Cyber-attacks detection and prevention
4. Manifestations of cybercrime
4.2. Botnet
Botnet can be simply defined as a network of software-linked bots [1] that perform an action based on a command from the “owner” (or administrator) of that network. The network built in this way can be used for legal activities (e.g. distributed computing) or for illegal activities (see below).
It was the distributed calculations that, in fact, inadvertently gave criminals the idea of building botnets the way they are understood today. The following text is from a website about distributed computing: “Most computers in the world use their full computing potential for only a very small part of their operating time, but their electricity consumption is only slightly lower than if they were fully utilised. It's a shame not to use this lounging computer, and very few people realise how much such unused power there is in the world… In distributed computing, the saying “There's no need for a shower, a few drops help too" applies in full, and drops from millions of ordinary computers in the world exceeds several times the performance of even the largest supercomputers in the world… Involvement in any distributed computing project consists only in the installation of the client, and it can usually perform all the necessary activities and take care of specific applications… Most projects work so that the total work is divided into lots of parts and these are then sent to individual computers, which request them. After processing each piece, the individual computers themselves send the resulting data back to the project centre, where the results are combined again into one unit.” [2]
The very idea of resource distribution, or the use of low computing power of other computer systems, for example for calculating complex mathematical algorithms, etc., is definitely not bad and is much more efficient than the use and construction of “supercomputers”. However, as humans we are very inventive, so it was obvious that this idea would be used for purposes other than altruism or charity. The ability to distribute different tasks among different geographically located computers has been and is attractive to attackers.
The current computer system, for example, in the form of a mail server, has no problem sending tens of millions or billions of e-mail messages a day. If a user decides to use this system, for example, to spread spam, this computer system (traceable by identifiers such as IP address) will perform this activity only for a very short time as it will be blocked very soon by the ISP (e.g. due to illegitimate or excessive traffic in the network, which can be marked as spam); its address will appear on the “blacklists”, and based on this information traffic will be blocked (e.g. outgoing mail). However, if an attacker uses distributed power in the form of a botnet, he will have thousands to hundreds of thousands of computers, each of which sends a portion of messages (e.g. 1000–2000 messages per day). Such traffic will then not be considered problematic and will not be stopped.
It is typical for a botnet that if a target computer system is infected, this system, called “zombie” or “bot”, connects to a central control server [called a command-and-control server (C&C)]. The whole system (containing zombies and C&C) is controlled by an attacker (referred to as a botmaster or botherder) who controls the bots via a C&C server. [3]
The following elements are characteristic (necessary) for the botnet:
1. Command-and-control infrastructure (C&C)
It is infrastructure that consists of a control element (or elements) and bots (controlled by computer systems).
2. Installation and control of a bot
This is most often malware that is spread through a botnet or otherwise. The primary goal of such malware is to integrate other computer systems into a botnet. Malware exploits various vulnerabilities in computer systems.
3. Controlling bots through C&C infrastructure
A bot is software that works secretly and uses common communication channels (IRC, IM, RFC 1459, etc.) to communicate with a C&C server. New bots try to get as much information as possible from their surroundings and promote themselves to other computer systems.
Based on the architecture, there are botnets with:
1. Centralised architecture
This architecture is typically built on the principle of client-server communication. End computer systems (zombies/bots) communicate directly with the C&C server (central control element) and follow instructions and use resources from this server.
2. Decentralised architecture
It is typically built on peer-to-peer (P2P) architecture. This architecture allows resources and commands to be shared within a P2P network. There is no central control element in the “classic” form, which makes this system more resistant to the attempt to take control through this control element.
Botnets can be used for many activities, but financial gain is mainly in the foreground, which consists in generating their own attacks (e.g. ransomware, phishing, spam, stealing information, DDoS, etc.), as well as renting their services or the entire botnet to clients. Thanks to the above, it is possible to include the botnet in the structure of crime-as-a-service (where the service is offered: botnet-as-a-service), or in the malware economy [6] , where it represents the basic technical platform necessary to perform a number of cyberattacks.
