Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.4. Ransomware
The group of malware also includes the so-called extortionate malware, for which the term ransomware has been coined [1] (sometimes also referred to as rogueware or scareware). Ransomware is malware that prevents or restricts users from using a computer system properly until an attacker receives a “ransom”. Ransomware most often gets on your computer using malware (a Trojan horse or worm) that is located on a website or is an e-mail attachment. Once a malware is safely “established” in a computer system, its own ransomware will be downloaded.
In general, it is possible to distinguish two types of ransomware according to how much they interfere with the actual operation of a computer system. The first type is ransomware which limits the functionality of an entire computer system and does not allow a user to use this system at all (e.g. by preventing the operating system from starting or blocking the system screen. A typical example of this type is “Police ransomware” – see below). The second type is ransomware, which leaves a computer system functional, but locks user data and makes them inaccessible.
Currently, the second type of ransomware, known as crypto-ransomware, is being used.The purpose of this malware is to encrypt a hard disk or selected file types in a computer system, primarily aimed at encrypting a user's private files such as images, text or spreadsheet documents, videos, etc. After encryption, the user usually receives a message that his/her files are encrypted, and if he/she wants to get them back (decrypt), he/she must send a certain amount to the attacker's account. Typically, virtual currencies such as Bitcoin or various prepaid services are used for transactions. In most cases, there is a time limit for payment. After this time, the key that can open the encrypted files is deleted.
Evolution of ransomware
Ransomware, like any other malware, is evolving, with the first malware to be classified as ransomware appearing around 2005. It was essentially a fake antivirus(screware) that, with the help of social engineering, tried to convince a user to pay an amount for cleaning an infected computer system. This ransomware usually allowed a user to use a computer system (it was not locked or data encrypted), but it bothered the user with pop-ups and alerts about non-existent viruses on the computer. This ransomware was very easy to remove.
The massive onset of ransomware can be dated to about 2011, when a ransomware attack blocking access to a Windows user's account began to spread worldwide, announcing that the computer had been blocked by the state's police.
The actual attack consisted in the user becoming infected with malware (typically a “botnet client” was downloaded when visiting some websites [2] ) and subsequently became part of a botnet through which its own “police ransomware” was distributed. This police ransomware subsequently blocked access to a Windows user account [3] by notifying the user that material infringing the law of the country was found on his/her computer (e.g. copyright infringement, child pornography, etc.). At the same time, the user was invited by the “police” to pay the required amount of money, after which the computer will be unblocked and the whole thing will be “resolved”. In this case, the attackers used social engineering techniques, specifically the concerns and trust of a user, and by referring to official authorities, they tried to obtain money from him.
What was striking about the whole case was the fact that a large part of users willingly paid the required amount (in the Czech Republic, this amount ranged between CZK 2000–4000), without verifying whether the real police are authorised to block computers or to “handle” any offences of the user in such a way.
The following print screens show “police ransomware” in various countries and then the versions used in the Czech Republic are shown.
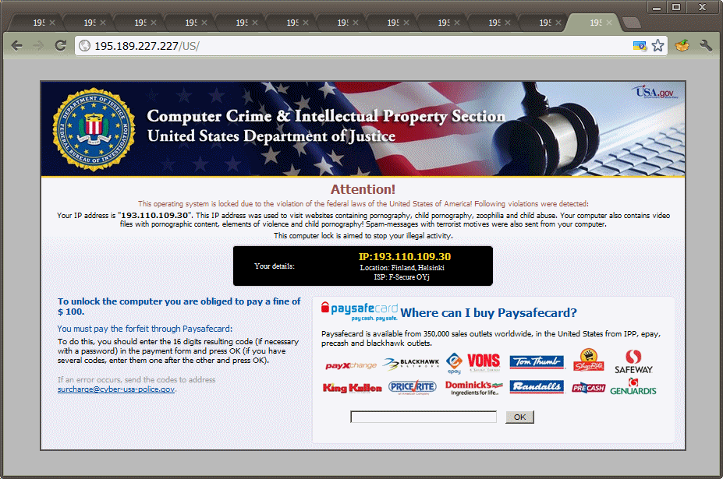
Police ransomware [4]

UK version of police ransomware [5]
In Europe, various versions (the appearance of the site) of police ransomware gradually appeared. The first version was recorded at the end of 2011, showing the IP address of the connection, the ISP connection and the location [where the IP address of a specific connection provider (ISP) was given], if a user had the webcam turned on, a photo was created and displayed.
