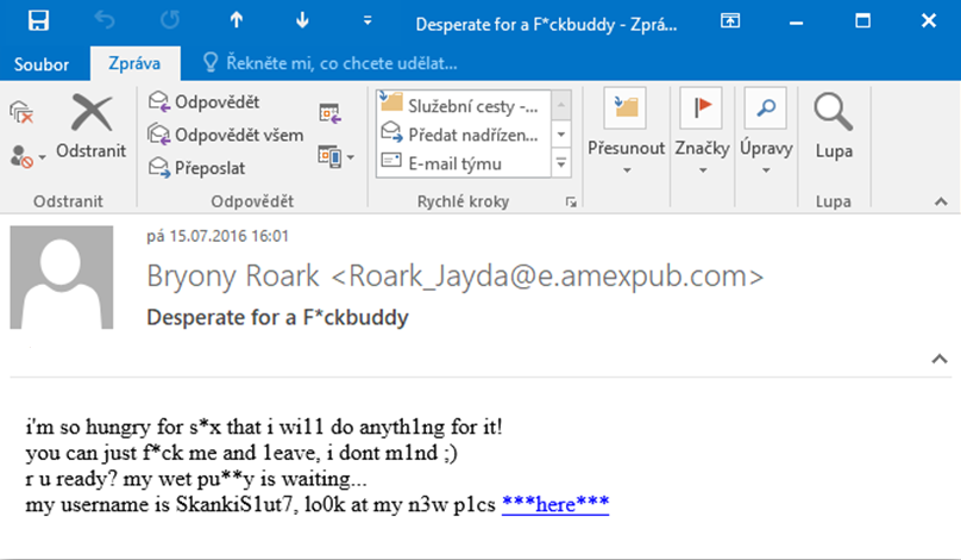
Message No. 3 – “Instant sex”
Message No. 4 – A Nigerian astronaut has been forgotten in space and needs to get home
The news began to spread in 2004, at which time the “first African astronaut” had been in space for 14 years without a break. It should be noted that the length of his stay surpassed all the times of astronauts (perhaps in total). I received the last version of this Scam 419 in 2016. Although I am very sorry for this imaginary astronaut (26 years in space and alone), I certainly do not intend to contribute to fraudsters. Unfortunately, despite the completely meaningless content and unsubstantiated information contained in this e-mail, there are a large number of people who want to help a person in need (thanks to this help, this scam could be included in the donor scam group).

Due to the nature of fraud, it would be possible, in some cases, to label or subordinate Scam 419 to acts having the nature of phishing.
4.5.2. Hoax
A hoax (a fiction, prank, press canard) is another form of spam or scam. The label “hoax” is used for chain messages (such as: “pass it on”, “if you don't send it to 20 other people... happens.”, etc.), which contain distorted, untrue, misleading or other false information. A hoax often contains warnings about attacks, descriptions of dangers, pleas for help, calls, petitions, statements of celebrities, chain letters of happiness, funny messages, pictures and videos in presentations, playing cats and other animals, etc.
4.5.3. Fraudulent offers
A very successful form of scam is various fraudulent offers, which can be sent in bulk or in a targeted manner. At present, such offers are sent not only via e-mails, but also via any instant messengers, social networks, auction portals, etc.
With regard to the mass distribution of fraudulent offers, it is possible to imagine a number of activities on the principle of “pyramid” or “plane”, offers of advantageous work from home [6] , “guaranteed” methods of value for money (with the highest interest rates), offers on loan (with the lowest interest rates), “great” job opportunities, etc.
Targeted sending of fraudulent offers should also include conduct that is not merely spam, but is, for example, a combination of bidding on a specific type of goods within auction portals and subsequent communication with users who have accepted this bid. These are so-called “auction frauds”.
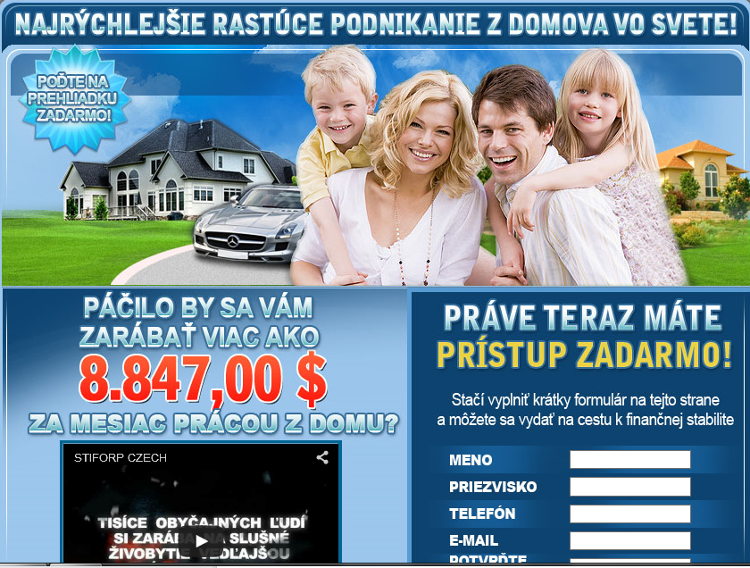
Irresistible offer of work from home (mass distribution within the social network Facebook)
At present, it is certainly no longer the rule that bulk or targeted offers are written in suspicious or broken Czech (or are written in English or Russian), on the contrary, an attacker's effort is to convince a victim of absolute correctness, seriousness and “honesty” of his actions. Auction portals very often fraudulently offer various types of electronics, especially mobile phones and computers. The actual fraud can then consist, for example, of changing essential information [e.g. country of origin of the mobile phone; information that it is a copy (forgery) of the phone] or non-delivery of the goods as such. (The attacker very often requests payment of the full amount or advance.)
