CSIRTs and CERTs
1. Cybersecurity
1.2. Principles of cybersecurity
When applying cybersecurity, the following principles are instituted, which are also called the triads of cybersecurity. [1]
For the purposes of this monograph, the following three triads will be defined:
1. CIA (C – Confidentiality; I – Integrity; A – Availability).
2. Elements of cybersecurity (People, Technology, Processes).
3. Cybersecurity life cycle (Prevention, Detection, Response).
1.2.1 The CIA Triad
The best known and most widely used triad of cybersecurity is the CIA triad, but the simple use of this basic triad of cybersecurity principles without putting in place other principles is currently insufficient to maintain an adequate level of cybersecurity.
In the literature, for example, reference is made to the application of the Parkerian hexad [2] , which is essentially the CIA triad, but supplemented by three other elements: P/C – Possession/Control, A – Authenticity and U – Utility.
The purpose of cybersecurity is to ensure both the security of ICT as such and, in particular, the data and information that are transmitted, processed and stored by these elements.
Very often, the CIA triad is primarily related to information.
This narrower concept results mainly from the very definition of information security, which focuses on information protection. Under this protection, the type of carrier (paper, electronic media, etc.) or information processing system is not an issue. Information security is then applied to information throughout its life cycle.
Information security is also defined by a number of ISO 27000 standards. The basic information security standards include:
- ISO/IEC 27001:2014 Information technology – Security techniques – Information security management systems – Requirements
- ISO/IEC 27002:2014 Information technology – Security techniques – Code of practice for information security controls
The question is whether the definition of information security is currently adequate and sufficient, or whether it applies to all key elements of security in cyberspace.
Despite the fact that the term information security is more commonly used in professional literature and procedural rules, we are convinced that in relation to activities related to the use of ICT or to activities related to cyberspace, the term cybersecurity is a more appropriate term.
As mentioned above: "information security refers to information as such". However, this omits key elements related to security in cyberspace.
We consider these important elements to be data and then the computer systems themselves (or individual elements of ICT), which enable the actual transmission of data and information.
There are a number of definitions of the terms data and information in the professional literature and in the legislation. For the purposes of this publication, definitions are selected that relate to the protection of information, data or cybersecurity.
According to the Convention on Cybercrime [3] , computer data means “any representation of facts, information or concepts in a form suitable for processing in a computer system, including a program suitable to cause a computer system to perform a function."
Thus, data is any element with an information value that is processed by a computer system, and is processed to subsequently create information.
Information “is data that has been processed into a form useful to a recipient. So every piece of information is a piece of data, but any stored data doesn't necessarily become information." [4]
Wiener states that “information is the name for the content of what is exchanged with the outside world as we adjust to it and make our adjustment felt upon it.” He also says that information is neither matter nor energy, but a separate physical category. [5]
Information is therefore perceived as something “more qualified” than data. Data are facts that become information when they are perceived or expressed in context and have a meaning that is understandable to people. [6]
It is the connection of “insignificant” data and the creation of a certain context, which only composes “significant” information from the data, which can be key from the point of view of cybersecurity. If we respect the above-mentioned thesis of information security, within which only information as such is protected, then there could be a significant security breach.
The following graph demonstrates the relationship between data and information. [7]
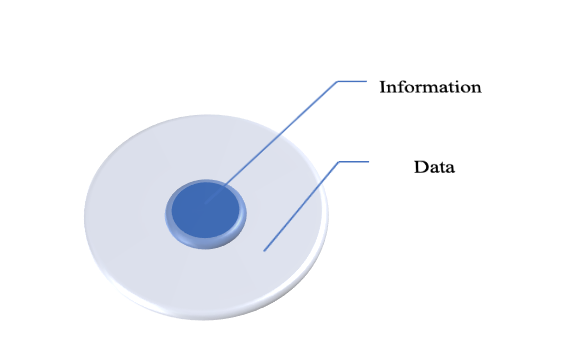
Data and information are transmitted within cyberspace using computer systems [8] , which are an integral part of cyber- or information security.
Based on the above, we are convinced that the CIA [9] triad should be applied not only to the information itself, but also to other elements of cybersecurity (data, computer systems, etc.)
Confidentiality
Confidentiality means a situation where only such entities that are authorised to do so have access to information, data or ICT.
Given the large amount of processed information, it is appropriate to introduce or apply one of the classifications of information. These classifications can then be applied to other elements of cybersecurity and access to them.
ISO/IEC 27000 security standards define that:
- "Information should be classified according to its value, legal requirements, sensitivity and criticality.”
- "Procedures in accordance with the classification scheme adopted by an organisation should be established and implemented for the marking and handling of information.”
- "In order to prevent unauthorised access to or misuse of information, rules should be laid down for the handling and storage of information.”
Examples of some classification schemes:
1. Classification of information according to Act 412/2005 Sb., on the Protection of Classified Information and on Security Clearance [10] :
- Top secret – unauthorised handling of information could cause extremely serious harm to the interests of the Czech Republic.
- Secret – unauthorised handling of information could cause substantial harm to the interests of the Czech Republic.
- Confidential – unauthorised handling of information could cause simple harm to the interests of the Czech Republic.
- Restricted – unauthorised handling of information could be disadvantageous to the interests of the Czech Republic.
2. Classification of information used in the commercial sphere:
- Protected – unauthorised handling of information could cause substantial damage or destruction of the organisation (e.g. leakage of strategic information, source code, security schemes, passwords, etc.).
- Internal – unauthorised handling of information could cause damage to the organisation (e.g. leakage of personal data, contracts, etc.).