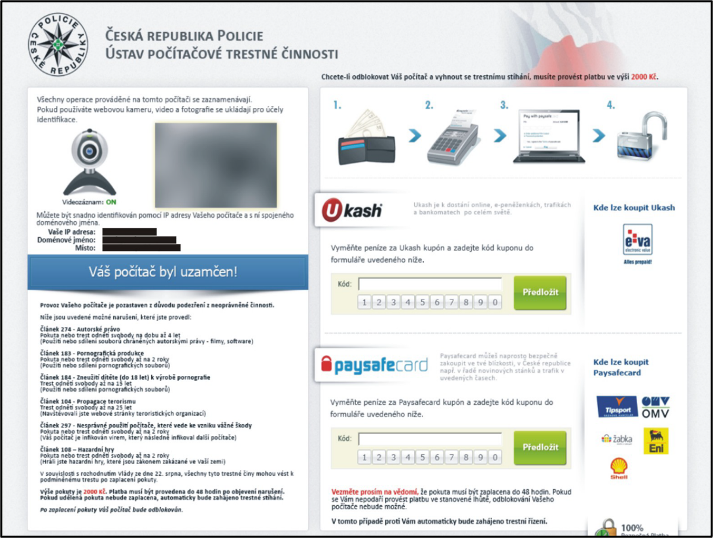
Police ransomware – the first version in the Czech Republic
Newer versions, in addition to differing graphically, also displayed the operating system version and username. The Czech language used on the locked page has also been improved.

Police ransomware in the Czech Republic – other versions
The “police ransomware” described above experienced its greatest expansion in 2011–2013; however, other variants of this malicious software appeared with various modifications later. The following print screens show modifications of the “police ransomware”. Both cases were discovered in 2015. The first print screen shows a ransomware that blocks the dominant web browser used on the infected computer (while other browsers have not been infected). The user was able to use all the functions of the computer system, except for the infected browser.
In addition to the previously mentioned information, the GPS position and the remaining time until payment are displayed.

Police ransomware in the Czech Republic (2015)
The second print screen shows a “locked” computer, while the ransomware was hidden in the crack of an illegally downloaded and installed game (in this case, it was a Far Cry 4 game downloaded from Czech torrents).
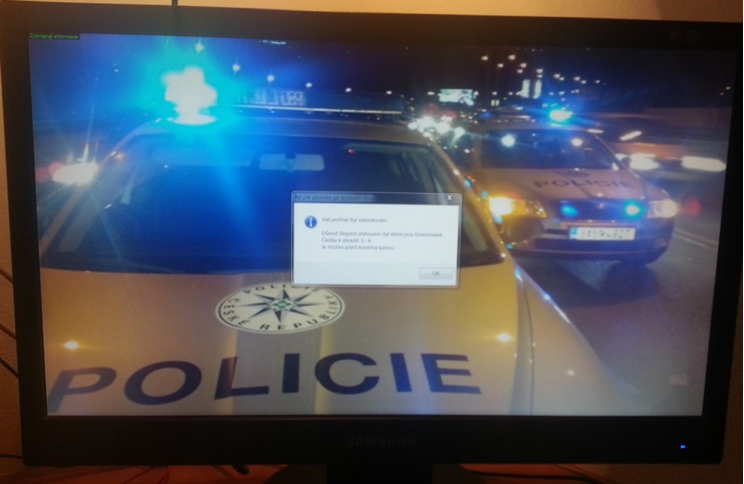
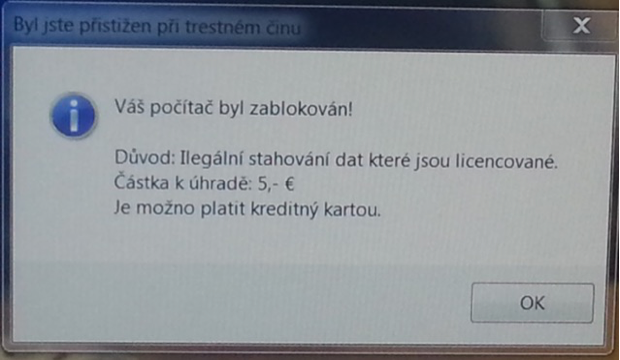
Police ransomware in the Czech Republic (2015)
Text on the figure:
Your computer has been blocked!
