Laws and regulations governing cybersecurity
5. Information Security Management System
5.1. ISMS framework
The Information Security Management System (ISMS)[1] is a set of rules designed to maintain the confidentiality, integrity and availability of information by applying a risk management process and providing assurance to stakeholders that risks are being adequately managed.[2]
Within the ISMS, assets are protected, information security risks are managed and measures already in place are checked.
Information security management system means such a part of the management system that is based on the approach to risks of the information and communication system. This part of the management system defines how to establish, implement, operate, monitor, review, maintain and improve the security of information and data.
It is also clear from the above definition that the ISMS is a part of processes and the overall management system of an organisation as well as being integrated into these systems.
ISMS can be applied to an organisation as a whole, as well as to an organisational unit within the organisation, or to a specifically designed information and communication system, or part thereof.
“ISMS can be implemented and used in an organisation with ten employees, as well as in a large holding company that can have thousands of employees. Simply put, there is only one ISMS, the one described in ISO/IEC 27001. However, the interpretation and implementation of individual recommendations can vary significantly depending on the scope of the system, the number of users, the way data are processed, their value and especially according to real security risks, etc. The ISMS strategy in small and medium-sized companies is not described in as much detail as is customary in large, especially multinational organisations.
The ISMS does not only apply to industrial enterprises and private organisations, the ISMS applies to all organisations, including public law institutions and state bodies. This is demonstrated by the existence of many national governmental and departmental resolutions recommending or requiring the implementation of ISMS in organisations managed and established by the state.”[3]
Many ISMS standards are designed to help organisations of all types and sizes implement and operate ISMS. It consists of the following international standards, collectively referred to as (Information Technology – Security Technologies[4] (listed below in numerical order):
| ISO/IEC 27000 | Information security management systems – Overview and vocabulary |
| ISO/IEC 27001 | Information Security Management Systems – Requirements |
| ISO/IEC 27002 | Code of practice for information security controls |
| ISO/IEC 27003 | Information security management systems – Guidance |
| ISO/IEC 27004 | Information security management – Monitoring,
measurement, analysis and evaluation |
| ISO/IEC 27005 | Information security risk management |
| ISO/IEC 27006 | Requirements for bodies providing audit and
certification of information security management systems |
| ISO/IEC 27007 | Guidelines for information security management systems auditing |
| ISO/IEC TR 27008 | Guidelines for auditors on information security controls |
| ISO/IEC 27009 | Sector-specific application of ISO/IEC 27001 – Requirements |
| ISO/IEC 27010 | Information security management for
inter-sector and inter-organisational communications |
| ISO/IEC 27011 | Code of practice for Information security
controls based on ISO/IEC 27002 for telecommunications organisations |
| ISO/IEC 27013 | Guidance on the integrated implementation of
ISO/IEC 27001 and ISO/IEC 20000-1 |
| ISO/IEC 27014 | Governance of information security |
| ISO/IEC TR 27015 | Information security management guidelines for financial services |
| ISO/IEC TR 27016 | Information security management — Organisational economics |
| ISO/IEC 27017 | Code of practice for information security
controls based on ISO/IEC 27002 for cloud services |
| ISO/IEC 27018 | Code of practice for protection of personally
identifiable information (PII) in public clouds acting as PII processors |
| ISO/IEC 27019 | Information security management guidelines
based on ISO/IEC 27002 for process control systems specific to the energy utility industry |
|
International Standards, which are not listed under this common name but are also part of a series of ISMS standards, are listed below: |
|
|
ISO 27799 |
Health informatics — Information security management in health using ISO/IEC 27002[5] |
The ISMS solution requires a systemic and comprehensive approach, respecting the principles and elements of the entire cybersecurity lifecycle. The ISMS management system is based on the Deming cycle, or also on the PDCA cycle (Plan-Do-Check-Act).
The PDCA cycle is one of the basic management principles based on the gradual improvement of the quality of processes, services, data, products, etc. thanks to the constant repetition of its four basic activities: Plan-Do-Check-Act.
There are currently a number of variants of the PDCA cycle[6], and one of the suitable modifications of this cycle, which is also applicable in the field of cybersecurity, is the OPDCA variant, which extends the original model by the Observe phase preceding the Plan phase.