- Sensitive – unauthorised handling of information could have a negative impact on the company (e.g. previously unpublished information about projects, planned events, etc.).
- Public – unauthorised handling of information should not harm anyone and should not have any impact on the company (e.g. publicly available contacts, project presentations, etc.). [11]
In addition to the two classifications mentioned above, there are a number of other classifications that are accepted by organisations or individuals, either on the basis of legislation or at the discretion of the user.
The classifications, provided they are respected and adhered to, can significantly mitigate the impact of a possible cyberattack.
3. Traffic Light Protocol
Within the cybersecurity community, there has been a need in the past to share sensitive information and data (typically about cyberattacks). For this reason, the TLP (Traffic Light Protocol) [12] was created in the National Infrastructure Security Coordination Center [13] in early 2000. This protocol aims to speed up the exchange of information between stakeholders and at the same time lays down rules for the handling of transmitted information. The entity that transmits information (the source of the information) always marks the information with a certain colour that determines how the recipient should handle the information.
The TLP protocol is best defined in the following table, which was taken from US-CERT [14] :
|
Colour |
When to use |
How to share? |
|
TLP:RED |
Entities may use TLP: RED in cases where the information does not allow for an effective response by other entities and could lead to implications for the privacy, reputation or operations of those entities if misused. |
Recipients may not share information classified in the TLP: RED category with any entity other than the specific exchange, meeting or conversation in which the TLP:RED information was originally disclosed. For example, in a meeting, the TLP: RED information is limited to those who are directly attending the meeting. In most cases, information marked TLP: RED should only be exchanged verbally or in person. |
|
TLP:AMBER |
Entities may use TLP: AMBER in cases where information requires an effective response from other entities and poses a risk to privacy, reputation or operations, if it is shared outside the participating organisations. |
Recipients may share information classified in the TLP: AMBER category with members of their own organisation and with clients or customers who need to know this information in order to protect or prevent further potential harm. Entities are free to set additional sharing rules, and these must be followed. |
|
TLP:GREEN |
Entities may use TLP: GREEN if the information is useful to raise awareness among all participating organisations. It is also possible to share this information with other entities within a wider community or sector. |
Recipients may share information classified in the TLP: GREEN category with partners and partner organisations within their sector or community. However, information cannot be shared through publicly accessible channels. Information in this category can be massively disseminated within a given community. Information included in the TLP: GREEN category may not be released outside the community. |
|
TLP:WHITE |
Entities may use TLP: WHITE if information contains little or no foreseeable risk of misuse in accordance with applicable disclosure rules and procedures. |
In accordance with the rules and copyright protection, information included in the TLP: WHITE category may be distributed without restriction. |
“In cybersecurity, unwanted disclosure of certain information is referred to as a breach of its confidentiality or leakage.” [15]
4. Confidentiality assessment according to Decree No. 82/2018 Sb., on Security Measures, Cybersecurity Incidents, Reactive Measures, Requirements for Filing in the Field of Cybersecurity and Data Disposal (Decree on Cybersecurity) [16]
The Decree on Cybersecurity largely takes over the Traffic Light Protocol mentioned above for the confidentiality rating scale (see Appendix 1 to the DoCS).
|
Level |
Description |
Examples of asset protection requirements |
|
Low |
Assets are publicly available or were intended for disclosure. Breach
of asset confidentiality does not jeopardise legitimate interests of an
obligor. |
No protection is required. |
|
Medium |
Assets are not publicly available and constitute the know-how of an obligor; the protection of assets is not required by any piece of legislation or contractual arrangement. In the case of sharing such an asset with third parties and using the classification according to the TLP, the TLP:GREEN or TLP:AMBER designation is used in particular. |
Access control tools are used to protect confidentiality. |
|
High |
Assets are not publicly available and their protection is required by
legal regulations, other regulations or contractual arrangements (e.g. trade
secrets, personal data). |
Tools to ensure access control and recording are used to protect
confidentiality. Transmissions of information over communication networks are
protected by cryptographic means. |
|
Critical |
Assets are not publicly available and require an above-standard level
of protection beyond the previous category (e.g. strategic trade secrets,
special categories of personal data). |
Tools to ensure access control and recording are used to protect
confidentiality. Furthermore, methods of protection preventing a misuse of
assets by administrators. Transmissions of information are protected by
cryptographic means. |
Integrity
According to the Cybersecurity Glossary [17] , integrity is defined as “the property of accuracy and completeness.” Data integrity is then defined in the same glossary as “certainty that data has not been altered. It also refers to the validity, consistency and accuracy of data, such as databases or file systems. It is provided by checksums, hash functions, self-healing codes, redundancy, journaling, etc. In cryptography and information security in general, integrity means data validity." System integrity is then “a property that the system performs its intended function in an undisturbed manner, without intentional or accidental non-automated manipulation with the system.”
Integrity therefore represents the impossibility of interfering with information, data, computer systems, their settings, etc. by a person other than the one authorised to do so.
At the same time, integrity is a kind of guarantee of the integrity of the system, information or data.
"Unwanted modification (alteration) is therefore referred to in information security as a breach of integrity." [18]
In the event of an integrity violation, be aware that if an unwanted change to the data occurs, the unwanted change may not be detected at all and a considerable amount of time may elapse before the integrity violation is detected.
