Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.3. Malware
Malware (a compound of malicious software) can be any software used to disrupt the standard operation of a computer system, gain information (data) or used to gain access to a computer system. Malware can take many forms, with many types of malware named after the activity they perform.
One malware is able to perform several functions (carry out several activities) at once. For example, it can further spread itself via e-mails (in an attachment) or as data in P2P networks, and at the same time it can obtain, for example, e-mail addresses from an infected computer system.
Historically, there were at first a number of different terms for this software, which is currently referred to by the collective term malware. The actual names of specific malicious software were usually created according to the activity that the program performed. Despite the above statement that the term malware is primarily used at present, it is still possible to come across a historically older designation of malicious software. These are the following groups:
1. Adware
2. Spyware
3. Viruses
4. Worms
5. Trojan Horses
6. Backdoor
7. Rootkits
8. Keylogger
9. Ransomware etc. [1]
Ad 1) Adware
The term adware is an abbreviation of the English phrase “advertising supported software”. It is the least dangerous but profitable form of malware. [2] Adware displays advertisements on the user's computer system (e.g. pop-ups in the operating system [3] or on websites, advertisements displayed together with software, etc.). Although in most cases these are products that only bother the user with constant advertising messages that “pop up” on the screen, adware can also be associated with spyware, the purpose of which is to monitor user activity and steal important information.
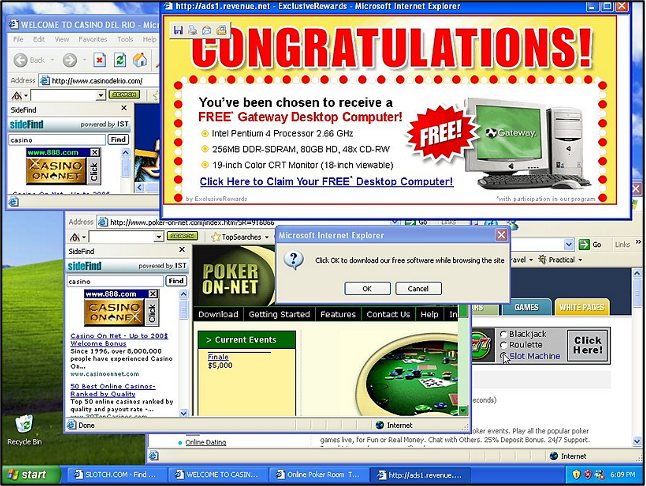
Adware
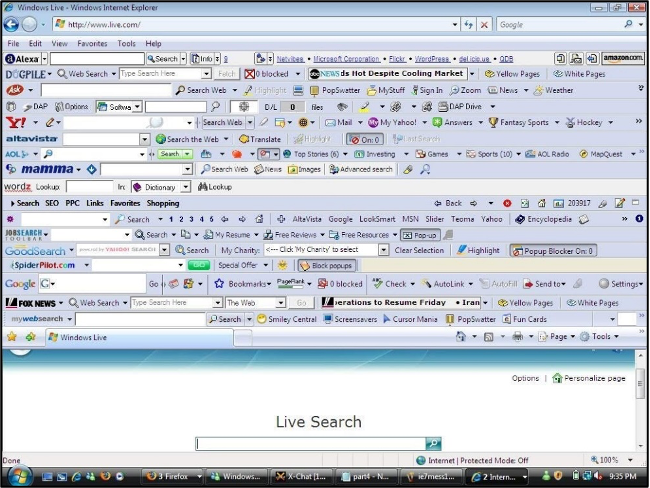
Example of Adware and other add ons installed in a web browser [4]
Ad 2) Spyware
The term spyware is a combination of the English words “spy” and “software”. Spyware is used to obtain statistical data [5] on an operation of a computer system and to send it to an attacker's data box without a user's knowledge and consent. This data may also include information of a personal nature or information about a person of a user, as well as information about visited websites, running applications, etc.