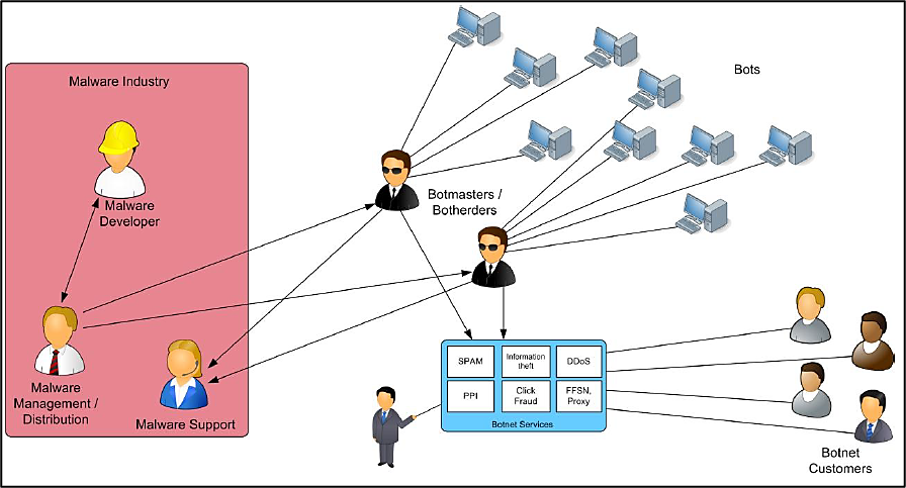
Malware economy
The computer system that becomes part of the botnet is then typically used for one of the activities described in the following table. It should be noted that these attacks are usually combined or distributed within the botnet with respect to its occupancy, demand from “customers”, etc.
|
Sending of |
Identity Theft |
DoS Attacks |
Click Fraud |
|
– spam – phishing – malware – adware – spyware |
Personal and sensitive data
and information is obtained and sent (back to the attacker). |
Launching a DoS attack against
a target (computer system) specified by the botmaster. |
The computer system displays (or clicks on) advertising links on the site without the user's knowledge. This gives the impression that the site has traffic and advertisers are losing money. [7] |
In the table below I summarise a list of some known botnets [8] :
|
Creation date |
End date |
Name |
Estimated number of bots |
Number of spam in billions per day |
Alias (also known as) |
More information |
|
2002 |
|
|
|
|
|
|
|
|
2011 |
2,300,000 |
|
|
Backdoor. Collection of personal and sensitive information. |
|
|
2004 |
|
|
|
|
|
|
|
230,000[16] |
5.7 |
Beagle, Mitglieder, Lodeight |
Massive sending of spam. Designed for computer systems with Windows OS. |
|||
|
Marina Botnet |
6,215,000[16] |
92 |
DamonBriant, BOB.dc, Cotmonger, Hacktool.Spammer, Kraken |
|
||
|
180,000[17] |
Sinowal, Anserin |
Distribution of malware and collection of sensitive and personal data. Designed for computer systems with Windows OS. |
||||
|
160,000[18] |
3 |
Nuwar, Peacomm, Zhelatin |
Sending of spam. Designed for computer systems with Windows OS. |
|||
|
2006 |
|
|
|
|
|
|
|
March 2011 |
150,000[19] |
30 |
RKRustok, Costrat |
Sending of spam. Capable of sending up to 25,000 spam messages per hour from one computer. Active on Windows OS. |
||
|
125,000[20] |
0.8 |
Buzus, Bachsoy |
Sending mainly pharmaceutical spam. |
|||
|
2007 |
|
|
|
|
|
|
|
1,500,000[21] |
74 |
Pandex, Mutant (related to: Wigon, Pushdo) |
Sending of spam. By default, it uses the Pushdo Trojan to infect a computer system. Active on Windows OS. |
|||
|
1,300,000[22] |
Backdoor, allowing you to take control of an infected computer. After installation, it collected data, stopped processes, or launched DDoS attacks. |
|||||
|
March 2007 |
November 2008 |
450,000[23] |
60 |
Cbeplay, Exchanger |
Primarily sending spam. The Srizbi trojan was used to infect computer systems. |
|
|
260,000[16] |
2 |
none |
Sending mainly pharmaceutical spam. |
|||
|
September 2007 |
dBot |
10,000+ (Europe) |
dentaoBot, d-net, SDBOT |
|
||
|
10,000[16] |
0.15 |
Rlsloup, Pixoliz |
Sending of spam. |
|||
|
2008 |
|
|
|
|
|
|
|
1,000,000[24] |
Sector, Kuku |
Malware group. Computer systems infected with Sality communicate through P2P. The activity consists of: sending spam, collecting sensitive data, attacking web servers, performing distributed calculations (e.g. for password cracking, etc.). Active on Windows OS. |
||||
|
April 2008 |
|
495,000[33] |
9 |
Kracken |
Malware distribution. Connecting other computers to the botnet. |
|
|
December 2009 |
12,000,000[25] |
Botnet primarily involved in scam and DDoS attacks. It was one of the biggest botnets ever. |
||||
|
November 2008 |
10.500,000+[26] |
10 |
DownUp, DownAndUp, DownAdUp, Kido |
Worm attacking computer systems with Windows OS. The bugs of this OS were used to further expand the botnet. |
||