The Decree on Cybersecurity in Appendix 1 also represents a scale for assessing integrity.
|
Level |
Description |
Examples of asset protection requirements |
|
Low |
Assets do not require protection in terms of integrity. Breach of asset integrity does not jeopardise the legitimate interests of an obligor. |
No protection is required. |
|
Medium |
Assets may require protection in terms of integrity. A breach of the integrity of an asset may damage the legitimate interests of an obligor and may have less serious effects on the primary assets. |
Standard tools (such as restrictions on write access rights) are used to protect integrity. |
|
High |
Assets require protection in terms of integrity. A breach of the integrity of an asset leads to damage to the legitimate interests of an obligor with significant effects on the primary assets. |
To protect integrity, special means are used that allow to track the history of changes made and record the identity of the person making the change. Protection of the integrity of information transmitted by communication networks is ensured by cryptographic means. |
|
Critical |
Assets require protection in terms of integrity. A breach of integrity leads to very serious damage to the legitimate interests of an obligor with direct and very serious effects on the primary assets. |
To protect integrity, special means are used to uniquely identify the person making the change (for example, using digital signature technology). |
Availability
According to the Cybersecurity Glossary [19] , availability is defined as “a property of accessibility and usability at the request of an authorised entity.”
Availability can therefore be defined as a guarantee of access to information, data or a computer system at the moment of need. No matter how system ensuring integrity and allowing access to the system itself, data or information is, it will be unusable if it does not provide reliable access as needed. [20]
“The destruction of certain information is referred to in information security as a violation of its availability.” [21]
The Decree on Cybersecurity in Appendix 1 also represents a scale for assessing availability.
|
Level |
Description |
Examples of asset protection requirements |
|
Low |
Disruption of asset availability is not important and in the event of an outage, a longer period of correction is usually tolerated (approximately up to 1 week). |
Regular backups are sufficient to protect availability. |
|
Medium |
Disruption of asset availability should not exceed a working day, a longer-term outage leads to a possible threat to the legitimate interests of an obligor. |
Common backup and recovery methods are used to protect availability. |
|
High |
Disruption of asset availability should not exceed a period of several hours. Any failure must be addressed immediately as it leads to a direct threat to the legitimate interests of an obligor. Assets are considered to be very important. |
Backup systems are used to protect availability, and the resumption of service provision may be conditional on operator intervention or the exchange of technical assets. |
|
Critical |
Disruption of asset availability is not permissible and even short-term unavailability (in the order of several minutes) leads to a serious threat to the legitimate interests of an obligor. Assets are considered to be critical. |
Backup systems are used to protect availability, and the resumption of service provision is short-term and automated. |
The CIA triad is often represented visually to better understand its individual attributes and relationships. For this reason, too, a typical depiction of the CIA triad is shown here. In the next part of this chapter, this triad is supplemented by certain elements (technology, people, processes).
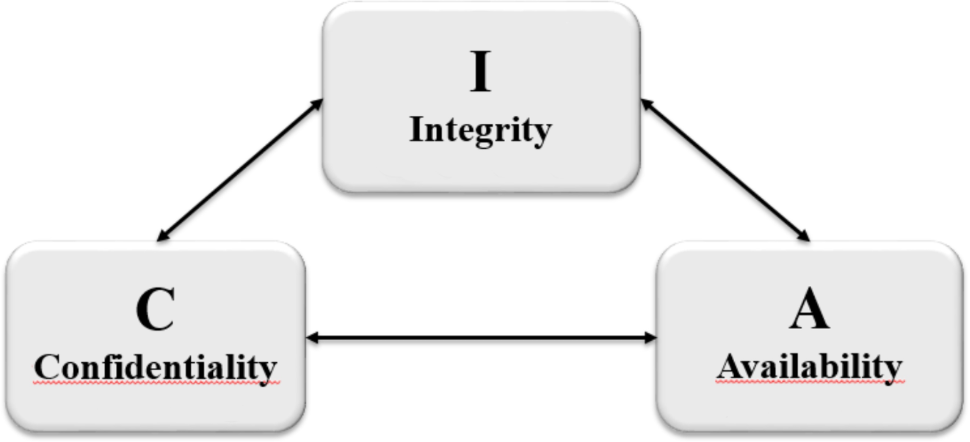
The CIA Triad
If we tried to define the space of cybersecurity within the implementation of the CIA triad, then this space could be displayed as an intersection of individual principles of this triad.