Spyware can be installed as a standalone malware, as well as often as part of other, free and otherwise completely safe programs. In this case, the installation and other activities of the spyware are typically handled in the terms of the EULA, and the user usually unknowingly voluntarily agrees to monitor their own activities. Adding spyware programs to other programs (e.g. P2P client programs, various shareware programs, etc.) is motivated by the program manufacturer's efforts to find out the interests or needs of a user and use this information, for example, for targeted advertising. [6] A characteristic feature of spyware programs that are part of a “program package” is that they usually remain installed on the computer even after the main program has been uninstalled, which in most cases is hidden from the user.
Spyware poses a threat both because it sends various information from a user's computer system to an “attacker” (which is further processed and correlates with data and information obtained from other sources), and because spyware may contain other tools that affect the user's own activities [7] .
Ad 3) Viruses
It is a program or malicious code that attaches itself to another existing executable file (e.g. software, etc.) or document. The virus is reproduced the moment this software is launched or an infected document is opened. Most often, viruses spread through the sharing of software between computer systems; they do not need the cooperation of a user to spread them. Viruses were the dominant form of malware, especially in the 1980s and 1990s. [8]
There are a large number of viruses whose purpose is to destroy, while others are designed to “settle” in as many computer systems as possible and then use them for a targeted attack. Typical for these programs is the ability to spread between systems without the need for user intervention on a computer system. Effects of viruses can be multifarious, such as the harmless playing of a melody, system congestion, change or destruction of data, or the total destruction of an infected system. Computer viruses can be classified according to many different aspects, e.g. according to the host (i.e. according to the type of programs that computer viruses transmit), according to the ways they effect in the system, according to their location in memory, etc. [9] Depending on what files the viruses infect, they can be divided into:
- boot viruses (infect only system partitions)
- file viruses (infect only files)
- multipartite viruses (infect files as well as system areas)
- macroviruses (attack applications using macros)
Ad 4) Worms
So-called computer worms are also referred to as viruses. The reason for the closer connection with viruses is the fact that worms do not need any host, i.e. no executable file (similar to viruses). Unlike viruses, which are attached as part of another program, these programs usually spread separately. A compromised system is then used by a worm to further send copies of itself to other users via network communication. In this way, it spreads very quickly, which can lead to congestion of a computer network, and thus an entire infrastructure. Unlike viruses, these programs are able to analyse security vulnerabilities in the security of an infected information system, [10] so they are also used to look for security gaps in systems or mail programs. [11]
Ad 5, 6) Trojan Horses and Backdoors
Trojan horses are generally those computer programs that contain hidden features that a user does not agree with or is unaware of, and that are potentially dangerous to the continued operation of a system. As with viruses, these programs can be attached to another, secure program or application, or they can look like a harmless computer program. Trojan horses, unlike classical viruses, are unable to replicate or spread without the“help” from a user. If a Trojan horse is activated, it can be used, for example, to delete, block, modify, copy data or disrupt the running of a computer system or computer networks.
Some Trojans, when activated without a user's knowledge, open the communication ports of a computer, which significantly simplifies further infection of the affected system by other malicious programs, or facilitates direct control of the infected computer so-called remotely. Such Trojan horses are referred to as backdoor. [12] Modern backdoor programs have improved communication and use most protocols of some communication tools, such as ICQ. [13]
The use of Trojan horses is often associated with the use of various scanning [14] programs (“port scanners”), which are programs that are used mainly to determine which communication network ports of the computer are open, what services are running on them and whether it is possible to carry out an attack on such a system. This data is again sent to an attacker and is also potentially useful in committing other cyberattacks.
