Cyber-attacks detection and prevention
2. The concept of cybercrime and related concepts
2.3. Cyberattack
Prosise and Mandiva characterise a “computer security event” (which can be understood as a computer attack or computer crime), as an illegal, unauthorised, unacceptable action that involves a computer system or computer network. Such an action may focus, for example, on the theft of personal data, spam or other harassment, embezzlement, dissemination or possession of child pornography, etc.[1]
Jirásek et al. define a cyberattack as: “An attack on an IT infrastructure to cause damage and obtain sensitive or strategically important information. It is most often used in the context of politically or militarily motivated attacks."[2]
Such a definition of a cyberattack would significantly narrow and not affect all the negative activities of cyberspace users[3], especially because it cumulatively combines the conditions for IT damage and information retrieval. A cyberattack can also include actions in the form of social engineering, where the only goal is to obtain information, or, conversely, a DoS or DDoS attack, where the only goal may be to suppress (i.e. not damage) the functionality of one or more computer systems or services.
Based on the above, a cyberattack[4] can therefore be defined as any illegal conduct by an attacker in cyberspace that is directed against the interests of another person. These acts do not always take the form of a crime. Their essential characteristic is that they disrupt the injured party's normal way of life. A cyberattack counts whether completed, in preparation or at a trial stage.[5]
A cybercrime must also be a cyberattack, but not every cyberattack must be a crime. Many cyberattacks, even due to the absence of a criminal law standard, can be subsumed under conduct that will be by its nature an administrative or civil tort, or it may not be conduct that is punishable by any legal standard. (It can be, for example, only an immoral or unwanted conduct.)
The success of a cyberattack typically lies in the breach of one of the elements that make up cybersecurity (people, processes, and technologies). These elements need to be applied or modified throughout their life cycle.In particular, they concern prevention, detection and response to attack. The security of IT, information and data is also directly dependent on respecting the principles of “C”, “I” and “A”.
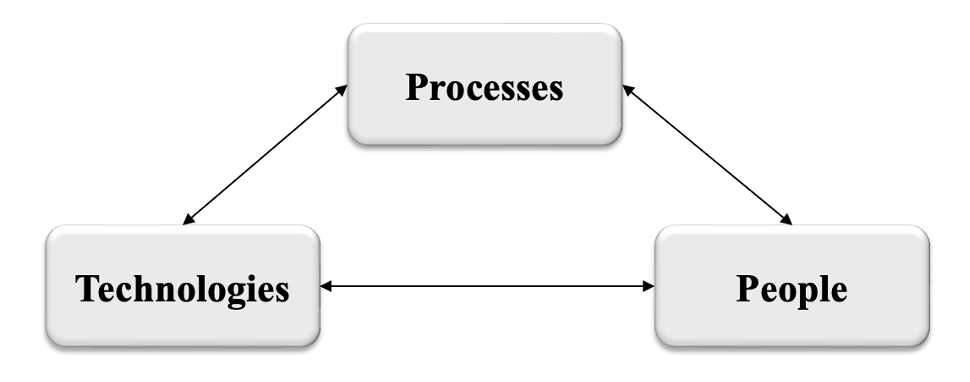
Elements of cybersecurity
If we want to define the term cyberattack, it is appropriate to use the definitions that result from Act No. 181/2014 Sb., on Cybersecurity and on the Amendment of Related Acts (Act on Cybersecurity).[6] This Act defines in Section 7 the terms of cybersecurity event and cybersecurity incident. Cybersecurity event is “an event that may cause a breach in information security in information systems or a breach in security of services or security and integrity of electronic communications networks.” In fact, it is an event without a real negative consequence for a given communication or information system. In essence, it is only a threat, but it must be real.
A cybersecurity incident is “a breach in the security of information in information systems or a breach in the security of service provision or a breach of security and integrity of electronic communication networks due to a cybersecurity event.” A cybersecurity incident thus represents a real breach of information security in information systems or a breach in the security of services or the security and integrity of electronic communications networks, i.e. a breach of an information or communication system having a negative impact.
[1] PROSISE, Chris and Kevin MANDIVA. Incident Response & Computer Forensic, second edition. Emeryville: McGraw-Hill, 2003, p. 13
See also: CASEY, Eoghan. Digital Evidence and Computer Crime: Forensic Science, Computers, and the Internet, Second Edition. London: Academic Press, 2004, p. 9 et seq.
[2] JIRÁSEK, Petr, Luděk NOVÁK and Josef POŽÁR. Výkladovýslovníkkybernetickébezpečnosti. [online]. 2nd updated edition. Prague: AFCEA, 2015, p. 59. Availablefrom: http://afcea.cz/cesky-slovnik-pojmu-kyberneticke-bezpecnosti/
[3] The above definition especially lacks a definition of any motivation of the attacker other than that... causing damage or gain to strategically important information.An example not covered by this definition can be economically motivated attacks, which are dramatically growing at present.
[4] It is necessary to distinguish the concept of a cyberattack from the concept of a security incident, which represents a breach of IS/IT security and the rules defined for its protection (security policy).
[5] E.g. Conficker virus attack created by Botnet. This completed the attack. However, the question remains as to what purposes this network may be used for. (It may be in preparation for a much more serious cyberattack.)
[6] Hereinafter referred to as the Act on Cybersecurity, or AoCS.