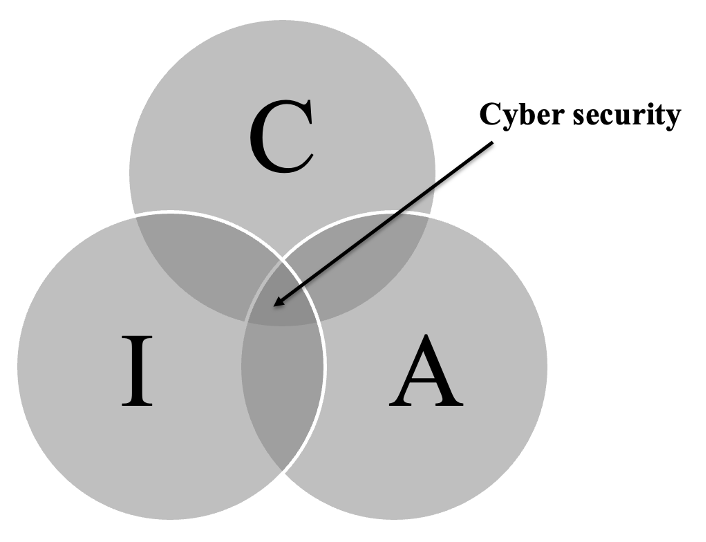
CIA triad and cybersecurity
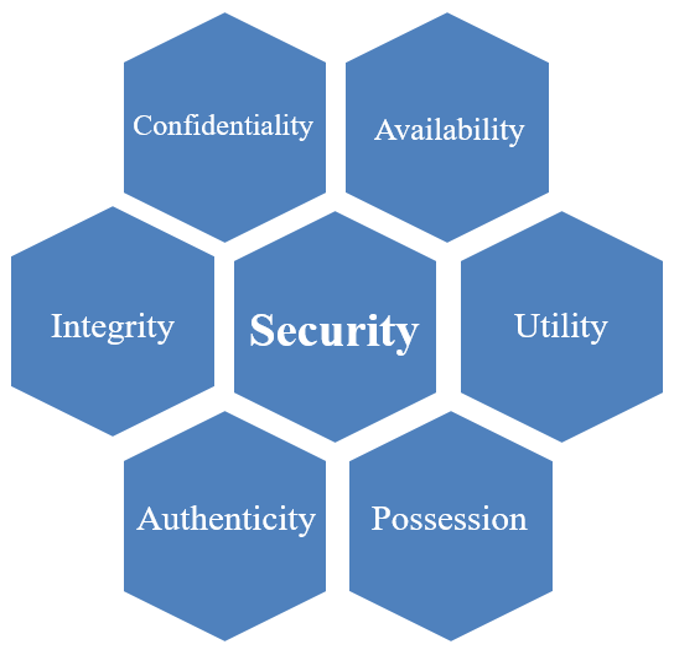
Parkenian hexad view[22]
1.2.2 Elements of cybersecurity
The following three elements, or their mutual interaction, make it possible to create or establish cybersecurity to a certain extent. These elements are:
- people,
- technologies and
- processes.
We believe that it is utopian to think that it is possible to create absolute cybersecurity or an absolutely secure system in which elements of ICT are used.
Theoretically, it would be possible to conceive of a completely isolated computer system (including a power supply, e.g. by means of an aggregate), enclosed in a Faraday cage, with a clearly defined group of people who are authorised to work on this computer system, ensuring no media (electronic or otherwise) is brought into or removed from this unique environment.
However, the question is what purpose a system secured in this way would serve and how the results of work on this system would be used, or how these results could be brought to life when it is not possible to bring the results of the activity. The counter-argument could then be the claim that the results will be delivered only at the end of the project, until then everything will be protected and access will be subject to the above-mentioned regime.
However, the question is whether such an artificially created and completely isolated system is protected against other threats, which may be the absence of backups, the possibility of physical destruction of the computer system, disclosure of partial information by people working with the system, etc.
Any system is as safe as its weakest link (element).
People
"People often represent the weakest link in the security chain and are chronically responsible for the failure of security systems.”
Bruce Schneier [23]
People interacting with cybersecurity can be seen as:
- the author (creator) of this security (i.e. typically persons who try to enforce and implement individual elements of cybersecurity, either in relation to themselves or in relation to the organisation),
- recipients of cybersecurity rules (i.e. persons who have decided or are forced to implement existing cybersecurity rules),
- entities that need to be protected against cyberattacks,
- entities that need to be informed and trained on the rules and principles of cybersecurity,
- a risk or threat to the creation and maintenance of cybersecurity.
If we focus on the role of people in building and maintaining cybersecurity, especially in connection with the AoCS, then it is necessary to define and staff the following positions in an appropriate manner:
- Cybersecurity Committee,
- Cybersecurity Manager,
- Cybersecurity Architect,
- Cybersecurity Auditor,
- Cybersecurity Team,
- Guarantor,
- of primary assets,
- of ancillary assets,
- Factual Administrator,
- Technical Administrator,
- Operator (sometimes also referred to as the supplier),
- Administrator,
- User.
People are a key element of any security. In the case of cybersecurity, their role is intensifying, and typically people are the weakest element and at the same time the most common target of attackers.
There are several reasons that lead us to this statement.
The first is the relatively short time we have actually been using computer systems. Most users started using one of the computer systems only after 1990. We started to connect to the Internet more on a large scale around 1995, and we have been using “smart” mobile phones since about 2007. A number of social network sites, which are currently considered a necessary part of life, without which we can't imagine our daily activities, haven't been used by us for more than 10 years.
The second reason lies in the enormous dynamics of the development of both hardware and especially software, which is inextricably linked to our interaction in the digital world. It is the dynamics of software development that do not allow many users to address in more detail the security issues that are inevitably associated with the use of software.
The third and last reason is the fact that life without information and communication technologies is now inconceivable or impossible for our society. ICT and applications associated with these technologies create digital avatars of ourselves, but with a much larger amount of information than we, as individuals, are able to remember or store. In addition to hardware and software vendors, attackers are aware of this fact, and it is for this reason that they are targeting people in cyberspace.
“Amateurs hack systems, professionals hack people.”
Bruce Schneier [24]
In our opinion, it is essential that people who use ICT and choose to interact in cyberspace:
- understand at least the basic principles and rules relating to cybersecurity,
- understand at least the basic functions of computer systems (e.g. PC, laptop, mobile phone, smart TV, etc.) that they use for this interaction,
- analyse the applications that they use for this interaction and, if necessary, if the activity of these applications or their contractual conditions do not suit them, they did not use the applications,
- educate themselves in cybersecurity.
Therefore, in order to facilitate at least the last item from the above list, we decided to create this publication and summarise at least some of the findings that can be used by both lay users and IT professionals who have decided to pay increased attention to cybersecurity.