Ad 7) Rootkits
This term refers not only to computer programs, but also to the entire technology used to mask the presence of malware (e.g. computer viruses or Trojan horses, worms, etc.) in an infected system. They most often take the form of not very large computer programs. Rootkits are not harmful in themselves, but are used by the creators of malicious programs, such as viruses, spyware, etc. [15] A rootkit program changes the behaviour of an entire operating system, its parts, or add-on applications so that users do not become aware of the existence of malicious programs on their computer system. In general, rootkits can be divided into system (modifying the kernel) and application (modifying the application configuration) rootkits. [16]
Of the applications, rootkits mainly attack specialised programs for searching for and removing dangerous programs from the system, i.e. antivirus, etc. [17] When using a rootkit program, antivirus programs cannot remove this malicious program from the infected system. In this way, the presence of a malicious program in the infected system is prolonged. From this point of view, it can be stated that rootkits can be very easily misused to commit crimes related to the use or misuse of information technology. Some literature refers to these tools as a subgroup of backdoor Trojans. [18]
Ad 8) Keylogger (Keystroke Logger)
Keylogger is software that records specific keystrokes on an infected computer system. Most often, a keylogger is used to record login data (username and password) to accounts that are accessed from a computer system. The information obtained is then typically sent to an attacker.
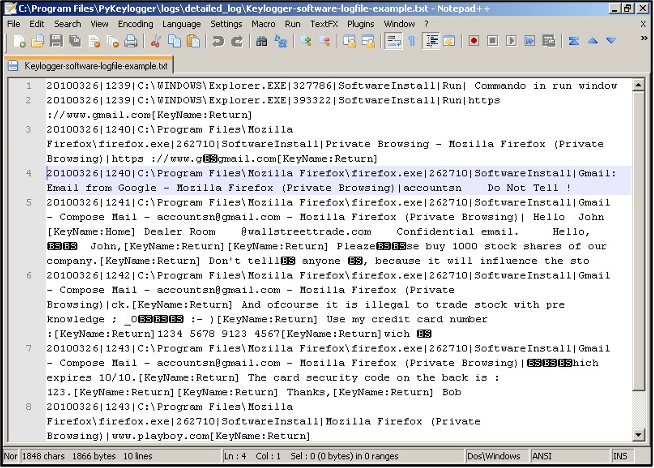
Example of keylogger operation [19]
Ad 9) Ransomware
Ransomware will be described in more detail in a separate chapter.
Malware distribution
There are a number of ways in which malware can be delivered to a target computer system. Here I will briefly list some methods of spreading malware. Malware can be distributed through:
· Portable storage media
For example, using CD, DVD, USB, external drive, etc. This is the oldest but still effective way of distributing malware, where users pass infected files or computer networks containing infected files (sharing such files within computer networks, typically P2P networks).
· Drive-by-download
One of the most common ways to infect malware is to download it from the Internet and then run a file, typically with an .exe (executable file) extension, from an unknown source. These can be fake or counterfeit programs (e.g. imitations of Flapp Bird, fake media codecs, etc.), programs used to circumvent copyright protection (cracks, keygens, etc.), real infected programs, etc.
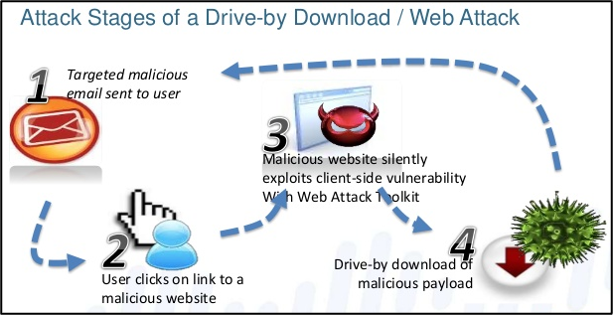
Illustration of one of the possible principles of drive by download. [20]
The following example shows malware downloaded by a user through a P2P network (specifically, a file featuring The Big Bang Theory –Season 9, Part 18). This malware prompted users to download a new codec through Media Player so that the video could be played. The media player started to connect to an attacker's site and then a fictitious codec was installed, but in fact malware was installed on the computer (in this case a combination of malware: backdoor, keylogger, bot), which allowed the attacker to completely control the user's computer system.
In this case, the fact that the offered part of The Big Bang Theory has not yet been broadcast in the USA, where it premieres, was very striking, but the number of downloads was in the tens of thousands.