|
November 2008 |
March 2010 |
80,000[27] |
1.5 |
Waled, Waledpak |
Sending of spam and distribution of malware. Terminated by Microsoft action. |
|
|
Maazben |
50,000[16] |
0.5 |
None |
Sending of spam, malware, scam, phishing. |
||
|
OnewordSub |
40,000[28] |
1.8 |
|
|||
|
Gheg |
30,000[16] |
0.24 |
Tofsee, Mondera |
|
||
|
Nucrypt |
20,000[28] |
5 |
Loosky, Locksky |
|
||
|
Wopla |
20,000[28] |
0.6 |
Pokier, Slogger, Cryptic |
|
||
|
15,000[29] |
Danmec, Hydraflux |
Phishing attacks, SQL injections, spread of malware. |
||||
|
12,000[28] |
0.35 |
Spam-DComServ, Covesmer, Xmiler |
Using P2P
|
|||
|
|
19/07/2012 |
560,000[31] |
39.9 |
Tedroo |
Sending mainly pharmaceutical spam. |
|
|
|
||||||
|
2009 |
|
|
|
|
|
|
|
May 2009 |
November 2010 |
30,000,000[30] |
3.6 |
Oficla |
Sending of spam. Ended by a joint action of the Dutch police, Govcert NL, Europol. Kaspersky Lab etc. Probably the largest known botnet. |
|
|
|
November 2009 |
509,000[32] |
10 |
Ozdok |
Sending of spam. |
|
|
August 2009 |
250,000[34] |
2.25 |
Spamnost |
Sending spam and performing DDoS attacks. |
||
|
2010 |
|
|
|
|
|
|
|
January 2010 |
LowSec |
11,000+[16] |
0.5 |
LowSecurity, FreeMoney, Ring0.Tools |
|
|
|
4,500,000[35] |
TDSS, Alureon |
|
||||
|
3,600,000 (US only)[36] |
Zbot, PRG, Wsnpoem, Gorhax, Kneber |
Focused on activities related to the theft of bank account information. It also installed CryptoLocker ransomware, etc. Active on Windows OS. |
||||
|
(Several: 2011, 2012) |
300,000+ |
4 |
Hlux |
Mostly involved in Bitcoin theft and sending spam. |
||
|
2011 |
|
|
|
|
|
|
|
2015-02 |
3,000,000[37] |
Worm attacking computer systems with Windows OS. Terminated by a joint action of Europol and Symantec. |
||||
|
|
|
2,000,000 |
|
Max++ Sirefef |
Botnet used mainly for mining bitcoins and click fraud. Active on Windows OS. |
|
|
2012 |
|
|
|
|
|
|
|
120,000 |
None |
Click Fraud |
||||
|
|
|
|
|
|
Botnet involved in the spread of malware and DDoS attacks. Most zombies (up to 85%) are located in China. The botnet client was found in computer systems delivered directly from the factory. |
|
|
2013 |
|
|
|
|
|
|
|
|
|
Boatnet |
500+ server computers |
0.01 |
YOLOBotnet |
|
|
|
|
Zer0n3t |
200+ server computers |
4 |
FiberOptck, OptckFiber, Fib3rl0g1c |
|
|
2014 |
|
|
|
|
|
|
|
|
|
300,000+ |
|
Soundfrost |
Sending of spam. |
|
|
|
|
6,000,000 |
|
|
|
|
|
2016 |
|
|
|
|
|
|
|
|
|
380,000 |
|
|
DDoS, sending of spam. |
|
|
|
|
Methbot |
6,000 domains and 250,267 distinct URLs |
|
|
|
|
2018 |
|
|
|
|
|
|
|
|
|
3ve |
1.7 million computers and a large number of servers |
|
|
Money theft. |
In fact, any computer system can be connected to a botnet network. Among other things, these are systems that satisfy the requirements of IoT (Internet of Things). In 2014, a case was reported in which a botnet included a fridge sending out more than 750,000 spam e-mails. [9]
The Nigam study shows [10] that there are dozens of botnets directly created and primarily focused on computer systems, which we can call mobile devices (e.g. smartphones, tablets, etc.). Due to the installation of applications from unknown sources and the considerable absence of antivirus products on users' mobile devices, it is also much easier to install malware on these mobile devices and thus gain control over them. These devices are currently able to fully meet the requirements of a botmaster for the operation of a botnet, or for the tasks assigned to “zombies”.