Technologies
„If you think technology can solve your security problems, then you don't understand the problems and you don't understand the technology.“
Bruce Schneier [25]
Technologies are usually a means for users to connect to the Internet, social media, and other applications. It is a tool that uses various office packages when creating documents, sends e-mails, checks video, etc. The average user usually perceives and interacts with end technologies (PC, tablet, mobile phone, etc.), which they themselves use, while they are usually not interested in other the technological layers that are necessary for its operation in cyberspace.
For organisations, technologies represent a whole range of devices from technologies intended for users (desktop, mobile devices, etc.), through a complete network infrastructure (LAN, active elements, Wi-Fi elements, etc.) and services (servers, applications, etc.), to elements that serve to ensure security both on the perimeter (firewall [26] , IDS/IPS [27] , honeypot [28] , etc.) and within the infrastructure (elements designed for authentication and authorisation, monitoring, analysis, etc.).
As part of building and maintaining cybersecurity, it is necessary to analyse existing assets and, on the basis of this analysis, possibly supplement or modify existing systems. Within technologies, the following elements should be an integral part of an ICT organisation, taking into account the specifics of that organisation:
- detection systems – Intrusion Detection System (IDS) / Intrusion Prevention System (IPS),
- central administration of users and roles,
- centralised management of information classification,
- protection against malicious code (application firewall, antivirus, antispam and other solutions),
- technology for recording the activities of individual elements of ICT, administrators and users (log system),
- active and offline backup systems; backups of vital servers, applications and databases (recovery system),
- network security management (VLAN, DMZ, firewall, etc.).
Technologies are usually the part of cybersecurity where we, as users or organisations, do not save money. We are willing to pay a large part of the funds for technology, either because we “need the latest phone” or because of a real and justified reason based on obsolescence and further non-support (updating) of the computer system.
Therefore, in order to ensure cybersecurity, it is necessary to keep technologies in such a state that they are able to respond to the changes associated with the development of ICT. In particular, technologies (both hardware and software) should be kept up to date and secure.
Although technologies are certainly an important part of the process of creating and maintaining cybersecurity, they are, in our opinion, the least important part. Much more important elements of cybersecurity are appropriately set up processes and people who can apply or modify the given processes in practice and follow pre-agreed rules.
Processes
„The mantra of any good security engineer is: ‚Security is a not a product, but a process.‘ It's more than designing strong cryptography into a system; it's designing the entire system such that all security measures, including cryptography, work together.“
Bruce Schneier [29]
Processes are activities that need to be done in order for people and technologies to be able to use them.
In terms of the passage of time, it is possible to monitor the processes of:
- asset and risk management,
- definition and categorisation of assets,
- risk analysis and categorisation,
- implementation of ICT and applications,
- user and role management,
- authorisation and authentication,
- maintenance (updating) of systems and services,
- security testing of individual computer systems and services,
- analysis of corrective measures,
- implementation of corrective measures,
- cybersecurity audit,
- detection of anomalies or cyberattacks,
- response to cyberattacks or other incidents,
- processes to ensure continuity,
- training and exercises, etc.
The above list of individual processes associated with the creation and maintenance of cybersecurity is certainly not exhaustive, and the outlined processes can be granularised. Individual processes are implemented within the entire life cycle of ICT, information, data and in relation to users. [30]
The actual setting of processes, their constant maintenance or modification is the most demanding part of building cybersecurity. At the same time, this activity places the highest demands on the administrators of individual systems.
If the organisation decides to implement the rules of cybersecurity, then it is of course appropriate to keep the hardware and software up to date, follow the rules that are set for access to individual systems, etc.
If possible, it is advisable to perform simulations of typical cyberattacks in the organisation (e.g. phishing, business e-mail compromise, etc.) in order to realistically demonstrate these attacks and possible impacts if a person falls victim to such attacks.
Penetration testing also allows you to find errors in already set processes.
However, when creating and setting cybersecurity rules, the organisation should primarily focus on human resources and their education.
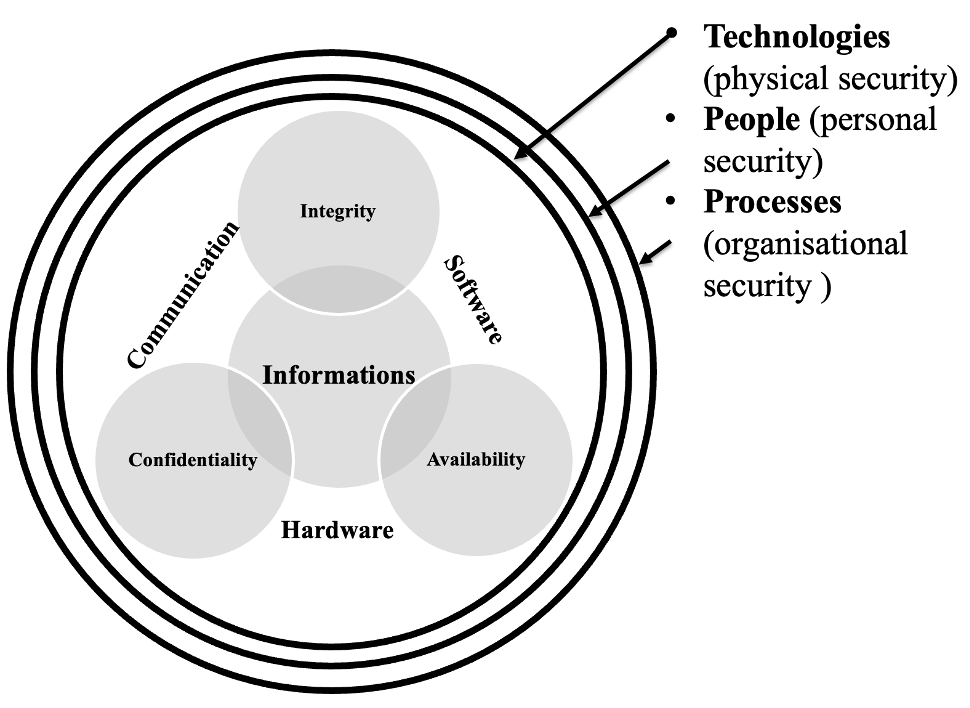
CIA triad supplemented by technologies, people and processes[31]
1.2.3 Cybersecurity life cycle
From the point of view of the passage of time, it is necessary to apply or modify both the CIA triad and partial elements of cybersecurity during the entire life cycle in the implementation of cybersecurity. In particular, it is about prevention, detection and reaction to the attack. [32]
Very often, the cybersecurity life cycle is represented by various diagrams. For clarity, I present some of them.