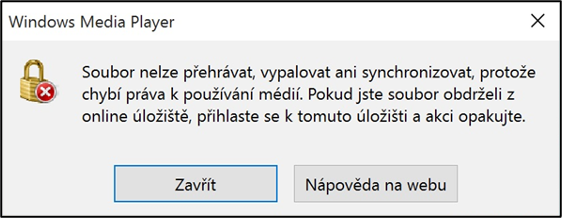
Text on the figure: The file cannot be played, burned or synchronised because media usage rights are missing. If you received the file from an online repository, log in to that repository and try again.
Close / Help on the web
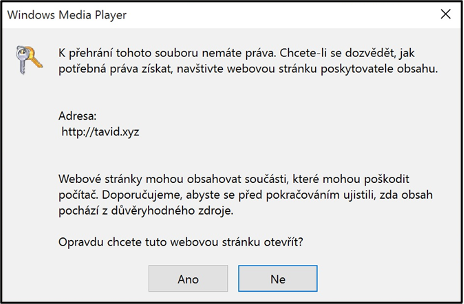
Text on the figure: You do not have permission to play this file. To learn how to obtain the necessary rights, visit the content provider's website.
Address: http://tavid.xyz
Websites can contain components that can harm your computer. We recommend that you make sure that the content comes from a trusted source before proceeding.
Are you sure you want to open this web page?
Yes / No

· “Office documents”
Very often, malware spreads in the body of files such as: .doc, .xls, .avi, etc. Only macro viruses can be distributed in this way. A user assumes that he/she is opening a word document, but at the same time runs an executable file that masquerades as that document.
Malware can be stored in an attachment to an e-mail, or it can be a script inside a HTML [21] body of e-mails. This is currently one of the most common ways of distributing malware. Examples are current phishing campaigns, hoaxes, spam, etc.
· HTML
Malware can be placed directly on a website or in individual scripts.
· Fake antivirus
Users are typically offered a free antivirus – as adware. This antivirus will “scan your computer” and detect serious vulnerabilities and malware that a user's antivirus did not detect. Fake antivirus combines a social engineering attack (raising concerns about malicious software) with the installation of malware contained in a fake antivirus.
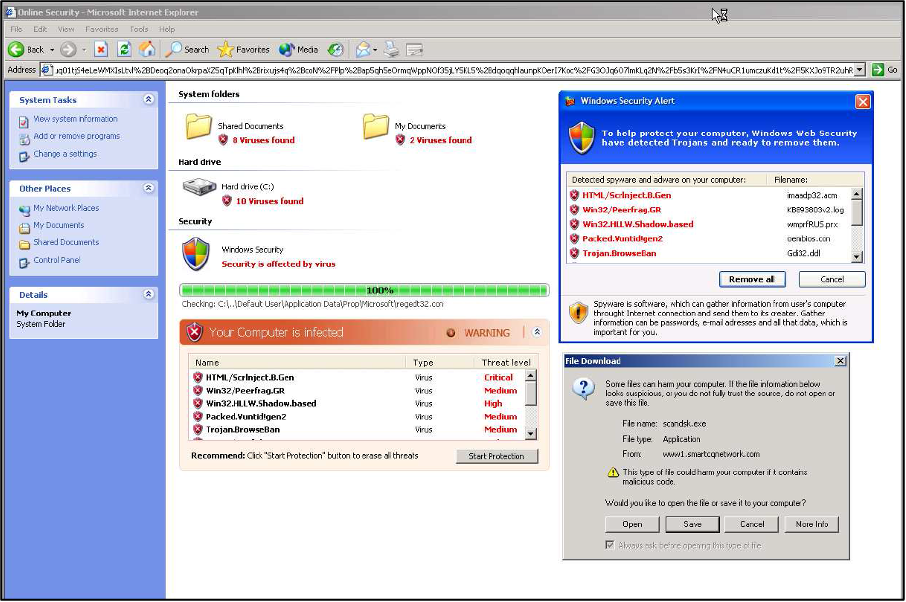
Fake antivirus
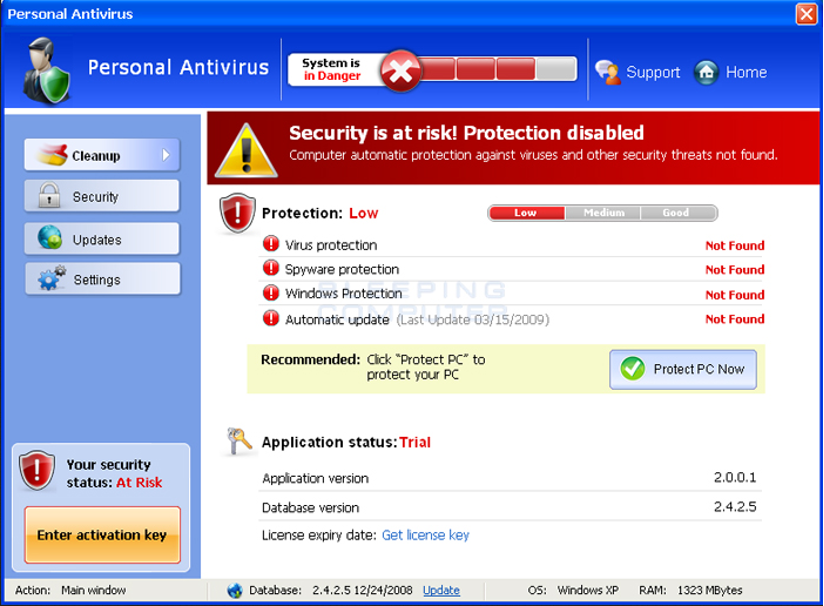
Fake antivirus [22]
If a user is unsure whether a file or website contains malware, they can use a variety of tools to help them check for malware.
One of the proven services is https://www.virustotal.com/. On this webpage, a user can specify a scan of a file up to 128 MB or have a website he/she intends to access checked. (It is advisable to perform this scan, for example, when visiting Internet banking sites or payment sites. You need to copy the full URL of the page you visit.) The Virustotal service connects companies handling cybersecurity, the development of antivirus products, etc., while a user's request is tested by the tools of all these companies, thus increasing the probability of detecting malicious software.