Malware serves as a means of gaining access, control, and further spread of malware or other tasks as directed by an attacker, and not only in the case of botnets. However, if malware is currently infected on a user's computer system, it is highly likely that it has become part of the botnet. An attacker (botmaster) installs malware on a computer system (zombie) that allows him to manipulate the computer system remotely (malware No. 1 – while this malware leaves control to the botmaster even if, for example, part or all of the botnet is leased). Only then is another malicious software (malware 2. to malware ∞) installed to perform other tasks (e.g. sending spam, collecting data, extortion using ransomware, etc.). The whole structure can be illustrated as follows:
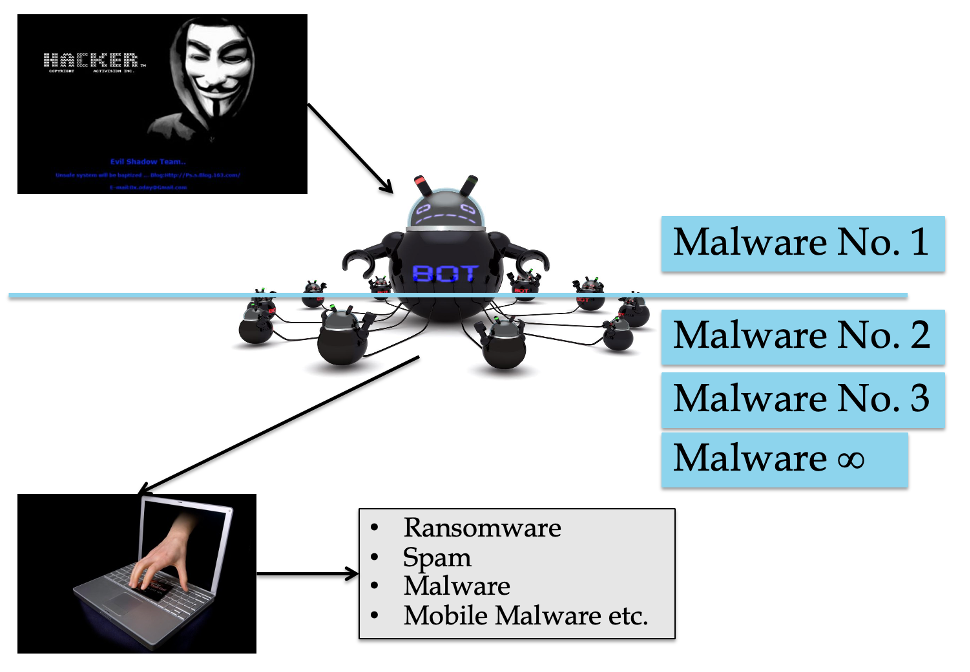
Malware installed on a computer system connected to a botnet
From a legal perspective, it can be stated that botnets represent entire networks of infected computer systems over which a third party has taken over some control without authorisation, without the knowledge of authorised users. Such infected systems most often serve as a base for anonymous connection of an attacker to the Internet, for sending malicious programs, carrying out attacks on other targets, carrying out DoS attacks, spreading spam, identity theft or other cyberattacks.