The imaginativeness of the attackers is considerable in the Internet environment, and in the case of any offers, advertisements, and especially the sending of advances or payments, it is advisable to be paranoid and not trust unknown persons.
In the case of fraudulent offers, where an attacker tries to obtain various advances or other payments in advance, such conduct can be punished according to Section 209 (Fraud) of the Criminal Code.
Possibilities of criminal sanctions in the Czech Republic
As far as the criminal sanction of spam and spammers is concerned, it is currently not fully (re)solved in the Czech Republic. There is no national or international legal protection against this undesirable behaviour. Even the Convention on Cybercrime does not include the definition of spam as a criminal offence.
For example, in the USA, spammers [7] have been convicted of sending spam in the past. For example, Jeremy Jaynes was sentenced in 2007 by a Virginia court to 9 years in prison. He was accused in 2003, as evidenced by 53,000 spams sent within three days. However, the prosecutor said he believed Jaynes was responsible for sending more than 10,000,000 spams a day, which should have earned him approximately $ 750,000 a month.
Due to the fact that only one form of harmful conduct cannot be included under the term spamming, it is very difficult to punish spamming under criminal law. This can only be done for its individual types. In certain cases, it is possible to punish the collection of e-mail addresses if such collection meets the objective elements of the criminal offence of unauthorised handling of personal data under Section 180 (Unauthorised handling of personal data) of the Criminal Code. If the spam contains malware or is intended to commit fraud, it is possible to punish a spammer's activities according to the provisions relating to malware or phishing.
Possibilities of criminal sanctions in Poland
In Poland sending unsolicited commercial information by electronic means of communication is considered an offence and is subject to a fine. This is regulated by the Act of 18 July 2002 on the provision of electronic services (Journal of Laws of 2002 No. 144, item1204):
Art. 24. 1. Whoever sends, by means of electronic communication, unsolicited commercial information, shall be subject to the penalty of a fine.
(2) The prosecution of the offence, referred to in section 1, shall occur at the request of the injured party.
Article 25 Adjudication in cases related to the offences specified in Articles 23 and 24 shall be conducted pursuant to the provisions on proceedings in petty offence cases.
Possibilities of criminal sanctions in Portugal
Also in Portugal, in general terms, spamming itself is not considered as a criminal offence. However, following Art. 14(1)(f)(g)(h)(i)(j) ofLaw No. 41/2004, on data protection and privacy in electronic communications, spammers for commercial purposes must pay administrative fines, from a minimum of € 1500 to a maximum of € 5000000.
However, as an exception, being the content of messages within the scope of Law No. 52/2003, on the fight against terrorism, it might be considered as a criminal offence (Arts. 2 and 4).
[1] To classify spam, cf. for example GONZÁLES-TALAVÁN, Guillermo. A Simple, Configurable SMTP Anti-spam Filter: Greylists. Computers & Security, 2006, vol. 25, No. 3, pp. 229–236.
[2] Cf. for example: Spam statistics. [online]. [cit.14.8.2016]. Available from: https://www.spamcop.net/spamstats.shtml
Spam Statistics and Facts. [online]. [cit.14.8.2016]. Available from: http://www.spamlaws.com/spam-stats.html
[3] Original online source:http://www.trustedsource.org/TS?do=homehttp://spam-filter-review.toptenreviews.com/spam-statistics.html [cit.12.2.2010].
[4] It is not possible to determine exactly what percentage of all e-mails are spam. The different sources available give different, sometimes very different numbers. E.g. One of the providers of antispam solutions, POSTINI, recorded in March 2005 within 24 hours that 10 out of 12 e-mails were spam. The frequency of sending spam, cf. e.g. LANCE, James. Phishing bez záhad. Prague: Grada, 2007, p. 22, SCHRYEN, Guido. The Impact that Placing Email Addresses on the Internet Has on the Receipt of Spam: An Empirical Analysis. Computers & Security, 2007, vol. 26, No. 5, pp. 361–372.
[5] Malware, mayhem, and the McColo takedown. [online]. [cit.14.8.2016]. Available from: http://betanews.com/2008/11/13/malware-mayhem-and-the-mccolo-takedown/
[6] On the one hand, these offers may consist of a request such as: “send us $10 to our account and we will send you instructions on how to earn $8,847 a month.” The second possibility is that these job offers do not require any fee in advance, they only require user registration. By registering, an attacker receives personal data about a user. An e-mail from this company, containing e.g. malware, etc., can then be sent to the user's e-mail address.
[7] Convicted spammer challenging Va. law[online]. [cit.14.8.2016]. Available from: http://www.usatoday.com/tech/news/techpolicy/2007-09-12-spammer-va_N.htm
Top Spammer Sentenced to Nearly Four Years.[online]. [cit.14.8.2016]. Available from: http://www.pcworld.com/article/148780/spam.html
Buffalo Spammer jde na 7 let za mříže kvůli rozesílání nevyžádané pošty.[online]. [cit.14.8.2016]. Available from: http://technet.idnes.cz/buffalo-spammer-jde-na-7-let-za-mrize-kvuli-rozesilani-nevyzadane-posty-13i-/tec_reportaze.aspx?c=A040528_28629_tec_aktuality