The following printscreen shows the scan result of a newly delivered file as part of a phishing campaign. The day after the start of this campaign, only 5 companies identified malware in an attached file, and within a week all other companies were able to identify it. However, the time between the delivery of updates to users' antiviruses on their computer systems and the start of the attack is crucial for the eventual success of an attacker.
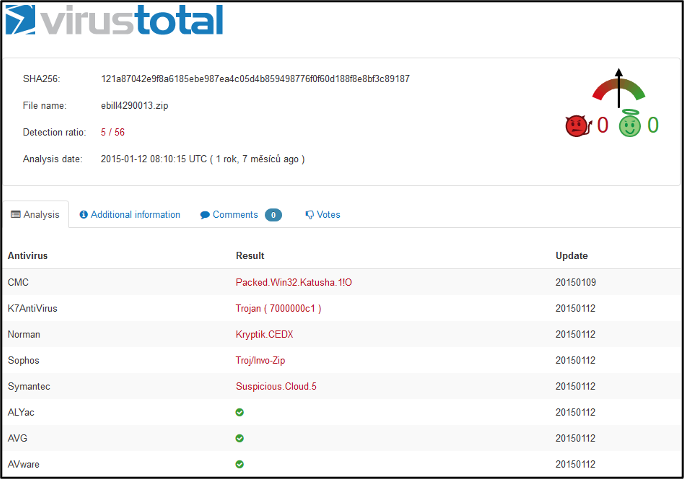
File test result
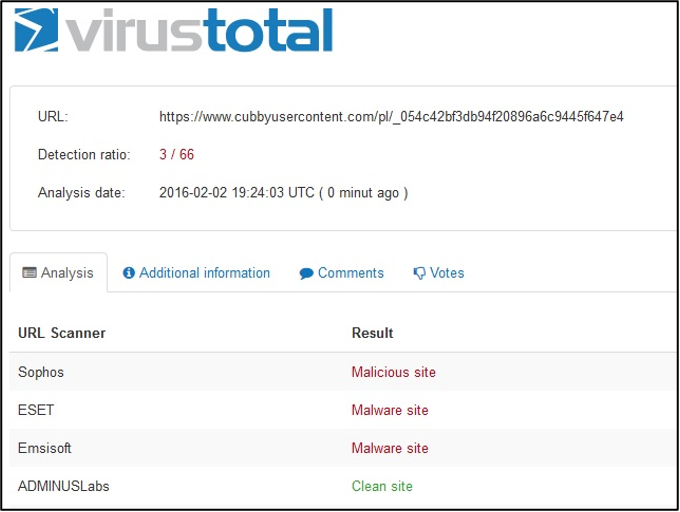
Website test result
Malware can be installed on almost any computer system. Micromalware installation cases are examples of specific installations. This is malicious code that spreads on a relatively small number of computer systems. This code exhibits abnormal behaviour and security programs often fail to respond. The most well-known case of micromalware is the STUXNET worm [23] or the installation of a botnet client in the already mentioned fridge.
A malware designed for mobile devices (mobile malware) is then a separate chapter. The first malware designed to attack mobile phones was discovered around 2004. Today, Kaspersky Lab, which reported on the discovery at the time, states that there are more than 340,000malware. [24]
If we focus on the most vulnerable operating system within mobile devices, then most threats target the Android OS. The reason for this is mainly the variety of used operating system versions and their outdatedness. Most Android devices do not allow you to update your operating system to the latest version, which is usually modified to withstand known vulnerabilities and has already fixed bugs from previous versions of this operating system. In fact, it is estimated that 77% of the threats attacking the Android OS could be eliminated by using the latest version of this operating system.
In the case of mobile devices, attackers mainly use:
- Outdated versionof a mobile device operating system (known vulnerabilities of individual systems);
- Minimal security of a mobile device by anti-virus means;
- User ignorance (Many users recklessly install applications “from an unknown source” or applications that require excessive access and permissions within the device.);
- Social engineering and “waves of interest” in applications of a certain type.