Possibilities of criminal sanctions in the Czech Republic
As for an attacker's own activity, which consists in the installation of malware for the subsequent control of a computer system, it is possible to assess this conduct according to Section 230 of the Criminal Code (Unauthorised access to the computer system and information carrier). If an attacker put malware into a computer system with the intention of causing damage or other harm to another or gaining an unauthorised benefit to himself or another, his actions could be qualified according to Section 230 (2) (d) of the Criminal Code.
It can be argued that it is also an unauthorised use of another’s possession (because the computer system in question is another’s possession in these cases) under Section 207 (1) al. (1) of the Criminal Code. Application of Section 207 (1) al. (2) of the Criminal Code [11] can be quite problematic, as the intensity of intervention and use of the computer system is decisive. On the basis of this degree of intensity, it would be possible, if appropriate, to quantify the damage incurred as an expression of depreciation at the time of use. Unfortunately, when using this calculation the caused damage is not small.
The actual protection against connection and use of computers within the botnet can have two levels. The first level is to increase the protection of property rights by supplementing Section 207 of the Criminal Code with the basic objective element, the wording of which could be as follows: “Who will use a computer system without the consent of the entitled person.”
This provision would also define the circumstance which consists in interfering with the ownership rights of another. In the case of unauthorised use of another's possession in relation to a computer system, the solution is not to reduce the damage from not small to insignificant (see Section 207 (1) al. (1) of the Criminal Code, as the price of many computer systems is currently lower than at least CZK 5,000), and yet these computer systems are able to fully perform the assigned activity within the botnet.
The second level, which describes the seriousness of the attacker's actions, then consists in the inclusion of a new qualification circumstance in Section 230 (3) of the Criminal Code, while this circumstance could be as follows:
“intentionally connects a computer system to a computer network with the intention of committing a crime or uses it on that network with the same intention"
Possibilities of criminal sanctions in Poland
Illegal access to a system (hacking) - Art. 267 § 1 and 2 of the Penal Code. This crime is prosecuted at the request of the aggrieved party. They are punishable by a fine, restriction of liberty or imprisonment for up to 2 years.
Article 267 Unlawful obtaining of information
§ 1. Whoever, without authorisation, gains access to information not intended for him, by opening a closed magazine, connecting to a telecommunications network or breaking or bypassing electronic, magnetic, IT or other specific protection thereof, shall be subject to a fine, the penalty of limitation of liberty or deprivation of liberty for up to 2 years.§ 2. The same punishment shall be imposed on anyone, who without authorisation, gains access to the whole or any part of an IT system.
§ 3. The same punishment shall be imposed on anyone, who in order to obtain information to which he is not entitled, establishes or uses an eavesdropping or visual device, or other device or software.
§ 4. The same punishment shall be imposed on anyone who discloses information obtained in the manner specified in § 1-3 to another person.
§ 5. The prosecution of the offence specified in § 1-4 shall occur on the motion of the injured person.
Possibilities of criminal sanctions in Portugal
According to Art. 6(2) of the Cybercrime Law, the illegal introduction in one or several computer devices of any computer programme, executable instruction, code or data intended to perform an illegal to a computer system is penalised as being an Illegal access. The same goes for the crimes of Damage to computer programmes or other computer data [Data interference] (Art. 4(3), Computer sabotage [Illegal interference] (Art. 5(2) and also Illegal interception (Art. 7(3).
Besides, there are not in place any provisions related to the building or use of networks for performing any of the stated offence.
[1] Bot (abbreviation of the word robot). It is a program that can execute an attacker’s commands entered from another computer system. Most often it is an infection of a computer with a virus such as worm, Trojan horse, etc. The computer system, which is thus remotely controlled, is then referred to as a zombie. However, some sources even refer to an infected computer system as a bot.
A bot can collect data, process requests, send messages, communicate with a control element, etc.