The PDCA cycle, or some of its modifications, can be applied to all ISMS processes. The simplest way to display this model is a never-ending circle:
Figure: PDCA model[7]
The PDCA model was also expressed in ISO/IEC 27001: 2005 and illustrated how the ISMS accepts information security requirements and stakeholder expectations as an input and uses information and processes to generate information security outputs that meet those requirements and expectations.
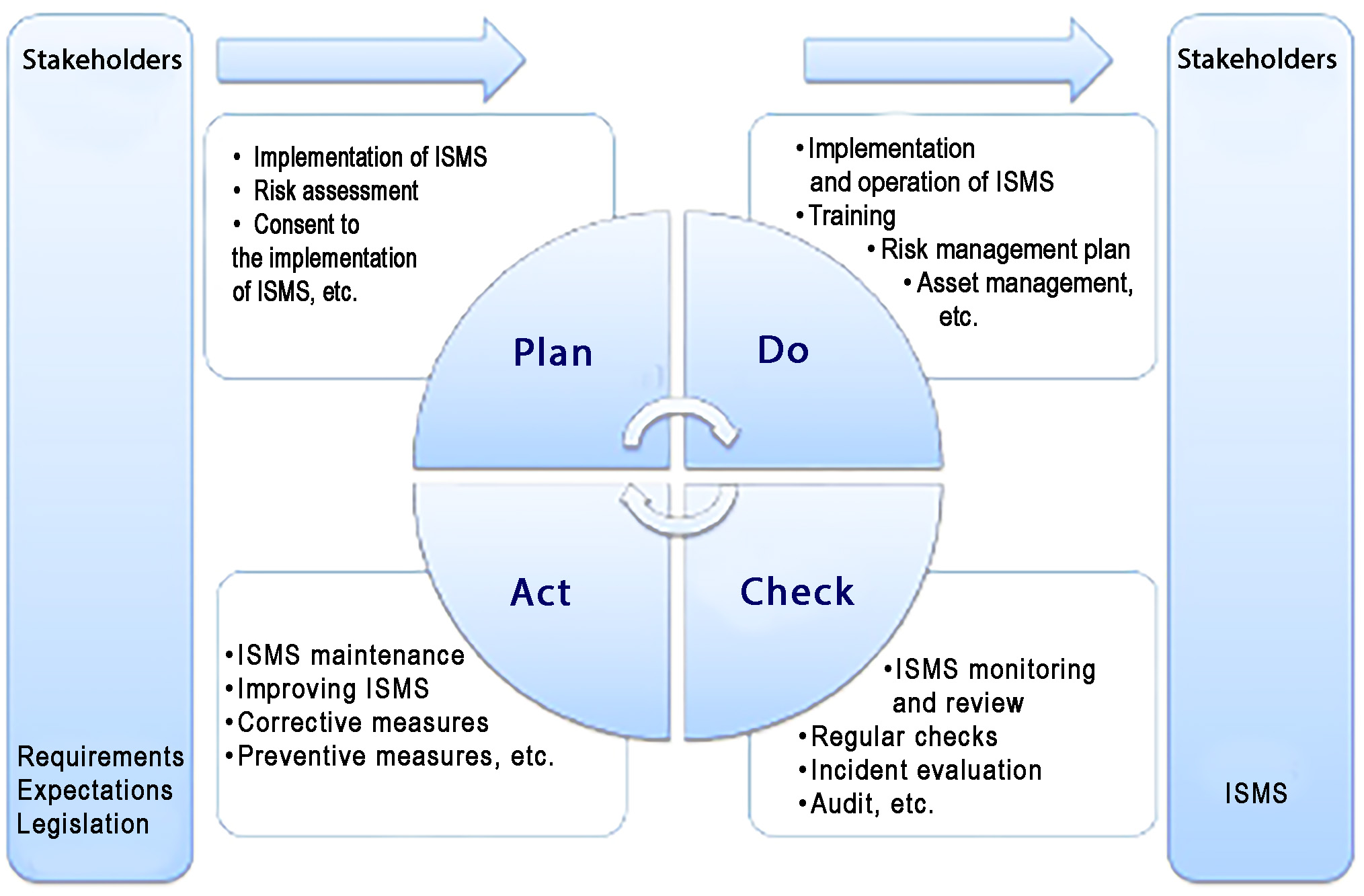
Figure: PDCA model applied to ISMS processes[8]
| Plan (ISMS establishment) | Establishment of ISMS policy, goals, processes and procedures related to risk management and information security to provide results consistent with the organisation’s overall policy and objectives. |
| Do (implementation and operation of ISMS) | Implementation and use of the ISMS policy, measures, processes and procedures. |
| Check (ISMS monitoring and review) | Assess, where possible, process performance measurement against the ISMS policy, objectives and practical experience and reporting results to organisation’s management for review. |
| Act (maintaining and improving ISMS) | Take corrective and preventive actions based on the results of the ISMS internal audit and review of the management system by organisation’s management to ensure continuous improvement of ISMS. |
The ISO/IEC 27001 standard promotes the adoption of a process approach for establishing, implementing, operating, monitoring, maintaining and improving ISMS in an organisation. Emphasis is placed especially on:
- understanding of an organisation’s information security requirements and the need to set information security policies and objectives,
- introduction and operation of measures for information security management in the context of managing the overall risks of an organisation’s activities,
- monitoring and reviewing the performance and efficiency of ISMS,
- continuous improvement based on objective measurement.
“For ISMS within an organisation, the management organisation, responsibility for information security of managers at all levels, professional bodies and roles in the information security system must be clearly described.
In the organisational structure of an organisation, information security must be taken into account so as to cover the activities and cooperation of management, persons responsible for application systems, operational services, end users and persons responsible for individual activities. Information security presupposes close cooperation of all mentioned groups of employees and provision of training in the field of information security, so that in addition to those responsible for information and other security in the organisation, information management staff and all users of information technology also have a basic knowledge of information security.”[9]