One of the reasons why Android is attacked as the primary operating system is the fact that the security of applications is not verified within the distribution channel (Google Play) (or whether a particular application does not contain malware, for example), as is the case with the iOS operating system and its distribution channel (App Store).
 An example of the above is Flappy
Bird and its “clones”.
An example of the above is Flappy
Bird and its “clones”.
This application was developed by NguyễnHàĐồng and released for distribution on iOS on 24 May 2013. This application became available for Android OS in 2014, and in January 2014 it became the most downloaded free game. The creator removed the game from the market on 10th February 2014. The game recorded more than 50 million downloads.
Already at the time when the original game Flappy Bird was on the market, various clones of this game for the Android OS began to appear, many of which benefited only from the success of the original. However, malware has been deliberately placed in a number of other versions, and it is estimated that up to 79% of clones of this game have been infected with malicious software. [25] Infected clones include, for example, the following products:



Infecting a mobile phone can be one of an attacker's primary targets, as these devices are typically used today for two-factor authentication of Internet banking or shopping. Attackers try to use the information obtained, for example, to withdraw funds by direct access to a user's bank account via the internet banking service or to obtain sensitive information.
Possibilities of criminal sanctions in the Czech Republic
In the Czech Republic, it is possible to punish an attack with malware according to Section 230 (Unauthorised access to a computer system and information carrier) of the Criminal Code. Possession of malware, with the intention to commit a criminal offence under Section 182 (Violation of the secrecy of transported messages) or a criminal offence under Section 230 of the Criminal Code, is a criminal offence under Section 231 (Obtaining and possession of access device and computer system passwords and other such data) of the Criminal Code.If the purpose of a virus were to obtain, for example, classified information or support from a terrorist group, an attacker could, for example, commit the crimes of Section 311 (Terrorist attack), Section 316 (Intelligence) or Section 317 (Threat of classified information) of the criminal Code in the preparation stage.