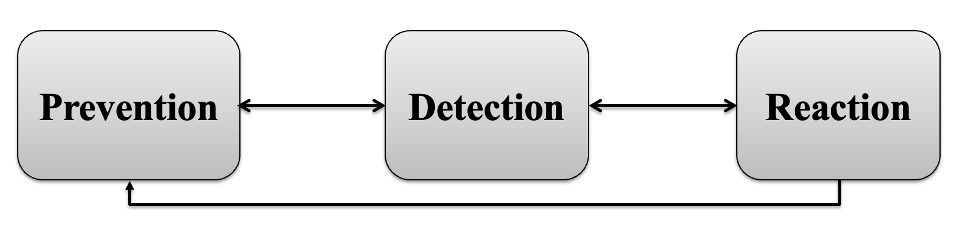
Simplified representation of the cybersecurity life cycle
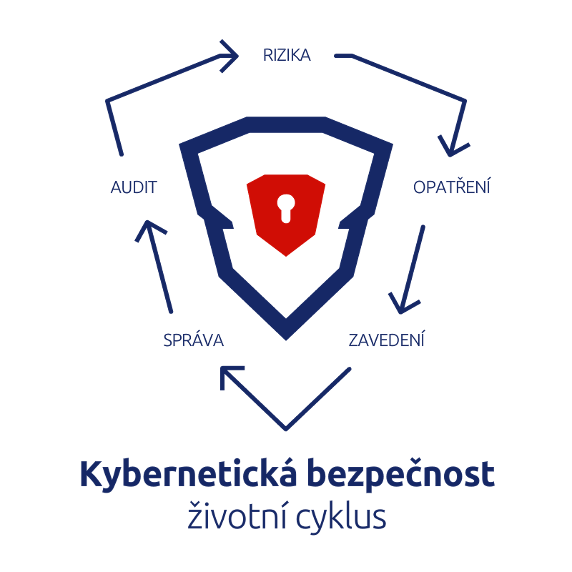
Cybersecurity life cycle according to kybez.cz [33]
Text on the figure: Cybersecurity – life cycle
ADMINISTRATION – AUDIT – RISKS – MEASURES – IMPLEMENTATION
When dealing with cybersecurity, there is no “point of reference” within which it could be said: “We made it! We are protected against cyberattacks or threats. We are cybernetically secure.”
Building and maintaining cybersecurity can be compared to a never-ending risk analysis, but this routine analysis needs to be complemented by other support processes that can help increase cybersecurity in the organisation.
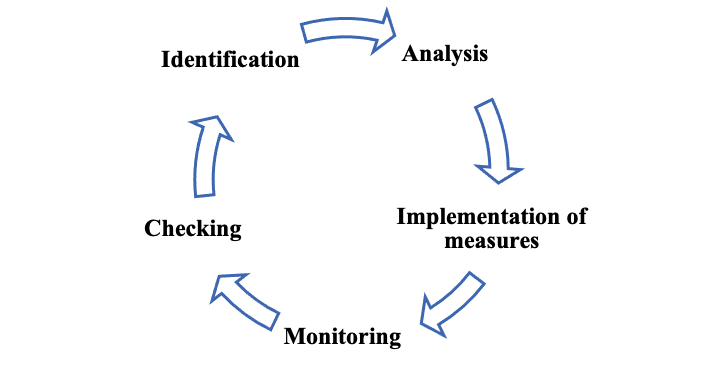
Risk analysis

Cybersecurity life cycle
The actual depiction of the cybersecurity life cycle can be much more complex. [34]
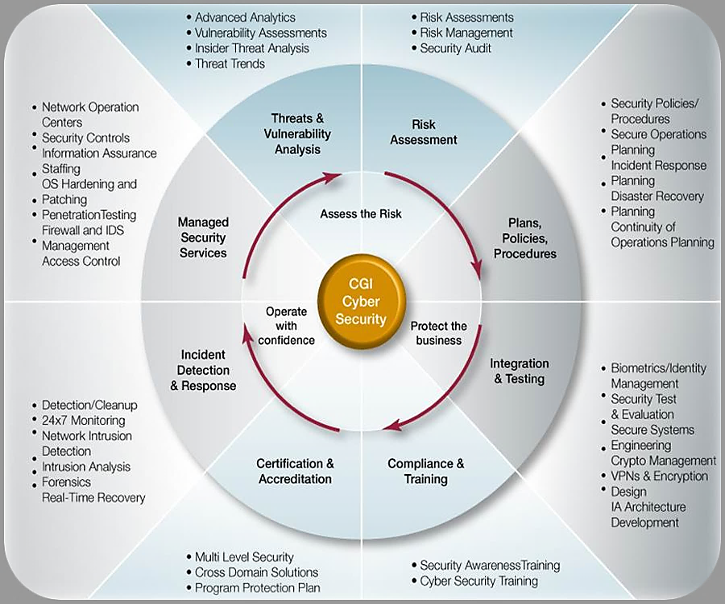
Example of cybersecurity solution
Evolution of cybersecurity
At the end of this subchapter, it would be possible to ask a simple question: “Why should I (as an individual) or an organisation deal with cybersecurity at all?”