[2] For more details see Distribuovanévýpočty. [online]. [cit.2.11.2013]. Available from: http://dc.czechnationalteam.cz/
[3] For more details see: PLOHMANN, Daniel, Elmar GERHARDS-PADILLA and Felix LEDER. Botnets: Detection, Measurement, Disinfection & Defence. ENISA, 2011. [online]. [cit.17.5.2015], p. 14. Available from: https://www.enisa.europa.eu/publications/botnets-measurement-detection-disinfection-and-defence
Further botnet definitions and information about them can be found, for example, at:
Co je to botnet a jak sešíří?[online]. [cit.15.7.2016]. Availablefrom: https://www.youtube.com/watch?v=ywXqDon5Xtg
Botnety: nová internetová hrozba. [online]. [cit.15.7.2016]. Available from: http://www.lupa.cz/clanky/botnety-internetova-hrozba/
Války síťových robotů – jak fungují sítě botnets.[online]. [cit.15.7.2016]. Available from: http://tmp.testnet-8.net/docs/h9_botnet.pdf
Botnets. [online]. [cit.15.7.2016]. Available from: https://www.youtube.com/watch?v=-8FUstzPixU&index=2&list=PLz4vMsOKdWVHb06dLjXS9B9Z-yFbzUWI6
[4] Figure of a centralised botnet. For more details see: PLOHMANN, Daniel, Elmar GERHARDS-PADILLA and Felix LEDER. Botnets: Detection, Measurement, Disinfection & Defence. ENISA, 2011. [online]. [cit.17.5.2015], p. 16. Available from: https://www.enisa.europa.eu/publications/botnets-measurement-detection-disinfection-and-defence
[5] Figure of a decentralised botnet. Ibidem, p. 18
[6] Malware economy. For more details see: PLOHMANN, Daniel, Elmar GERHARDS-PADILLA and Felix LEDER. Botnets: Detection, Measurement, Disinfection & Defence. ENISA, 2011. [online]. [cit.17.5.2015], p. 21. Available from: https://www.enisa.europa.eu/publications/botnets-measurement-detection-disinfection-and-defence
[7] Bots and Botnets – A growing Threat. [online]. [cit.11.8.2016]. Available from: https://us.norton.com/botnet/
[8] The table was created based on a combination of information from the following sources:
Botnet. [online]. [cit.15.7.2016]. Available from: https://en.wikipedia.org/wiki/Botnet
Botnet – Historical List of Botnets. [online]. [cit.15.8.2016]. Availablefrom: http://www.liquisearch.com/botnet/historical_list_of_botnets
Botnet. [cit.8.7.2016]. Availablefrom: http://research.omicsgroup.org/index.php/Botnet
Historical list of botnets. [online]. [cit.15.8.2016]. Available from: http://jpdias.me/botnet-lab//history/historical-list-of-botnets.html
[9] Fridge caught sending spam e-mails in botnet attack. [online]. [cit.17.5.2016]. Available from: http://www.cnet.com/news/fridge-caught-sending-spam-emails-in-botnet-attack/
[10] For more details see NIGAM, Ruchna. A timeline of Mobile Botnets. [online]. [cit.12.7.2016]. Available from: https://www.botconf.eu/wp-content/uploads/2014/12/2014-2.2-A-Timeline-of-Mobile-Botnets-PAPER.pdf
[11] This provision provides for damage to other people's property, while the damage does not have to be small (i.e. at least CZK 25,000, see Section 138 (1) of the Criminal Code).

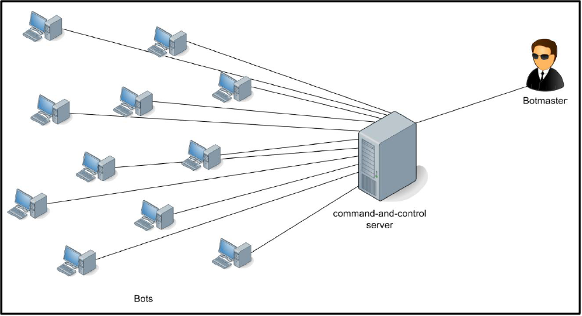 [4]
[4]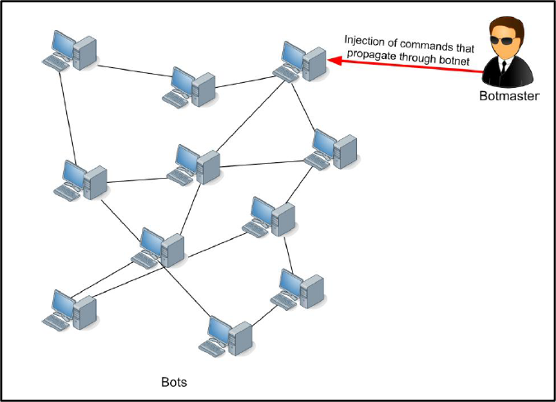 [5]
[5]