Reason: Illegal downloading of data that is licensed.
Amount to be paid: 5,- €
It is possible to pay by credit card.
Since 2013, there has been a significant change in the case of ransomware.The attackers reduced the attacks which consisted in limiting the functionality of the entire computer system, and primarily focused on locking user data. Data on local disks, disks connected within the computer network and on all connected peripherals (e.g. external USB, HDD, etc.) are locked. Data becomes a “hostage”, and breaking encryption is almost impossible. One of the first ransomware of this type was CryptoLocker (then CryptoWall, etc.).
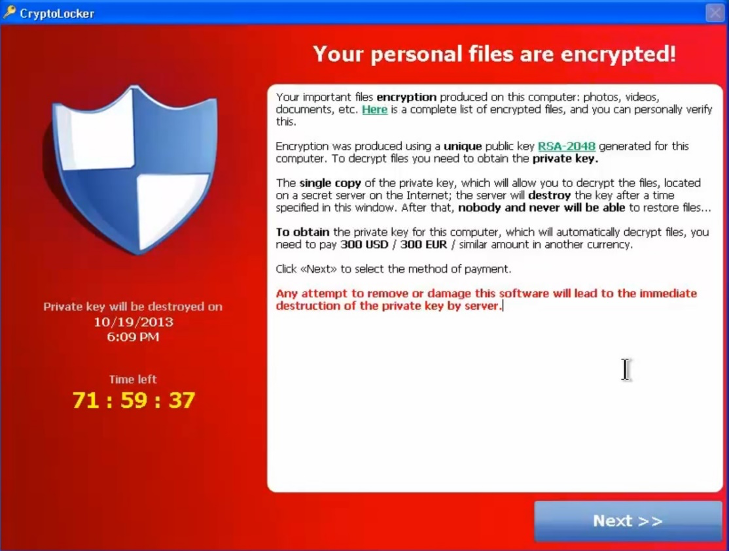
CryptoLocker (2013)
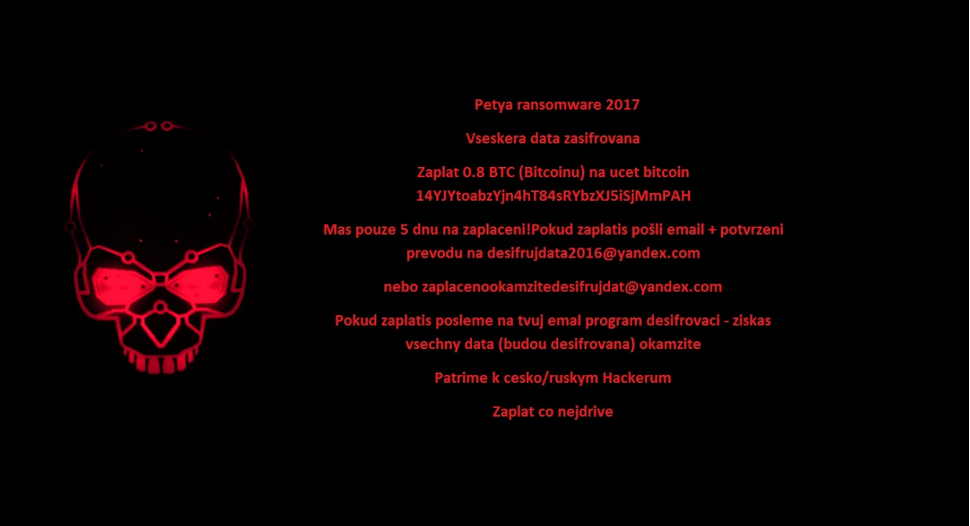
Petya (2017)
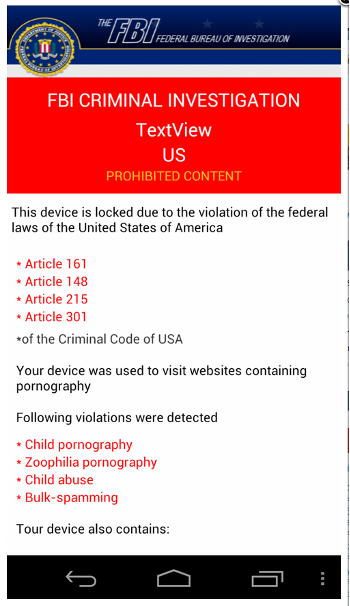
Mobile ransomware (2018)
As part of crime-as-a-service activities, the ransomware-as-a-service has been offered since 2016. A user (i.e. an attacker) has the opportunity to define his/her own ransomware according to his ideas. At the same time, he/she is provided with technical background in the form of C&C servers, bitcoin wallets, online 24/7 support, etc. An example of ransomware-as-a-service is the Ransom32 software.
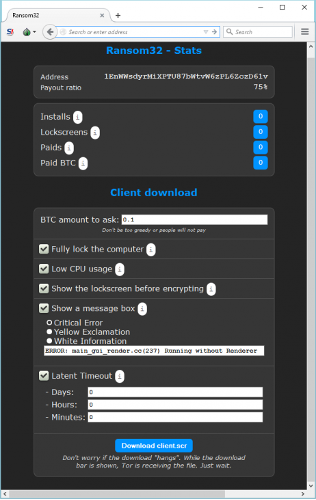
Ransomware (client)
Other changes can be observed in attackers’ activities. If ransomware is installed, this malware can be targeted, for example, to encrypt stored positions in games, or to “lock” TVs that use the Android operating system. [6]
Prevention and response to ransomware can be summarised in the following points:
1. Immediately:
· Avoid interconnecting systems other than necessary
· Prevent communication to the Internet except when necessary
· Change the passwords of privileged accounts
2. Within a few days:
· Move backups offline, check the functionality of backups