The answer will not be so complicated, although it will be necessary to dispel the often ingrained myth that someone else, whether large organisations such as Microsoft, Google, Apple or providers of cloud services, connectivity, etc., is already addressing the issue of cybersecurity for me.
It is true that these organisations have introduced and applied sub-elements of cybersecurity, but cybersecurity, like any other security, always begins and ends with a specific person or organisation that wants to secure itself, always with regard to the specifics of that person or organisation.
The following facts emerge from the Data Breach Investigations Report [35] for 2017, which deals with security breaches leading to data compromise:
- the attacker was
· a person outside the organisation – 73%
· a person within the organisation – 28%
· an organised crime group – 50%
- a method of the attacks was:
· hacking – 48%
· malware – 30%
o 49% of the malware was distributed by an attacker and subsequently installed via e-mail
· social engineering – 43%
· physical attack – 8% [36]
- victims are organisations operating in:
· healthcare – 24%
· public sector (typically state administration and self-government, etc.) – 14%
- motive of attack:
· enrichment – 76%
· gain of data and information (espionage) – 13%
- 68% of attacks were detected only after several months or after a longer period
The following graph presents the development of individual attacks from 2010 to the end of 2017.

Types of attacks used to compromise security [37]
According to a report by the National Cyber and Information Security Agency, [38] “a further increase in cyberthreats can be expected in 2018, especially further next-generation phishing attacks, attacks on markets, wallets and cryptocurrency exchanges, file-free variants of ransomware, use of artificial intelligence for cyberattacks, data attacks in Cloud solutions, attacks on the Internet of Things, industrial systems, etc. The share of state or state-supported actors in cyberattacks is expected to increase, and massive leaks of personal data, passwords and access data will continue. That is why it is necessary to build the cybersecurity of information and communication systems important for the operation of the state and its critical infrastructure." [39]
The area of cybersecurity will be one of the most important areas in the future as it can be assumed that the use of ICT and services related to these technologies will not be reduced. Cybersecurity is intended to help identify gaps in the setup of these systems and services.
“Cybersecurity also helps identify, assess and address threats in cyberspace, reduce cyber risks and eliminate the impact of cyberattacks, information crime, cyberterrorism and cyber espionage by strengthening the confidentiality, integrity and availability of data, systems and other information and communication infrastructure elements.
The main purpose of cybersecurity is the protection of the environment to enforce human information rights.” [40]
[1] See e.g. HSU, D. Frank and D. MARINUCCI (eds.). Advances in cybersecurity: technology, operations, and experiences. New York: Fordham University Press, 2013. 272 p. ISBN 978-0-8232-4456-0. p. 41.
KADLECOVÁ, Lucie. Konceptuální a teoretické aspekty kybernetické bezpečnosti. [online]. [cit. 21/07/2018]. Available from: https://is.muni.cz/el/1423/podzim2015/BSS469/um/Prezentace_FSS_Konceptualni_a_teoreticke_aspekty_KB.pdf
[2] For more details, see e.g. Parkerian Hexad. [online]. [cit. 20/08/2016]. Available from: https://vputhuseeri.wordpress.com/2009/08/16/149/
[3] Article 1 (b) of the Convention on Cybercrime. Convention on Cybercrime. [online]. [cit. 20/08/2016]. Available from: https://rm.coe.int/CoERMPublicCommonSearchServices/DisplayDCTMContent?documentId=09000016804931c0
[4] POŽÁR, Josef. Informační bezpečnost. Plzeň: Aleš Čeněk, 2005, p. 25
[5] For more details, see WIENER, Norbert. Kybernetika: neboli řízení a sdělování v živých organismech a strojích. Prague: Státní nakladatelství technické literatury, 1960. 148 p., p. 32 et seq.
[6] ŠÁMAL, Pavel et al. Trestní zákoník II. § 140 až 421. Komentář. 2. Publ. Prague: C. H. Beck, 2012, p. 2308
[7] POŽÁR, Josef. Informační bezpečnost. Plzeň: Aleš Čeněk, 2005, p. 25
[8] For more details see: KOLOUCH, Jan. CyberCrime. Prague: CZ.NIC, 2016, p. 57 et seq.
[9] For more details, see e.g. EVANS, Donald, Philip, BOND and Arden BEMET. Standards for Security Categorization of Federal Information and Information Systems. National Institute of Standards and Technology, Computer Security Resource Center. [online]. [cit. 10/12/2017]. Available from: https://csrc.nist.gov/csrc/media/publications/fips/199/final/documents/fips-pub-199-final.pdf
ANDRESS, Jason. The Basics of Information Security. 2nd Edition. Syngress. ISBN: 9780128007440
HENDERSON, Anthony. The CIA Triad: Confidentiality, Integrity, availability. [online]. [cit. 13/01/2018]. Available from: http://panmore.com/the-cia-triad-confidentiality-integrity-availability
[10] For more details, see https://www.nbu.cz/cs/pravni-predpisy/zakon-c-412-2005/1122-uplne-zneni-zakona-c-412-2005/
[11] See also: ŠULC, Vladimír. Kybernetická bezpečnost. Plzeň: Aleš Čeněk, 2018. p. 20 et seq.
