Laws and regulations governing cybersecurity
7. Privacy and security in ICT, data protection in cyberspace
7.2. Terms of Service (EULA)
In the next part of this chapter, I will try to describe what information about users is collected by default by the largest ISPs.[1] I specifically chose Google Inc. because I believe there are a tiny number of users who would never use one of Google’s products (such as OS Android, the search engine on www.google.com, Gmail, Google Chrome, etc.).[2] My goal is by no means to “attack” Google Inc. or other companies (including their products). The purpose is to present the possible security risks that are associated with the use of certain services provided and with the acceptance of the Terms of Service (EULA – End Users Licence Agreement), to which the use of these services is bound.
The Terms of Service enabling the use of a service of a given service provider are, in essence, nothing more than a generally unilaterally established definition of rights and obligations by the service provider (ISP). However, a user is not limited in any way in his/her rights as he/she has the option of not using such unilaterally set terms of service. In the case of consent to the use of such services, it is generally possible to state that private law standards will be applied primarily.
The question is whether a user is really aware of what Terms of Service he/she has agreed to, when they become binding on him/her and what possible (legal) interference with his/her fundamental human rights and freedoms is such consent. Another important fact is that the service provided in this way may affect the rights and legitimate interests (e.g. IT security, trustworthiness of data, etc.) of third parties (e.g. employers, etc.) who have not explicitly agreed to use the service.
Theoretically, it can be stated that a private law contract with this company for the entire period of its existence has been entered into by almost 3 billion users.[3] The sad fact remains that a very small percentage of users are willing to read the Terms of Service relating to a service provided.[4]
Excerpts from Google Inc. Terms of Service[5]
Google explicitly states that if any user begins to use any Google services, they agree to the applicable terms of service. It further clearly defines the relationship between a user and itself, as a service provider, in the event that the user is obliged to accept other terms of service. This relationship is expressed as follows: “Our range of services is wide, and some may be subject to additional conditions or requirements (including age restrictions). Additional terms will be available along with applicable services. If you use these services, the additional terms of service become part of the contractual arrangements between the two parties.”
In the introduction to the Terms of Service, Google states that: “We may review content[6] to determine whether it is legal and in compliance with our policies and if we believe that it violates our policies or laws, we may remove or prevent the content from appearing. Please note that the above does not mean that we review content.”
From the point of view of security, in my opinion, an essential part of the Terms of Service is the section dealing with the protection of personal data and copyright.[7] In this section, Google defines what information it collects about users and how it handles it. The following information is crucial from a security and “anonymity” perspective. I believe that declaring that the following information is collected “so that we can provide a better service to all our users – from identifying simple things like the language you speak to more complex things, such as ads that will be most useful to you, the people you are most interested in on the web or which YouTube videos you might like,” may be commendable but at least startling. The comparison with the already mentioned Minority Report in the form of advertising targeting is more than obvious after such a statement. Furthermore, Manfred Spitzer and Digital Dementia again spring to mind because, over time, it is no longer me who decides what I will watch or what I will search for (or all the relevant responses may not and are not offered to me).
Google collects user information in basically two ways:
Information disclosed by a user. Typically these are:
Name, email address, phone number or credit card.
Information obtained through the use of Google services. It involves the collecting of information about the services that a user uses, including how they are used (“for example, when you watch a video on YouTube, visit websites that use our advertising services or watch or respond to our ads and content”). According to Google, these are:
- Device information (e.g., hardware model, operating system version, unique device identifiers[8] and mobile network information, including the phone number). Google reserves the right to assign your device identifiers or your phone number to your Google user account
- Protocol information:
- details of how a user used a Google service,
- information from the call protocol (e.g. phone number, caller number, divert numbers, time and date of calls, call duration, SMS routing data and call types),
- Internet Protocol address
- information about device events (e.g., failure, system activity, hardware settings, browser type, browser language, date and time of your request, or referring URL),
- cookies, which can be unique identifiers of your browser or Google account.
- Location information. Google may collect and further process information about the actual location of its user. Google can determine your location using a variety of technologies, such as IP address, GPS and other sensors that can provide Google with information about nearby devices, Wi-Fi hotspots and mobile network transmitters.
- Unique application numbers. Typically, this is a licence number and type (version) of an applicable installed software product. The Terms of Service do not imply that unique application numbers are recorded only from devices whose primary operating system is Android. It can therefore be concluded that, if Google services are used, then information about unique application numbers is also collected from other operating systems (iOS, Linux, Windows, etc.).
- Local storage. Under the Terms of Service, Google may: “collect and store information (including personal information) in your device’s local storage.” In this case, too, the same conclusion can be reached as for unique application numbers.
In my opinion, the possibility of misuse of such stored data by an attacker is also a threat to users. Information (which is typically packaged on cookies, etc.) stored in a user’s local storage can also become an appealing target for an attacker because it is from this information that it is possible to determine, for example, patterns of user behaviour.
- Cookies and similar technologies. “When you visit a Google service, we and our partners use a variety of technologies to collect and store information. This may include, but is not limited to, the use of cookies or similar technologies to identify your browser or device. We use these technologies to collect and store information even when you use services we offer to our partners, such as advertising services or Google features that may appear on other websites.”