Possibilities of criminal sanctions in Poland
Violation of data integrity (viruses, trojans), 268 of the PenalCode, Art. 268a of the Penal Code. This offence concerns, inter alia, stealing personal data, making them available to third parties without the consent of the owner, as well as use them in an unauthorised way. There are financial sanctions (up to PLN 100,000) for committing these acts.
Article 268 Making it difficult for an entitled person to familiarise himself with information
§ 1. Whoever, without being entitled to do so, destroys, damages, deletes or alters a record of important information or in any other way prevents or considerably obstructs an entitled person from learning about it, shall be subject to a fine, the penalty of limitation of liberty or deprivation of liberty for up to 2 years.
§ 2. If the act specified in § 1 concerns a record on a computer data carrier, the perpetrator shall be subject to the penalty of deprivation of liberty for up to 3 years.
§ 3. Whoever, while committing the act specified in § 1 or 2, causes substantial damage to property, shall be subject to the penalty of deprivation of liberty for a term of between 3 months and 5 years.
Article 268a. Destroying, damaging, deleting, altering or impeding access to computer data
§ 1. Whoever, without being entitled to do so, destroys, damages, deletes, alters or obstructs access to computer data or substantially interferes with or prevents the automated processing, storage or transfer of such data
shall be subject to the penalty of deprivation of liberty for up to 3 years.
§ 2. Whoever, while committing the act specified in § 1, causes substantial damage to property,
shall be subject to the penalty of deprivation of liberty for a term of between 3 months and 5 years.
§ 3 The prosecution of the offence specified in § 1 or 2 shall occur on a motion of the injured
Possibilities of criminal sanctions in Portugal
According to Art. 6(2) of the Cybercrime Law, the illegal creation, distribution or dissemination of any computer programme, executable instruction, code or data intended to perform an illegal access to a computer system is penalised as being an Illegal access. The same goes for the crimes of Damage to computer programmes or other computer data [Data interference] (Art. 4(3), Computer sabotage [Illegal interference] (Art. 5(2) and Illegal interception (Art. 7(3), as the Portuguese legislator decided not to have a single provision for the misuse of devices, as the Budapest Convention (Art. 6).
[1] This is not a complete list of different types of malware. Rather, it is about defining the basic types of malware, including an explanation of how they work.
[2] There are companies specialising in “pay per install” (PPI). "PPI then causes plenty of activities leading to the installation of add-ons or other unwanted software, which (in the least harmful case) exchanges ads on websites without the user's knowledge, or inserts them where there are no ads on the site... PPI is based on the fact that those who offer these services do not pay any attention to whether the user wants to install something. They receive up to USD 1.50 per installation, so it's more than certain that fraudulent and automated installations are an essential element of their "business model."
[3] Figure of these pop-ups. For more details see Adware. [online]. [cit.10.8.2016]. Available from: http://www.mhsaoit.com/computer-networking-previous-assignments/324-lesson-16-h-the-secret-history-of-hacking
[4] [online]. [cit.10.8.2016]. Available from: https://i.ytimg.com/vi/GcvlB-EpMwA/maxresdefault.jpg
[5] E.g. an overview of the websites visited, their IP addresses, overviews of installed and used programs, records of downloads of files from the Internet, data on the structure and contents of directories stored on the hard disk, etc.
[6] [cit.8.1.2008]. Available from: http://www.spyware.cz/go.php?p=spyware&t=clanek&id=9
[7] These can be, for example: Browser Helper Object (DLL library, allowing programmers to change and monitor Internet Explorer); Hijacker (software that changes a home page of a web browser); Dialers [redirects the telephone line to expensive telephone tariffs (currently mainly attacks on mobile phones and VoIP exchanges)]; Keystroke Logger / Keylogger (keystroke monitoring); Remote Administration (allows a remote user to control a user's computer system remotely); Tracer (a program that monitors the movement of a computer system – typically a mobile device), etc.