[12] Currently the Center for Protection of National Infrastructure – CPNI
[13] For more details, see e.g. Traffic Light Protocol (TLP) Definitions and Usage. [online]. [cit. 13/01/2018]. Available from: https://www.us-cert.gov/tlp
[14] Traffic Light Protocol (TLP) Definitions and Usage. [online]. [cit. 13/01/2018]. Available from: https://www.us-cert.gov/tlp
[15] ŠULC, Vladimír. Kybernetická bezpečnost. Plzeň: Aleš Čeněk, 2018. p. 19
[16] Hereinafter referred to as the Decree on Cybersecurity or DoCS.
[17] JIRÁSEK, Petr, Luděk NOVÁK and Josef POŽÁR. Výkladový slovník kybernetické bezpečnosti. [online]. 3rd updated edition. Prague: AFCEA, 2015, p. 58. [online]. [cit. 10/07/2018]. Available from: http://afcea.cz/wp-content/uploads/2015/03/Slovnik_v303.pdf
[18] ŠULC, Vladimír. Kybernetická bezpečnost. Plzeň: Aleš Čeněk, 2018. p. 22
[19] JIRÁSEK, Petr, Luděk NOVÁK and Josef POŽÁR. Výkladový slovník kybernetické bezpečnosti. [online]. 3rd updated edition. Prague: AFCEA, 2015, p. 43. [online]. [cit. 10/07/2018]. Available from: http://afcea.cz/wp-content/uploads/2015/03/Slovnik_v303.pdf
[20] See e.g. EVANS, Donald, Philip, BOND and Arden BEMET. Standards for Security Categorization of Federal Information and Information Systems. National Institute of Standards and Technology, Computer Security Resource Center. [online]. [cit. 10/12/2017]. Available from: https://csrc.nist.gov/csrc/media/publications/fips/199/final/documents/fips-pub-199-final.pdf
[21] ŠULC, Vladimír. Kybernetická bezpečnost. Plzeň: Aleš Čeněk, 2018. p. 24
[22] The Parkerian Hexad. [online]. [cit. 20/08/2016]. Available from: http://cs.lewisu.edu/mathcs/msisprojects/papers/georgiependerbey.pdf
[23] SCHNEIER, Bruce. [online]. [cit. 18/07/2018]. Available from: https://www.azquotes.com/quote/570039
[24] SCHNEIER, Bruce. [online]. [cit. 18/07/2018]. Available from: https://www.azquotes.com/quote/570035
[25] SCHNEIER, Bruce. [online]. [cit. 18/07/2018]. Available from: https://www.azquotes.com/quote/570040
[26] A firewall is a system containing rules that govern data flows within network technologies.
[27] IPS (Intrusion Prevention System), a device that monitors unwanted (malicious) network activity and/or computer system activity. Hereinafter referred to as the IPS.
IDS (Intrusion Detection System) is a system designed to detect unusual activities that can potentially lead to breaches of security of computer networks, computer systems, applications, etc. Hereinafter referred to as the IDS.
[28] A honeypot is a system the purpose of which is to detect malware or other unwanted activities, which are then analysed in this artificial environment.
[29] SCHNEIER, Bruce. [online]. [cit. 18/07/2018]. Available from: https://www.azquotes.com/quote/570047
[30] The term “user” is used here to express a natural person who is authorised to use elements of ICT, individual systems and applications. From this point of view, the user means both a person with administrator rights and an end user.
[31] The graph was based on the graph published in: CIA triad methodology. [online]. [cit. 10/07/2018]. Available from: https://en.wikipedia.org/wiki/Information_security#/media/File:CIAJMK1209.png
[32] For more details, see SVOBODA, Ivan. Řešení kybernetické bezpečnosti. Přednáška v rámci CRIF Academy. (23/ 09/2014)
[33] Základní pojmy. [online]. [cit. 10/07/2018]. Available from: https://www.kybez.cz/bezpecnost/pojmoslovi
[34] The complete breadth of CGI Cyber Security services. [online]. [cit. 10/07/2018]. Available from: https://mss.cgi.com/service-portfolio
[35] 2018 Data Breach Investigation Report. 11th Edition. [online]. [cit. 28/07/2018]. Available from: http://www.documentwereld.nl/files/2018/Verizon-DBIR_2018-Main_report.pdf
[36] Techniques and tools are usually combined as a part of individual attacks.
[37] 2018 Data Breach Investigation Report. 11th Edition. [online]. [cit. 28/07/2018]. Available from: http://www.documentwereld.nl/files/2018/Verizon-DBIR_2018-Main_report.pdf p. 7
[38] Národní úřad pro kybernetickou a informační bezpečnost. Hereinafter referred to as the NUKIB
[39] Zpráva o stavu kybernetické bezpečnosti za rok 2017. [online]. [cit. 29/06/2018]. Available from: https://nukib.cz/download/Zpravy-KB-vCR/Zprava-stavu-KB-2017-fin.pdf
[40] Národní strategie kybernetické bezpečnosti České republiky na období let 2015 až 2020. [online]. [cit. 01/07/2018]. Available from: https://www.govcert.cz/download/gov-cert/container-nodeid-998/nskb-150216-final.pdf