With regard to the above, it is possible to define standard goals of ISMS within an organisation:
- ensuring the security of information and communication systems and services,
- ensuring the continuity of operation of information and communication systems and services,
- data and information protection,
- protection of other assets,
- handling threats, events and incidents, including prevention,
- increasing the security of information and communication systems and services,
- raising the general awareness of users about security and security threats (education),
- sharing experiences with other entities.
However, the implementation of ISMS in an organisation cannot ensure the complete security of the organisation’s assets. However, the implementation of ISMS can significantly reduce the risks of asset encroachment to an acceptable level. The whole system is as strong as its weakest link. In this case, the weakest link, and the greatest danger to information security, is a person.
[1] Hereinafter referred to as the ISMS
[2] Cf. introduction ČSN ISO/IEC 27001
[3] POŽÁR, Josef and Luděk NOVÁK. Pracovní příručka bezpečnostního manažera. Prague: AFCEA, 2011. ISBN 978-80-7251-364-2, p. 5, or: POŽÁR, Josef and Luděk NOVÁK. Systém řízení informační bezpečnosti. [online]. [cit. 06/07/2018]. Available from: https://www.cybersecurity.cz/data/srib.pdf p. 1
[4] The common name “Information technology – Security techniques” indicates that these international standards have been prepared by the joint technical committee ISO/IEC JTC 1 Information Technologies, subcommittee SC 27 IT Security Techniques
[5] For an overview of standards, see: ČSN EN ISO/IEC 27000 (369790) – Information technologies – Security techniques – Information security management systems – Overview and vocabulary
[6] ROSER, Christoph. The Many Flavors of the PDCA. [online]. [cit. 06/07/2018]. Available from: https://www.allaboutlean.com/pdca-variants/
[7] PDCA cycle. [online]. [cit. 06/07/2018]. Available from: https://www.creativesafetysupply.com/glossary/pdca-cycle/
[8] Modified and supplemented PDCA model. The original model was introduced in ISO/IEC 27001: 2005 p. 7
[9] POŽÁR, Josef and Luděk NOVÁK. Pracovní příručka bezpečnostního manažera. Prague: AFCEA, 2011. ISBN 978-80-7251-364-2, pp. 7–8, or: POŽÁR, Josef and Luděk NOVÁK. Systém řízení informační bezpečnosti. [online]. [cit. 06/07/2018]. Available from: https://www.cybersecurity.cz/data/srib.pdf p. 2