· Examine business continuity plans and move them out of systems
· Do not delete data about cybersecurity incidents
· Check compromise indicators
· Alert employees to the risk of phishing
3. Within a week:
· Verify that backups are separated so that even a privileged administrator cannot delete them
· Prohibit the use of unsigned macros if possible.
· Check network segmentation and control between segments
· Tighten the security policies of end stations (prohibition of running unapproved applications, unsigned PowerShell...)
· If business continuity management is not implemented – develop business continuity plans at least for key systems
· Install antivirus on all relevant devices
· Consider testing and deploying the update
4. Long-term recommendations for solving ransomware attacks
· Regular staff training
· Significant network segmentation
· Minimise the use of administrator accounts
· Backup, regularly test backups, keep backups offline
· Rule 3 – 2 – 1 = At least 3 copies on 2 different devices, 1 of which is outside the organisation.
· Have business continuity plans (BCPs) and test them
· Regularly check applications accessible from the Internet and evaluate whether they are still needed
Possibilities of criminal sanctions in the Czech Republic
In the Czech Republic, it is possible to punish an attack with malware which is ransomware according to Section 230 (Unauthorised access to a computer system and information carrier) of the Criminal Code. Possession of malware, with the intention to commit a criminal offence under Section 182 (Violation of the secrecy of transported messages) or a criminal offence under Section 230 of the Criminal Code, is a criminal offenceunder Section 231 (Obtaining and possession of access device and computer system passwords and other such data) of the Criminal Code.