What information do apps running on Android OS collect:
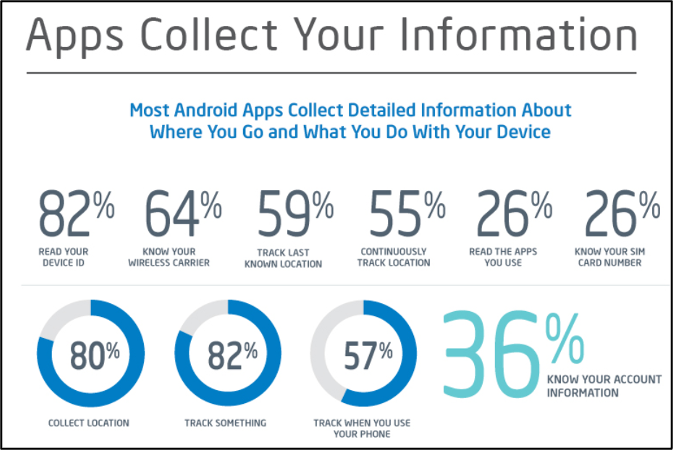
Google may continue to use this information based on the agreed Terms of Service. Among other things, Google is authorised to analyse content (including emails) using automated systems. It is also entitled to combine personal data from one service with information and personal data from another service (using Google).
Handling of the mentioned information then means its sharing, either with the user’s consent or without this consent.[11] The Service of Terms enable sharing for external processing and for legal reasons:
“We provide personal information to our affiliates or other trusted businesses or persons to process it for us, based on our instructions and in compliance with our Privacy Policy and any other appropriate confidentiality and security measures.
“We share personal information with companies, organizations or individuals outside of Google if we have a good-faith belief that access, use, preservation, or disclosure of the information is reasonably necessary to:
- meet any applicable law, regulation, legal process, or enforceable governmental request,
- enforce the applicable Terms of Service, including investigation of potential violations,
- detect, prevent, or otherwise address fraud, security, or technical issues,
- protect against harm to the rights, property or safety of Google, our users, or the public as required or permitted by law.”
However, from a security and anonymity perspective, I consider the following section of the Terms of Service that deals with user content on the services provided by Google to be probably the most problematic:
“By uploading, submitting, storing or receiving content to or through our Services, you grant Google (and its partners) a worldwide license to use, host, store, reproduce, modify, create derivative works (for example, those that are of the translation, adaptation or other changes that we make so that your content is better adapted to our Services)[12], communicate, publish, perform or publicly display and distribute of said content.…. This license will remain in effect even when you stop using our Services (e.g. business listing added to Google Maps). Some services allow you to access or remove content that you have submitted to the service…. “
Personally, I believe that at least in this part of the Terms of Service, the imaginary limit defining the adequacy of the information collected about individual users has been exceeded. This section is, in fact, about a “legal use” of any content that Google “interacts with”. Personally, I believe that it is the interference with the content of, for example, transmitted information that should be a last possible resort, and not a kind of “matter of course” enshrined in the contract.
[1] For this part of the text, the theses that were used were published in the article: KOLOUCH, Jan. Pseudoanonymita – bezpečnostní riziko pro uživatele Internetu. DSM – data security management [online]. 2015. Vol. 19, No. 3, pp. 24–29 ISSN 1211-8737. Available from: http://www.tate.cz/cz/casopis/clanek/dsm-2015-3-456/
[2] It should be noted that the following companies have very similar Terms of Service (enabling them to provide information to a comparable extent): Microsoft, Apple, Facebook, etc.
[3] According to the article SMITH, Craig. By the Numbers: 100 Amazing Google Search Statistics and Facts. [online]. [cit. 04/08/2016]. Available from: http://expandedramblings.com/index.php/by-the-numbers-a-gigantic-list-of-google-stats-and-facts/, there are 100 billion searches per month through Google search.
[4] And according to one participant in the Security 2015 conference, a normal person would spend about 10–20 years of their life reading all the constantly changing Terms of Service.
[5] Hereinafter referred to as the Google. All excerpts from the Terms of Service were drawn from: Smluvní podmínky společnosti Google. [online]. [cit.14/06/2016]. Available from: https://www.google.cz/intl/cs/policies/terms/regional.html
[6] Content means content (data) that does not belong to Google. The entity that published it is responsible for the content.
[7] Specifically then Zásady ochrany osobních údajů. [online]. [cit.14/06/2016]. Available from: https://www.google.cz/intl/cs/policies/privacy/
[8] Google definition. Unique device identifier. [online]. [cit.14/06/2016]. Available from: https://www.google.cz/intl/cs/policies/privacy/key-terms/#toc-terms-unique-device-id
“A unique device identifier (sometimes called a universally unique ID or UUID) is a string of characters that is encoded into the device by the manufacturer and is used to uniquely identify the device (for example, the IMEI of a mobile phone). Different device identifiers differ depending on whether they are permanent, whether users can reset them and how they can be accessed. A given device can contain several different unique identifiers. Unique device identifiers can be used for a variety of purposes, such as security, fraud detection, synchronisation of services such as inbox, or to store user settings and provide relevant ads.”
[9] According to the required function, it will be mainly about storing information and data in the folder of the given browser (web browser), but according to the contractual conditions, it can also be applications other than a web browser.
[10] CAETANO, Lianne. Are Your Apps Oversharing? 2014 Mobile Security Report Tells All. [online]. [cit.10/04/2015]. Available from: https://blogs.mcafee.com/consumer/mobile-security-report-2014/
[11] E.g. with domain administrators; for external processing or for legal reasons.
[12] It is understandable that Google attempts, for example, to translate works, pages or other content so that even a user who does not know the original language of the work can read it. However, in absurd cases, it is possible to imagine the publication of your private love poem that you sent using one of the Google services, your photo, your brilliant idea for a perpetual-motion machine, etc.