[8] For more details see The Malware Museum. The Malware Museum @ Internet Archive. [online]. [cit.17.5.2016]. Available from: https://labsblog.f-secure.com/2016/02/05/the-malware-museum-internet-archive/
[9] More details e.g. in POŽÁR, Josef. Informační bezpečnost. Plzeň: Aleš Čeněk, 2005, p. 216 et seq.
[10] For more details cf. RAK, Roman and Radek KUMMER. Informačníhrozby v letech 2007–2017. Security magazín, 2007, vol. 14, No. 1, p. 4.
[11] Cf. JIROVSKÝ, Václav and Oldřich KRULÍK. Základní definice vztahující se k tématu. Security magazín, 2007, vol. 14, No. 2, p. 47.
[12] An overview of the most common Trojans, together with a list of their functions and communication ports, can be obtained from various websites available on the Internet. For more details cf. e.g. http://www.test.bezpecnosti.cz/full.php
[13] Cf. JIROVSKÝ, Václav. Kybernetická kriminalita. Nejen o hackingu, crackingu, virech a trojských koních bez tajemství. Prague: Grada, 2007, p. 63.
[14] These programs are sometimes referred to as scanning or scanner programs.
[15] For more detailscf. BALIGA, Arati, Liviu IFTODE and Xiaoxin CHEN. Automated Containment of Rootkits Attacks. Computers & Security, 2008, vol. 27, No. 7–8, pp. 323–334.
[16] Cf. RAK, Roman and Radek KUMMER. Informačníhrozby v letech 2007–2017. Security magazín, 2007, vol. 14, No. 1, p. 5.
[17] E.g. The DNS-Changer Trojan first attacks security programs, removing itself from the list of malicious programs, making it impossible to detect. For more details: PLETZER, Valentin. Demaskovaný spyware. CHIP, 2007, No. 10, pp. 116–120.
[18] JIROVSKÝ, Václav. Kybernetická kriminalita. Nejen o hackingu, crackingu, virech a trojských koních bez tajemství. Prague: Grada, 2007, p. 65
[19] Capturing keystrokes and information about running files. [online]. [cit.10.8.2016]. Available from: http://img.zerosecurity.org/files/2013/10/Keylogger-software-logfile-example.jpg
[20] [online]. [cit.10.7.2016]. Available from: https://image.slidesharecdn.com/delljointevent2014november-onur-141105074412-conversion-gate02/95/end-to-end-security-with-palo-alto-networks-onur-kasap-engineer-palo-alto-networks-23-638.jpg?cb=1415174438
[21] Hyper Text Markup Language – This is the name of the markup language used to create web pages.
[22] Two versions of fake antivirus. [online]. [cit.10.8.2016]. Available from: http://www.cctslo.com/images/fake-personal-antivirus.jpg
[23] For more details, see e.g. Stuxnet. [online]. [cit.23.7.2016]. Available from: https://cs.wikipedia.org/wiki/Stuxnet
[24] The very first mobile malware: how Kaspersky Lab discovered Cabir. [online]. [cit.29.6.2015]. Available from: http://www.kaspersky.com/about/news/virus/2014/The-very-first-mobile-malware-how-Kaspersky-Lab-discovered-Cabir
See also e.g.:
Škodlivý kód cílí na mobily, šíří se jako lavina. [online]. [cit.17.5.2016]. Available from: https://www.novinky.cz/internet-a-pc/bezpecnost/401956-skodlivy-kod-cili-na-mobily-siri-se-jako-lavina.html
Warning! Over 900 Milion Android Phones Vulnerable to New „QuadRooter“ Attack.[online]. [cit.10.8.2016]. Available from: https://thehackernews.com/2016/08/hack-android-phone.html
[25] For more details, see e.g.Flappy Bird Clones Help Mobile Malware Rates Soar.[online]. [cit.14.8.2016]. Available from: http://www.mcafee.com/us/security-awareness/articles/flappy-bird-clones.aspx