In the case of ransomware, it is also possible to apply the provisions of Section 230 (3) of the Criminal Code, where an attacker commits such a criminal offence with the intention of obtaining an unjustified benefit to himself or to another. The application of Section 175 (Blackmailing) of the Criminal Code could also be considered, when a person is forced to pay a given amount by threatening other serious damage (e.g. by being filed with a criminal complaint [7] ]).
Possibilities of criminal sanctions in Poland
The laws that apply in Poland are:
Art. 267. Unlawful obtaining of information
Art. 269a. Interference with the operation of an information or data communications system or network
Possibilities of criminal sanctions in Portugal
As in almost all jurisdictions, ransomware attacks are not specifically criminalised. Though, such actions may be persecuted as Extortions (Art. 223 of the Criminal Code). An alternative, from a strict perspective of Cybercrime, would be Computer-related fraud (Art. 221 of the Criminal), as the its material scope is quite wide, following the wording of the equivalent felony in the text of the Convention of Budapest (Art. 8).
Nonetheless, other felonies would also be present, depending on the modus operandi of the attackers. Namely, by technical means, being punishable as an Illegal access (Art. 6 of Cybercrime Law), or by social engineering, with the inherent Computer-related forgery (Art. 3 of Cybercrime Law).
Furthermore, in itself, the encryption of the victim’s data would amount to Computer sabotage [Illegal interference] (Art. 5 of Cybercrime Law), in an aggravated form if critical infrastructures or essential services were disturbed (Art 5(5)(b) of Cybercrime Law).
Finally, if the decryption is not possible, a Damage to computer programmes or other computer data [Data interference] (Art. 4 of Cybercrime Law) would be in place.
[1] For example Reventon, CryptoLocker, CryptoWall, Loky, Petya, Cerber, SamSam, JigSawetc. For more details, see e.g.:
Ransomware. [online]. [cit.14.8.2016]. Available from: https://www.trendmicro.com/vinfo/us/security/definition/ransomware
[2] Very often it was a site with pornography or other sexual material. A user could also be redirected to these pages from another page with a “bait”.
[3] The application was set to “StayOnTop”. A user does not see other applications hidden under this “ransom dialog” and is not able to call up the task manager. The Ransomware itself was registered in the Run and RunOnce registers and performed a check every 500 ms, and hid the task manager in the same time range. The only other running application was communication with the C&C server (masked in the browser process).
[4] Police ransomware. [online]. [cit.14.8.2016]. Available from: https://www.f-secure.com/documents/996508/1018028/multiple_ransomware_warnings.gif/8d4c9ca2-fc77-433d-ac16-7661ace37f88?t=1409279719000
[5] [online]. [cit.14.8.2016]. Available from: https://sophosnews.files.wordpress.com/2012/11/cool_ransom_uk_full.png
[6] Cf. for example. New Ransomware Encrypts Your Game Files. [online]. [cit.14.8.2016]. Available from: https://techcrunch.com/2015/03/24/new-ransomware-encrypts-your-game-files/
Android Ransomware now targets your Smart TV, Too! [online]. [cit.14.8.2016]. Available from: https://thehackernews.com/2016/06/smart-tv-ransomware.html
FLocker Mobile Ransomware Crosses to Smart TV. [online]. [cit.14.8.2016]. Available from: http://blog.trendmicro.com/trendlabs-security-intelligence/flocker-ransomware-crosses-smart-tv/
[7] The concept of other severe damage, see ŠÁMAL, Pavel et al. Trestnízákoník II. § 140 až 421. (Criminal Code II. Sections 140 to 421). Komentář. (Comment.) 2nd Edition. Prague: C. H. Beck, 2012, pp. 1752–1753
Specifically, “a threat of other serious damage may consist of a threat of property damage, serious damage to honour or reputation, etc. Another type of serious damage may be the initiation of criminal proceedings as a result of reporting a crime by which the perpetrator threatens the injured party, forcing him to do, neglect or tolerate something. At the same time, it is indecisive whether the injured party has committed a crime, the notification of which he/she is threatened, or not (cf. R 27/1982).“
